Find Connections for a Specific IP Address
Sometimes, if you find that a specific IP address has made unauthorized connections to your environments, you may want to find out what other connections were made to this IP address.
Follow these steps to search for connections:
Step 1: Build the request to retrieve connections
To help you find connections for an IP address, you need to build a query that filters by the IP address.
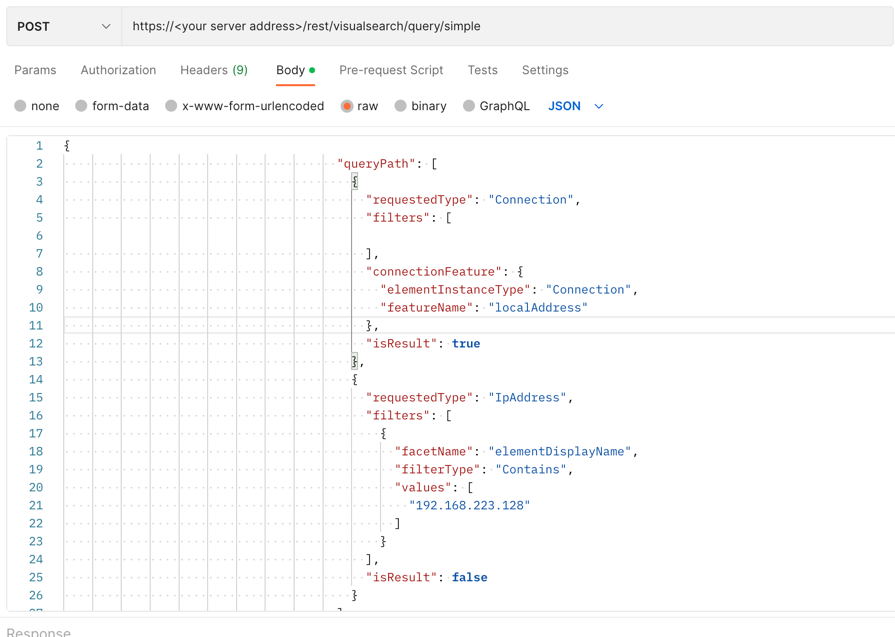
To build the request, replace the placeholders in the relevant cURL command, request body example, or Python script:
curl --request POST \
--url https://<your server>/rest/visualsearch/query/simple \
--header 'Content-Type:application/json' \
--data '{
"queryPath": [
{
"requestedType": "Connection",
"filters": [
],
"connectionFeature": {
"elementInstanceType": "Connection",
"featureName": "localAddress"
},
"isResult": true
},
{
"requestedType": "IpAddress",
"filters": [
{
"facetName": "elementDisplayName",
"filterType": "Contains",
"values": [
"192.168.223.128"
]
}
],
"isResult": false
}
],
"totalResultLimit": "100",
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "DETAILS",
"queryTimeout": 120000,
"pagination": {
"pageSize": 1000
},
"customFields": [
"ownerMachine",
"ownerProcess.user",
"localPort",
"remotePort",
"transportProtocol",
"state",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}'
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
{
"queryPath": [
{
"requestedType": "Connection",
"filters": [],
"connectionFeature": {
"elementInstanceType": "Connection",
"featureName": "localAddress"
},
"isResult": true
},
{
"requestedType": "IpAddress",
"filters": [
{
"facetName": "elementDisplayName",
"filterType": "Contains",
"values": [
"192.168.223.128"
]
}
],
"isResult": false
}
],
"totalResultLimit": "100",
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "DETAILS",
"queryTimeout": 120000,
"pagination": {
"pageSize": 1000
},
"customFields": [
"ownerMachine",
"ownerProcess.user",
"localPort",
"remotePort",
"transportProtocol",
"state",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}
Note
The code in this sample is repeated in the samples below. You do not need to run the script now but it is used here to help you understand how you build the request.
All Python examples are formatted for Python version 3.0 and higher, up to the latest Python version. If you are using versions of Python earlier than 3.0, ensure you manually remove parentheses for the print statements in this sample. For example, the print (response.content) statement updates to print response.content.
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
ip_address = "192.168.223.128"
query = json.dumps({"queryPath":[{"requestedType": "Connection","filters":[],"connectionFeature":{"elementInstanceType":"Connection","featureName":"localAddress"},"isResult":True},{"requestedType":"IpAddress","filters":[{"facetName":"elementDisplayName","filterType":"Contains","values":[ip_address]}],"isResult":False}],"totalResultLimit": "100","perGroupLimit": 100,"perFeatureLimit": 100,"templateContext": "DETAILS","queryTimeout": 120000,"pagination": {"pageSize": 1000},"customFields": ["ownerMachine","ownerProcess.user","localPort","remotePort","transportProtocol","state","calculatedCreationTime","endTime","elementDisplayName"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Step 2: Run your request and generate the response
In the command line, REST API client, or IDE, run the command or script that contains the request. After a few seconds, the Cybereason API returns a response.
Step 3: Evaluate the response
The response contains a large number fields. Focus on these fields for meaningful information: