Retrieve a List of Malops and Malop Details (20.1 and later)
In this tutorial, we will explain, step-by-step, how to use the Cybereason API to retrieve a list of Malops in your environment (on versions 20.1 and later), as well as details about those Malops.
You must have the Analyst L1, L2, or L3 role to perform these commands.
As part of your security management and response automation efforts, you may want to retrieve a list of all Malops or a partial list of Malops to use in incident management, ticketing, and the like. You can use the API to retrieve a list of Malops, which you can then use to integrate with your own systems.
Beginning in version 20.1, the Cybereason platform expands the definition of a Malop. In prior versions, the platform used the term “Malop” for those situations detected using the EDR component of the Cybereason platform. However, in version 20.1 and later, the Malop definition was expanded to include situations detectedd by the platform’s EPP component.
As a result, the Cybereason platform has two different kinds of Malops:
AI Hunting Malops: Malops created using the Cybereason platform’s Endpoint Detection and Response data collection abilities and proprietary detection rules
Endpoint Protection Malops: Malops created based on events detected by endpoint sensors. These were previously known as Malware alerts.
The request in this tutorial retrieves both types of Malops.
In this topic:
Build the request body
Note
The request body is the same regardless of how you run the request (such as a cURL command, in a REST API client, or Python script).
Ensure you log in to the Cybereason platform with the API. For details, see Log in with the API.
In your REST API client, open a new tab/file.
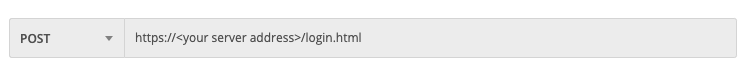
In the relevant field, enter the URL for the request:
https://<your server address>/rest/detection/inbox
For example, in Postman, you enter the URL here:
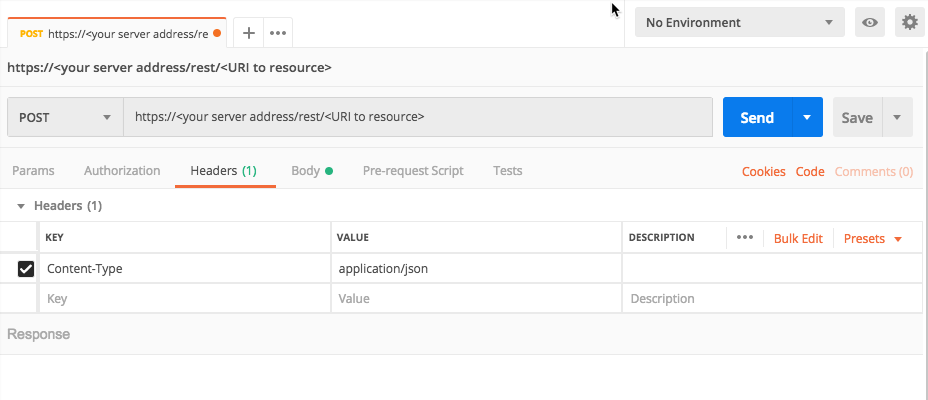
Ensure that the method for the request is set to POST. (This may be the default for your REST API client, but if not, ensure that you select it.)
For the Headers, in tne Key column, add a Content-Type header.
In the Value column, add the value application/json.
For example, in Postman, your header will look like this:
Navigate to the section to add your request body. In Postman, for example, this is the Body tab.
In the Body tab, ensure that you have set your client editor to enable you to add raw JSON content. In Postman, for example, ensure that Raw is selected.
In the request body edit area, enter an open and closed bracket {}. This is the standard syntax for JSON.
Inside the brackets, add this template request body:
{ "startTime":"<time in milliseconds>", "endTime":"<time in milliseconds>" }
In the request body, in the startTimne key, for the <time in milliseconds> placeholder value, add the value 1581621505486 (a random time in millisecond format).
{ "startTime":"**1581621505486**", "endTime":"<time in milliseconds>" }
In the endTime key, for the <time in milliseconds> placeholder value, add the value 1582226305530.
{ "startTime":"1581621505486", "endTime":"**1582226305530**" }
In your client machine, run your request.
View the details in the response
In the response to retrieve the Malops, there are a large number of key/value pairs related to Malops:
{
"malops":[
{
"guid":"11.7498520112250262440",
"status":"Active",
"displayName":"83714d9c0ef6b8901fe7dfeffce7c451.xlsx",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["EDR"],
"detectionTypes":["Process opened a malicious file"],
"malopDetectionType":"MALICIOUS_PROCESS",
"machines":[
{
"guid":"-576002811.1198775089551518743",
"displayName":"a07-b37",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567254569103
}
],
"users": [
{
"guid":"0.2548072792133848559",
"displayName":"a07-b37\\admin",
"admin":true,
"localSystem":false,
"domainUser":false
}
],
"creationTime":1566356476000,
"lastUpdateTime":1566356481000,
"labels":["new malop"],
"iconBase64":null,
"priority":null,
"decisionStatuses":null,
"severity":"High",
"edr":true,
"escalated":false
}
],
"machineCounterModel": {
"totalMachines":104,
"onlineInfectedCount":32,
"onlineCleanCount":34,
"offlineInfectedCount":13,
"offlineCleanCount":25
}
}
Each Malop appears in its own object with its own details.
In this response, you may want to focus on these important keys:
guid: The unique identifier the Cybereason platform uses for the Malop.
status: The current status of the Malop.
displayName: The name for the Malop (usually the name of the root cause Element)
rootCauseElementType: The Element type identified as the root cause.
detectionEngine: The method the Cybereason platform uses to detect the behavior, such as EDR.
detectionTypes: The specific Malop type name.
malopDetectionType: The type of Malop.
machines object: Detials on the machines associated with the Malop, including the machine GUID and name.
users object: Details on users associated with the Malop, including the user GUID and name
creationTime: The time the Cybereason platform generated the Malop.
lastUpdateTime: The last time the Malop details were updated
machineCounterModel: A listing of the number of machines associated with the Malop.
Next steps
Now that you understand how to retrieve Malops in versions 20.1 and later, you can begin incorporating these requests into your automation and orchestration frameworks to better streamline your operations.