Retrieve All MalOps
Endpoint URL: https://<your server>/rest/detection/inbox
Endpoint URI: detection/inbox
Action: POST
Returns details about all AI Hunt MalOps and Endpoint Protection MalOps in your environment.
This request is supported for versions 20.1.43 and later.
Note
Ensure that you have logged into the Cybereason platform. For details, see Log in with the API.
Request Headers
Add a Content-Type:application/json header.
Note
If you are using cURL, add the authorization cookie details or the path to the file containing the cookie details as part of every request.
Request Body
Input: JSON
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Note
When you send this request, there may be a delay in returning a response, depending on how much data and activity is in your system. Ensure you do not send this request multiple times while waiting for a response as this may cause unexpected results and performance issues in your environment.
{
"startTime":"<time in milliseconds>",
"endTime":"<time in milliseconds>",
"groupIds":"<sensor group IDs>",
}
Request Parameters
URL/URI parameters: none
Request Body Parameters: Add the following available fields in the request. Required parameters are noted in bold.
startTime: The beginning time (in milliseconds) from which you want to retrieve MalOp that were active (both created and updated)
endTime: The ending time (in milliseconds) to which you want to retrieve MalOps (both created and updated)
groupIds: The group ID(s) if the sensors from which you want to retrieve MalOps. (From version 21.1.21 and later, for SOC Federation customers only)
Response Status Codes
This request can return the following status codes:
200: Success OK
400: Time range is not valid
Response Success Schema
The response contains the following fields:
Field |
Type |
Description |
|---|---|---|
malops |
Array |
An object that contains a list of Malops in your Cybereason environment. Each Malop has an individual GUID. |
guid |
Array |
An object that contains details on one specific item, such as Malop or a machine. |
status |
Enum |
The status of the Malop. Possible values include:
|
displayName |
String |
The display name for the item. |
rootCauseElementType |
Enum |
The Element that is the root cause of the Malop. |
rootCauseElementNamesCount |
Integer |
A count of the items that are the root cause or causes of the Malop. |
detectionEngines |
Enum |
The method of detecting the Malop. Possible values include (with the corresponding filter from the Malops management screen):
|
detectionTypes |
String |
The type of detection for the root cause. For details on the possible pre-defined values, see detectionTypes Field Values. |
malopDetectionType |
Enum |
The type of Malop. Possible values include:
|
machines |
Array |
An object that contains a list of machines associated with the root cause of the Malop. Each machine has an individual GUID. |
osType |
Enum |
The operating system type of the affected machine. Possible values include:
|
connected |
Boolean |
Indicates whether the machine is currently connected to the Cybereason server. |
isolate |
Boolean |
Indicates whether the machine is currently isolated. |
lastConnected |
Integer |
The time (in epoch) when the machine was last connected to a Cybereason server. |
users |
Array |
An object that contains a list of users associated with the root cause of the Malop. Each user has an individual GUID. |
admin |
Boolean |
Indicates whether the specified user has administrator privileges on the machine. |
localSystem |
Boolean |
Indicates whether the specified user has local system privileges on the machine. |
domainUser |
Boolean |
Indicates whether the specified user is a domain user. |
creationTime |
Integer |
The time (in epoch) when the Malop was generated. |
lastUpdateTime |
Integer |
The time (in epoch) when the Malop was last updated. |
labels |
Array |
An object that contains details on the labels, such as the label name and the time the label was added. |
iconBase64 |
Long |
The base64 value for the item that is the root cause of the Malop. |
priority |
Enum |
The priority of the Malop. Possible values include:
If the Malop does not have a priority, this value is null. |
decisionStatuses |
Enum |
The prevention action that the Cybereason platform used for this Malop. Possible values include:
|
severity |
Enum |
The Malop severity level. Possible values include:
|
groupIds |
Array |
The Group ID(s) of the affected sensors. (From version 21.1.21 and later, for SOC Federation customers only) |
edr |
Boolean |
Indicates whether the Malop is an Auto Hunt Malop or an Endpoint Protection Malop. |
escalated |
Boolean |
Indicates whether someone has marked the Malop as escalated. |
machineCounterModel |
Array |
An object containing details on the count of machines associated with Malops. |
totalMachines |
Integer |
The total number of machines associated with the Malops in the selected time filter. |
onlineInfectedCount |
Integer |
The total number of machines involved with an active Malop that are currently online. |
onlineCleanCount |
Integer |
The total number of machines not associated with an active Malop that are currently online. |
offlineInfectedCount |
Integer |
The total number of machines involved with an active Malop that are currently offline. |
offlineCleanCount |
Integer |
The total number of machines not associated with an active Malop that are currently offline. |
Response Failure Schema
None
Important Response Fields
Important information is found in these fields:
guid parameter: The unique GUID the Cybereason platform uses for the MalOp.
status parameter: The status of the MalOp.
displayName parameter: The display name for the MalOp. This is usually the name of the root cause Element.
rootCauseElement parameter: The Element identified as the root cause for the MalOp.
detectionEngine parameter: The method of detection used by the platform to detect the malicious activity.
detectionTypes parameter: The reason the Cybereason platform generated them MalOp.
malopDetectionType parameter: The type of MalOp.
machines object: An object containing details on the machines associated with the MalOp.
users object: An object containing details on users associated with the MalOp.
processes object: An object containing details on processes associated with the MalOp.
files object: An object containing details on files associated with the MalOp.
creationTime parameter: The time (in epoch) when the MalOp was generated by the platform.
lastUpdateTime parameter: The time (in epoch) when the platform last updated information relevant to the MalOp.
priority parameter: The priority assigned to the MalOp.
severity parameter: The severity assigned to the MalOp.
machineCounterModel object: Details on all machines associated with MalOps.
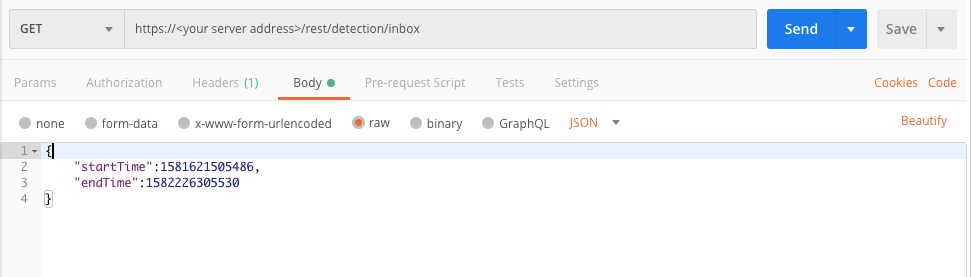
Example: Retrieve a list of MalOps of all types
Request
curl --request POST \
--url https://12.34.56.78/rest/detection/inbox \
--header 'Content-Type:application/json' \
--data '{
"startTime":1581621505486,"endTime":1582226305530
}'
Response
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "startTime":1581621505486, "endTime":1582226305530 }Response
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username ="[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
response = session.post(login_url, data=data, verify=True)
print (response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/detection/inbox"
api_url = base_url + endpoint_url
start_time = 1581621505486
end_time = 1582226305530
query = json.dumps({"startTime":start_time,"endTime":end_time})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "malops":[ { "guid":"11.7498520112250262440", "status":"Active", "displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx", "rootCauseElementType":"File", "rootCauseElementNamesCount":1, "detectionEngines":["EDR"], "detectionTypes":["Process opened a malicious file"], "malopDetectionType":"MALICIOUS_PROCESS", "machines":[ { "guid":"-576002811.1198775089551518743", "displayName":"a07-b37", "osType":"WINDOWS", "connected":true, "isolated":false, "lastConnected":1567254569103 } ], "users": [ { "guid":"0.2548072792133848559", "displayName":"a07-b37\\admin", "admin":true, "localSystem":false, "domainUser":false } ], "creationTime":1566356476000, "lastUpdateTime":1566356481000, "labels":["new malop"], "iconBase64":null, "priority":null, "decisionStatuses":null, "severity":"High", "edr":true, "escalated":false } ], "machineCounterModel": { "totalMachines":104, "onlineInfectedCount":32, "onlineCleanCount":34, "offlineInfectedCount":13, "offlineCleanCount":25 } }
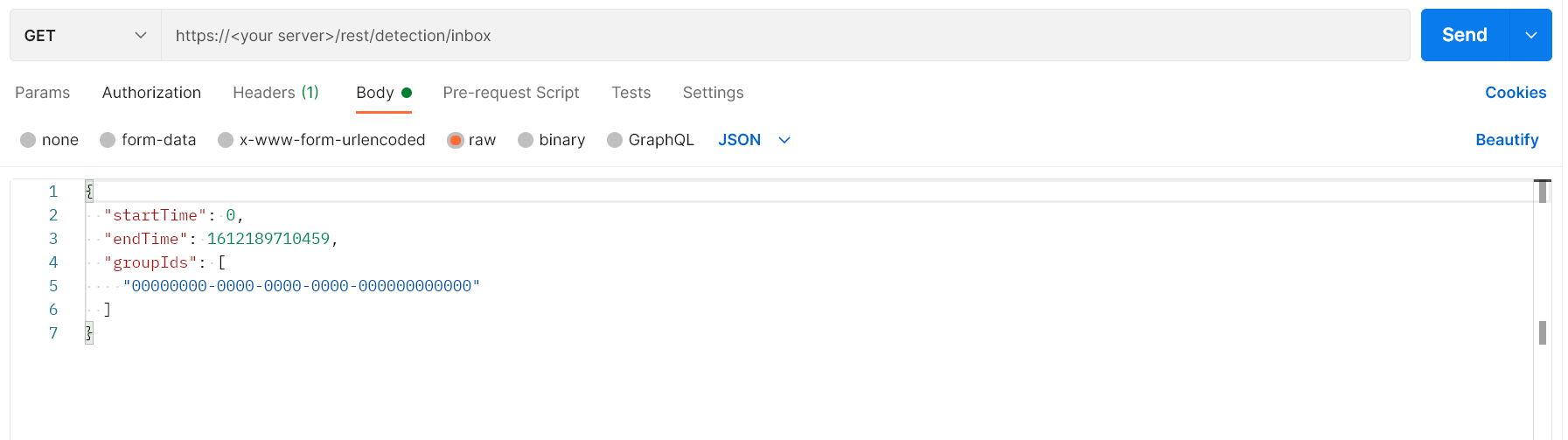
Example: Retrieve a list of MalOps of all types on unassigned sensor group IDs
Request
curl --request POST \
--url https://12.34.56.78/rest/detection/inbox \
--header 'Content-Type:application/json' \
--data '{
"startTime":0,"endTime":1612189710459,"groupIds":00000000-0000-0000-0000-000000000000
}'
Response
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"group": "00000000-0000-0000-0000-000000000000",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "startTime":0, "endTime":1612189710459, "groupIds": [ "00000000-0000-0000-0000-000000000000" ] }Response
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"group": "00000000-0000-0000-0000-000000000000",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username ="[email protected]" password = "mypassword" server = "myserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() response = session.post(login_url, data=data, verify=True) print (response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/detection/inbox" api_url = base_url + endpoint_url start_time = 0 end_time = 1612189710459 group_ID = 00000000-0000-0000-0000-000000000000 query = json.dumps({"startTime":start_time,"endTime":end_time,"groupID"group_ID}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))Response
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"group": "00000000-0000-0000-0000-000000000000",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}