Get a Report of Malops and Suspicions for a Specific Time Period
As you monitor your environment, you may want to create a request that can create a summary of new Malops and associated details for these Malops to help you spot trends . You can use the API to prepare these summaries by retrieving Malops from a specific time period and extracting details.
This example shows how to retrieve Malops from the past seven days and examine some details about these Malops.
Note
This scenario applies to Cybereason versions earlier than 20.1.43 (when the Malops management screen was introduced). You can run this request in later versions, but the response for the endpoint in version 20.1.43 and later returns different data. Therefore, finding and extracting the response details is different for these versions.
In this topic:
Step 1: Build your request
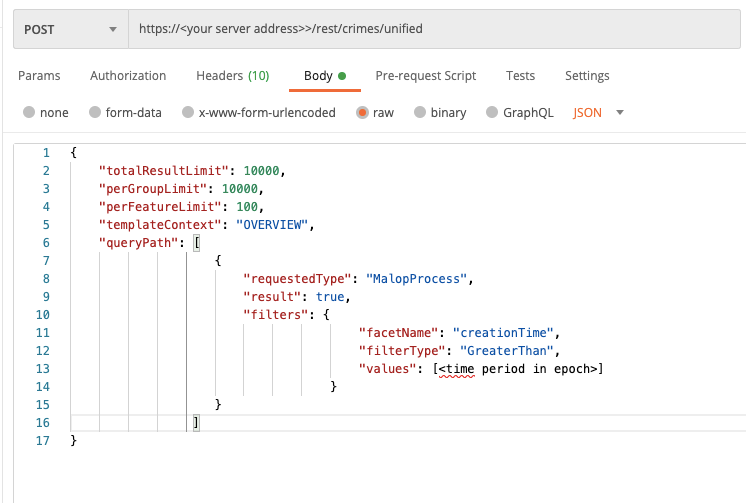
To build a request to retrieve results from a specific time period:
Determine the time period that you want.
Add a filters object with the creationTime Feature (as seen in the examples below).
Set the value of the requestedType parameter.
The Cybereason platform generates Malops on both the Process Element and the LogonSession Element. Therefore, you must run the request twice.
The first time you run the request, set this key parameter to MalopProcess. The second time you run the request, set this key parameter to MalopLogonSession.
Set the value of the time_period_start to the time, in epoch form.
Use the following cURL command, request body example, and Python script show a request to retrieve results from a specific time period:
curl --request POST \
--url http://myserver.com/rest/crimes/unified \
--header 'Content-Type:application/json' \
--data '{
"totalResultLimit": 10000,
"perGroupLimit": 10000,
"perFeatureLimit": 100,
"templateContext": "OVERVIEW",
"queryPath": [
{
"requestedType": "MalopProcess",
"result": true,
"filters": {
"facetName": "creationTime",
"filterType": "GreaterThan",
"values": [<time period in epoch>]
}
}
]
}'
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"totalResultLimit": 10000,
"perGroupLimit": 10000,
"perFeatureLimit": 100,
"templateContext": "OVERVIEW",
"queryPath": [
{
"requestedType": "MalopProcess",
"result": true,
"filters": [
{
"facetName": "creationTime",
"filterType": "GreaterThan",
"values": [<time period in epoch>]
}
]
}
]
}
All Python examples are formatted for Python version 3.0 and higher, up to the latest Python version. If you are using versions of Python earlier than 3.0, ensure you manually remove parentheses for the print statements in this sample. For example, the print (response.content) statement updates to print response.content.
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
import requests
import json
# Login information
username = "[email protected]"
password = "FzmzI66%8AWK1"
server = "ses-ui.cybereason.net"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/crimes/unified"
api_url = base_url + endpoint_url
# These are the variables necessary to build the request.
query_element = "MalopProcess"
time_period_start = <time period start in epoch>
query = json.dumps({"totalResultLimit": 10000,"perGroupLimit":10000,"perFeatureLimit":100,"templateContext":"OVERVIEW","queryPath":[{"requestedType":query_element,"result": True,"filters":[{"facetName":"creationTime","filterType":"GreaterThan","values":[time_period_start]}]}]})
api_response = session.request("POST", api_url, data=query, headers=headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Step 2: Run your request and generate the response
In the command line, REST API client, or IDE, run the command or script that contains the request. After a few seconds, the Cybereason API returns a response.
Step 3: Evaluate the response
The response contains many fields with details about each Malop, including:
In particular, you may want to find:
The Malop ID - the many digit numerical string that typically starts with 11
Malop creationTime - the creationTime field
The Element names of the root cause of the Malop - the rootCauseElementNames field
There are numerous other fields you can view too. For details on all available fields, see Retrieve All MalOps.
Example Script
The following example script shows how to retrieve process Element Malops from the past seven days. The provided Python script automatically retrieves these fields from the API and prints them in a command window or console window.
If you want to run this script for multiple Elements, in the script, change the value of the query_element variable to the MalopProcess or MalopLogonSession as needed.
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "password"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/crimes/unified"
api_url = base_url + endpoint_url
# These are the variables necessary to build the request.
query_element = "MalopProcess"
time_period_start = 1577836800
query = json.dumps({"totalResultLimit":10000,"perGroupLimit":10000,"perFeatureLimit":100,"templateContext":"OVERVIEW","queryPath":[{"requestedType":query_element,"isResult":True,"filters":[{"facetName":"creationTime","filterType":"GreaterThan","values":[time_period_start]}]}]})
api_response = session.request("POST", api_url, data=query, headers=headers)
your_response = json.loads(api_response.content)
results_list = your_response['data']['resultIdToElementDataMap'].keys()
def getMalopDetails(malops_list):
for x in malops_list:
print(x + ": " + "Malop creation time - " + your_response['data']['resultIdToElementDataMap'][x]['simpleValues']['creationTime']['values'][0] + " Malop name - " + your_response['data']['resultIdToElementDataMap'][x]['simpleValues']['rootCauseElementNames']['values'][0])
getMalopDetails(results_list)