Retrieve a List of Malops and Malop Details (pre-20.1)
In this tutorial, we will explain, step-by-step, how to use the Cybereason API (in versions prior to 20.1) to retriev ea list of all Malops in your environment, as well as details about those Malops.
You must have the Analyst L1, L2, or L3 role to perform these commands.
As part of your security management and response automation efforts, you may want to retrieve a list of all Malops or a partial list of Malops to use in incident management, ticketing, and so forth. You can use the API to retrieve a list of Malops, which you can then use to integrate with your own systems.
In this topic:
Retrieve all Malops
Note
The request body is the same regardless of how you run the request (such as a cURL command, in a REST API client, or Python script).
#. Ensure you log in to the Cybereason platform with the API. For details, see Log in with the API. #, In your REST API client, open a new tab/file. #. In the relevant field, enter the URL for the request:
Ensure that the method for the request is set to POST. (This may be the default for your REST API client, but if not, ensure that you select it.)
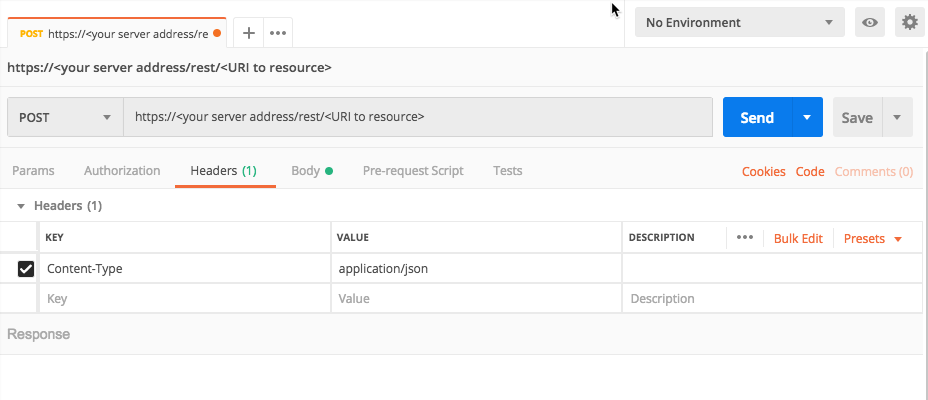
For the Headers, in the Key column, add a Content-Type header.
In the Value column, add the value application/json.
For example, in Postmanm, your header will look like this:
Navigate to the section to add your request body. In Postman, for example, this is the Body tab.
In the Body tab, ensure that you have set your client editor to enable you to add raw JSON content. In Postman, for example, ensure that Raw is selected.
In the request body edit area, enter an open and closed bracket {}. This is the standard syntax for JSON.
You are now ready to begin adding the objects and key/value pairs that build the request body.
Inside the brackets, add this template request body:
{ "totalResultLimit": 10000, "perGroupLimit": 10000, "perFeatureLimit": 100, "templateContext": "OVERVIEW", "queryPath": [ { "requestedType": "MalopProcess", "result": true, "filters": null } ] }
In your client machine, run your request.
In the request body, for the requestedType key, update the value from MalopProcess to MalopLogonSession.
The Cybereason platfrom creates Malops based on the MalopProcess Element and the MalopLogonSession Element, so you need to run the request twice to ensure you retrieve all Malops.
In your client machine, run the request again.
For both requests, the response contains a list of all relevant Malops with various details on the Malops. We will look at the parts of the response in the next section.
View the response with Malop details
In the response to retrieve Malops, there are a large number of key/value pairs related to Malops:
{
"data": {
"resultIdToElementDataMap": {
"11.5133381726858807240": {
"simpleValues": {
"hasRansomwareSuspendedProcesses": {
"totalValues": 1,
"values": [
"false"
]
},
"decisionFeature": {
"totalValues": 1,
"values": [
"Process.maliciousByCodeInjection (Malop decision)"
]
},
"rootCauseElementCompanyProduct": {
"totalValues": 0,
"values": null
},
"malopStartTime": {
"totalValues": 1,
"values": [
"1518364187368"
]
},
"detectionType": {
"totalValues": 1,
"values": [
"PROCESS_INJECTION"
]
},
"malopActivityTypes": {
"totalValues": 1,
"values": [
"MALICIOUS_INFECTION"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"MALICIOUS_INFECTION"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1518364234280"
]
},
"isBlocked": {
"totalValues": 1,
"values": [
"false"
]
},
"rootCauseElementTypes": {
"totalValues": 1,
"values": [
"Process"
]
},
"rootCauseElementNames": {
"totalValues": 1,
"values": [
"iathookdll.dll (malopgenerator.exe > notepad.exe)"
]
},
"malopLastUpdateTime": {
"totalValues": 1,
"values": [
"1518364234280"
]
},
"allRansomwareProcessesSuspended": {
"totalValues": 1,
"values": [
"false"
]
},
"rootCauseElementHashes": {
"totalValues": 1,
"values": [
"7aa61ff36c9c490184c416820c88371be46ab7c0"
]
},
"managementStatus": {
"totalValues": 1,
"values": [
"UNREAD"
]
},
"closeTime": {
"totalValues": 1,
"values": [
null
]
},
"closerName": {
"totalValues": 1,
"values": [
null
]
},
"customClassification": {
"totalValues": 1,
"values": [
"None"
]
}
},
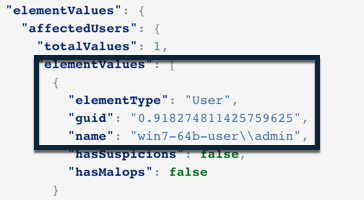
"elementValues": {
"affectedUsers": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.918274811425759625",
"name": "win7-64b-user\\admin",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"affectedMachines": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1304188264.1198775089551518743",
"name": "WIN7-64B-USER",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": null,
"filterData": {
"sortInGroupValue": "11.5133381726858807240",
"groupByValue": "MalopProcessRuntime:11.5133381726858807240 "
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "11.5133381726858807240",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {},
"evidenceMap": {},
"totalPossibleResults": 188,
"queryLimits": {
"totalResultLimit": 10000,
"perGroupLimit": 10000,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "MalopProcess",
"featureName": "self"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "MalopProcess",
"featureName": null
},
"count": 188
}
]
},
"status": "SUCCESS",
"message": ""
}
While the Cybereason platfrom uses each of these fields to process Malop data, you may want to focus on the important Malop details:
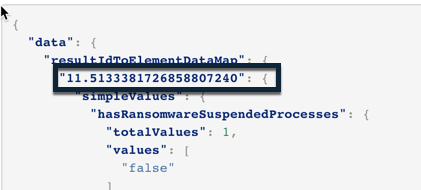
Malop ID: The Malop ID is a multi-digit number, usually beginning with 11, that shows the unique identifier for the Malop:
malopStartTime
detectionType: The type of Malop
malopActivityTypes: The part of the attack lifecycle related to this Malop
creationTime
rootCauseElementName: The name of the specific process or logon session identified as the root cause of the Malop.
malopLastUpdateTime
managementStatus: The current status of the Malop
closeTime
The guid and name fields for the affectedUsers and affectedMachines objets in the elementValues object
suspicions object: Details on the suspicions associated with the Malop
Retrieve details on a specific Malop
Note
The request body is the same regardless of how you run the request (such as a cURL command, in a REST API client, or Python script).
In addition to retrieving a list of all Malops, you have the ability to retrieve details on a single or finite number of Malops.
In your REST API client, open another tab/file.
In the relevant field, enter the URL for the request (the same as the previous section):
https://<your server address>/rest/crimes/unified
Ensure that the method for the request is set to POST.
For the Headers, for the Key column, add a Content-Type header.
In the Value column, add the value application/json.
Navigate to the section to add your request body.
In the Body tab, ensure that you have set your client editor to enable you to add raw JSON content.
In the request body edit area, enter an open and closed bracket {}.
Inside the brackets, add this template request body:
{ "totalResultLimit":10000, "perGroupLimit":10000, "perFeatureLimit":100, "templateContext":"OVERVIEW", "queryPath":[ { "requestedType":"MalopProcess", "guidList":["<Malop guid"], "result":true,"filters":null } ] }
In the request body, in the queryPath object, in the guidList object, update the Malop guid placeholder to 11.64804795222430027 (a fictitious Malop ID).
{ "totalResultLimit":10000, "perGroupLimit":10000, "perFeatureLimit":100, "templateContext":"OVERVIEW", "queryPath":[ { "requestedType":"MalopProcess", "guidList":["**11.64804795222430027**"], "result":true,"filters":null } ] }
In your client machine, run your request.
The response should contain the same fields as the previous section, but there will be only one Malop ID in the response.
Retrieve Malops from a time period
Note
The request body is the same regardless of how you run the request (such as a cURL command, in a REST API client, or Python script).
In addition, you can retrieve Malops from a certain time range. Using this type of filter enables you to retrieve only the most recent Malop or Malops from a time period you have not previously checked.
In your REST API client, open another new tab/file.
In the relevant field, enter the URL for the request:
https://<your server address>/rest/crimes/unified
Ensure that the method for the request is set to POST.
For the Headers, in the Key column, add a Content-Type header.
For the Value column add the value application/json.
Navigate to the section to add your request body.
In the Body tab, ensure that you have set your client editor to enable you to add JSON content.
In the request body edit area, enter an open and closed bracket {}.
Inside the brackets, add this template request body:
{ "totalResultLimit":10000, "perGroupLimit":10000, "perFeatureLimit":100, "templateContext":"OVERVIEW", "queryPath":[{ "requestedType":"MalopProcess", "filters":[ { "facetName": "creationTime", "filterType": "<operator>", "values": ["<time in epoch>"] } ], "isResult": true }] }
As part of the time filter, you must specify a time feature and an operator.
For this example, we will use the creationTime feature. However, you need to add an operator.
In the filters object, for the filterType key, for the operator placeholder value, add GreaterThan. This will retrieve all Malops after the time specified.
{ "totalResultLimit":10000, "perGroupLimit":10000, "perFeatureLimit":100, "templateContext":"OVERVIEW", "queryPath":[{ "requestedType":"MalopProcess", "filters":[ { "facetName": "creationTime", "filterType": "GreaterThan", "values": ["<time in epoch>"] } ], "isResult": true }] }
Lastly, you must add a time from which to filter. You add this time in epoch form.
In the filters object, for the values array, replace the “”<time in epoch>” placeholder value with the value 1572965899000 without quotes (a random time).
{ "totalResultLimit":10000, "perGroupLimit":10000, "perFeatureLimit":100, "templateContext":"OVERVIEW", "queryPath":[{ "requestedType":"MalopProcess", "filters":[ { "facetName": "creationTime", "filterType": "GreaterThan", "values": [1572965899000] } ], "isResult": true }] }
In your client machine, run the request.
The response will contain a list of Malops, but it should be a more limited list with times in the range you specified.
Next steps
Now that you understand how to retrieve Malops - both the full list and a filtered list - you can begin incorporating these requests into your automation and orchestration frameworks to better streamline your operations.