Add Sensor Tags to a Machine Associated with a Malop
If certain machines are frequent targets of attackers, or certain types of machines seem more vulnerable to attack, you can add sensor tags to these machines to help your system admins easily identify and apply specific protection settings to these machines.
You can use the API to automatically add the tags to a machine after at least one Malop occurs on the machine. This topic provides a step by step example of how to extract this information from a Malop and add sensor tags to that machine.
In this topic:
Step 1: Build the request to retrieve Malops
To build this request, you need the following keys:
requestedType: This key is the Element on which the Cybereason platform generates the Malop. You can set the value to MalopProcess or MalopLogonSession.
Because the Cybereason platform generates Malops based on MalopProcess and MalopLogonSession Element, you must run separate requests for each Element to retrieve all Malops.
totalResultLimit: This key is the total number of results. This example uses the default value.
perGroupLimit: This key is the total number per group. This example uses the default value.
perFeatureLimit: This key is the total number for the selected Feature. This example uses the default value.
Note
Although version 20.1 and later include a new endpoint to retrieve Malop details (/rest/detection/inbox), you can still use the endpoint (/rest/crimes/unified) in the example below on these versions.
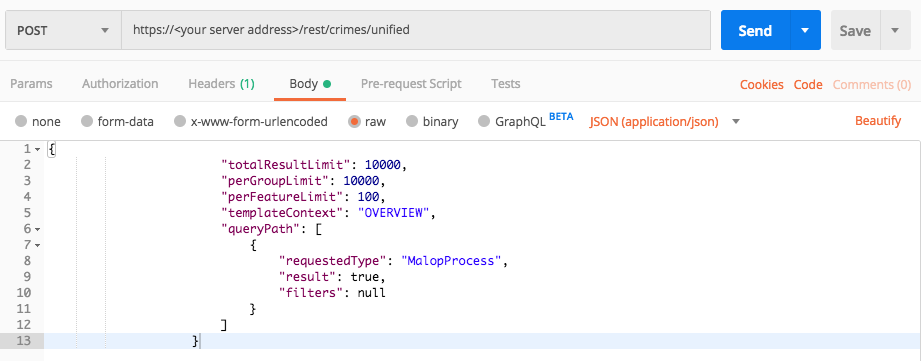
To build the request, replace the placeholders in the relevant cURL command, request body example, or Python script:
curl --request POST \
--url http://myserver.com/rest/crimes/unified \
--header 'Content-Type:application/json' \
--data '{
"totalResultLimit": 10000,
"perGroupLimit": 10000,
"perFeatureLimit": 100,
"templateContext": "OVERVIEW",
"queryPath": [
{
"requestedType": "MalopProcess",
"result": true,
"filters": null
}
]
}'
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"totalResultLimit": 10000,
"perGroupLimit": 10000,
"perFeatureLimit": 100,
"templateContext": "OVERVIEW",
"queryPath": [
{
"requestedType": "MalopProcess",
"result": true,
"filters": null
}
]
}
All Python examples are formatted for Python version 3.0 and higher, up to the latest Python version. If you are using versions of Python earlier than 3.0, ensure you manually remove parentheses for the print statements in this sample. For example, the print (response.content) statement updates to print response.content.
Note
The code in this sample is repeated in the second sample below. You do not need to run the script now but it is used here to help you understand how you build the request.
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/crimes/unified"
api_url = base_url + endpoint_url
null = None
query = json.dumps({"totalResultLimit": 10000,"perGroupLimit":10000,"perFeatureLimit":100,"templateContext":"OVERVIEW","queryPath":[{"requestedType": "MalopProcess","result": True,"filters": null}]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Step 2: Run the request and generate the response
In the command line, REST API client, or IDE, run the command or script that contains the request. After a few seconds, the Cybereason API returns a response.
Step 3: Evaluate the response
When the Cybereason API returns a response for a Malop retrieval request, the data in the response contains many different pieces of data.
However, to add a sensor tag to a machine, you only need to locate the following fields.
Note
The example Python scripts in this topic contain the code to automatically find these values and print them in an easily visible way, so that you do not have to read each line in the response.
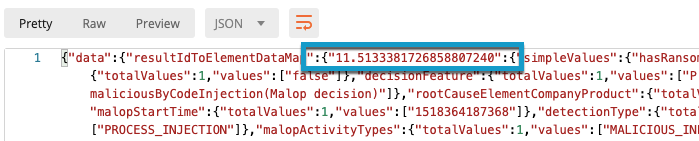
The unique Malop ID. The Malop ID normally begins with 11 and are found throughout the response.
To find the Malop ID, in the request body, locate the data object, and then locate the resultIdToElementDataMap object. The key that immediately follows these object fields is the Malop ID:
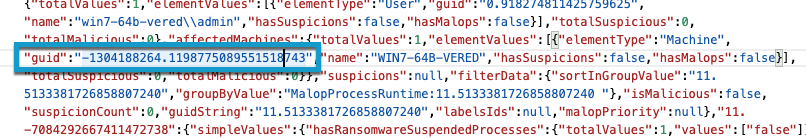
The machine name. Inside the Malop object (which begins with the Malop ID that you found), locate the affectedMachines object and the name key inside this object. This is the machine name for the machine associated with the Malop.
Step 4: Build the request to add sensor tags
When you add sensor tags, you will need to add values for a number of keys:
The machine name. You add sensor tags per machine. To add sensor tags correctly, you must specify the machine name.
Predefined sensor tag values. The Cybereason platform contains a number of predefined tags, including:
Department
Location
Device type
Critical Asset.
You can add any string value you want for the Department, Location, and Device type tags.
The Critical Asset tag is a boolean value and therefore requires a True or False value.
Custom sensor tags. You can also add a tag labeled CUSTOM. Set the value to any string value you need.
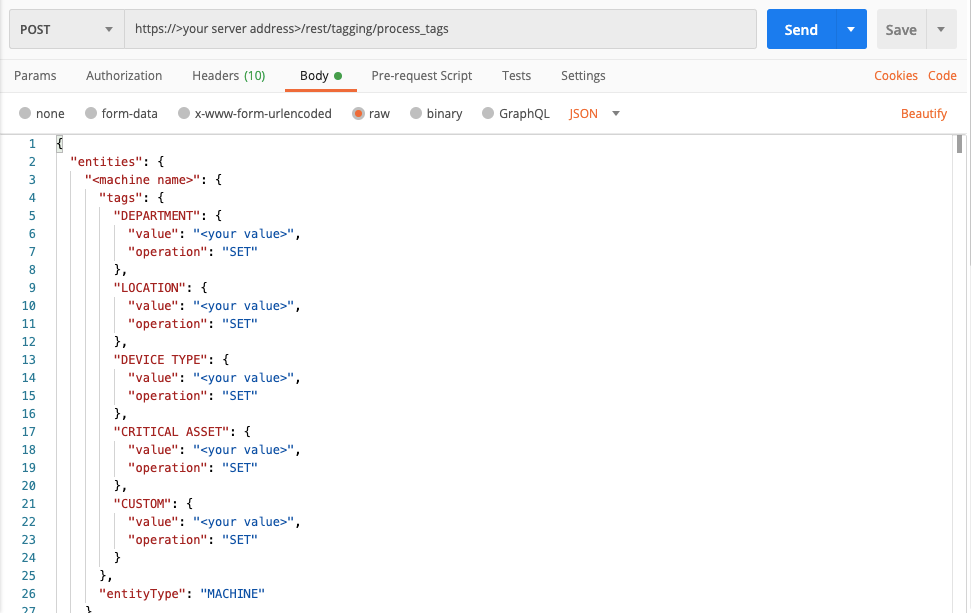
To build a request to add a sensor tag, replace the placeholders in the following cURL command, request body example, or Python script with the values that you want:
curl --request POST \
--url http://myserver.com/rest/tagging/process_tags \
--header 'Content-Type:application/json' \
--data '{
"entities": {
"<machine name>": {
"tags": {
"DEPARTMENT": {
"value": "<your value>",
"operation": "SET"
},
"LOCATION": {
"value": "<your value>",
"operation": "SET"
},
"DEVICE TYPE": {
"value": "<your value>",
"operation": "SET"
},
"CRITICAL ASSET": {
"value": "<your value>",
"operation": "SET"
},
"CUSTOM": {
"value": "<your value>",
"operation": "SET"
}
},
"entityType": "MACHINE"
}
}
}'
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"entities": {
"<machine name>": {
"tags": {
"DEPARTMENT": {
"value": "<your value>",
"operation": "SET"
},
"LOCATION": {
"value": "<your value>",
"operation": "SET"
},
"DEVICE TYPE": {
"value": "<your value>",
"operation": "SET"
},
"CRITICAL ASSET": {
"value": "<your value>",
"operation": "SET"
},
"CUSTOM": {
"value": "<your value>",
"operation": "SET"
}
},
"entityType": "MACHINE"
}
}
}
All Python examples are formatted for Python version 3.0 and higher, up to the latest Python version. If you are using versions of Python earlier than 3.0, ensure you manually remove parentheses for the print statements in this sample. For example, the print (response.content) statement updates to print response.content.
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
endpoint_url = "/rest/crimes/unified"
api_url = base_url + endpoint_url
null = None
query = json.dumps({"totalResultLimit": 10000,"perGroupLimit":10000,"perFeatureLimit":100,"templateContext":"OVERVIEW","queryPath":[{"requestedType": "MalopProcess","result": True,"filters": null}]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
results_list = (your_response['data']['resultIdToElementDataMap'].keys())
malop_id = (results_list[1])
machine_name = (your_response['data']['resultIdToElementDataMap'][malop_id]['elementValues']['affectedMachines']['elementValues'][0]['name'])
endpoint_url_2 = "/rest/tagging/process_tags"
api_url_2 = base_url + endpoint_url_2
department_tag = "Docs"
location_tag = "USA"
device_type_tag = "Mac"
critical_asset_tag = "false"
custom_tag = "Malop"
tags = json.dumps({"entities":{machine_name:{"tags":{"DEPARTMENT":{"value":department_tag,"operation":"SET"},"LOCATION":{"value":location_tag,"operation":"SET"},"DEVICE TYPE":{"value":device_type_tag,"operation":"SET"},"CRITICAL ASSET":{"value":critical_asset_tag,"operation":"SET"},"CUSTOM":{"value":custom_tag,"operation":"SET"}},"entityType":"MACHINE"}}})
api_response = session.request("POST", api_url_2, data=tags, headers=headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Step 5: Run the request and generate the request body
In the command line, REST API client, or IDE, run the command or script that contains the request. After a few seconds, the Cybereason API returns a response.
Step 6: Evaluate the response
The response for this request includes several items. The majority of these items repeat the values you entered for the tag in the request.
To verify that the request to add sensor tags to a machine was successful, view the results object and ensure the success field reports true.