Find Scanning Activity
Use the API to hunt for malicious behavior occurring in the scanning stage of an attack.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
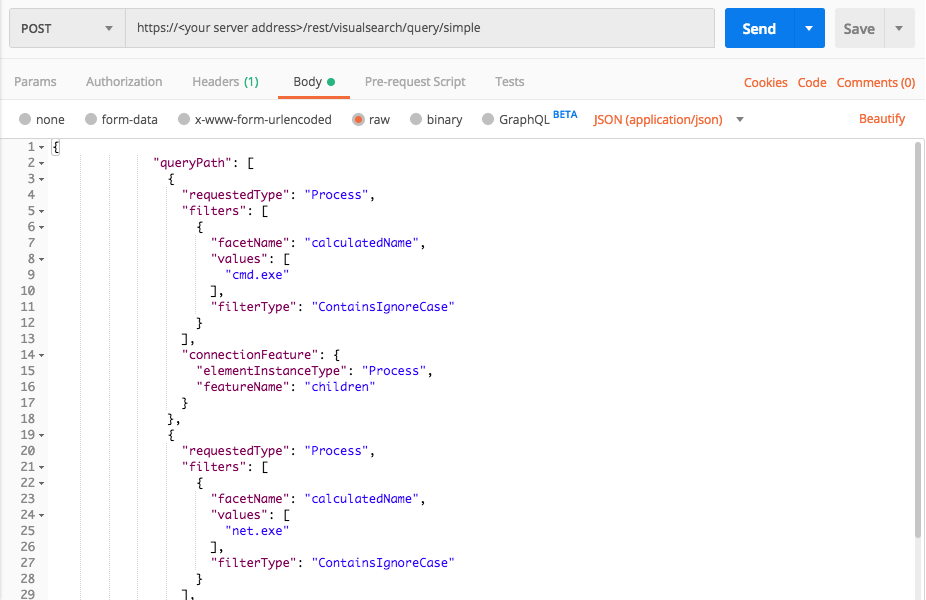
Processes executing extensive net commands
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"cmd.exe"
],
"filterType":"ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType":"Process",
"featureName":"children"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"net.exe"
],
"filterType":"ContainsIgnoreCase"
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
"iconBase64"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"cmd.exe"
],
"filterType": "ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "children"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"net.exe"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
"iconBase64"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "calculatedName"
query_element_1_filter_value = "cmd.exe"
linking_element = "Process"
linking_feature = "children"
query_element_2_filter_value = "net.exe"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"ContainsIgnoreCase"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_2_filter_value],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
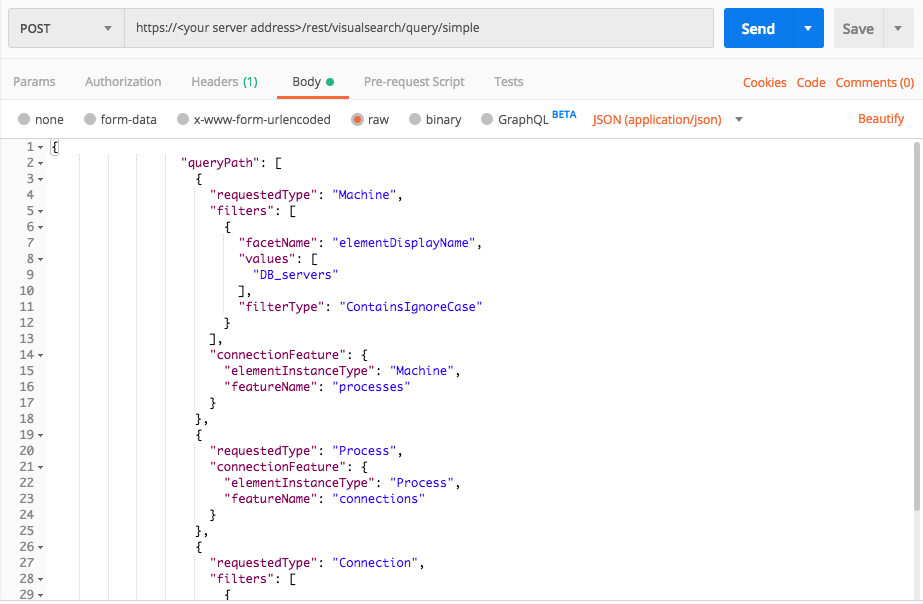
Fake module suspicion
Use this request to investigate machines running processes with counterfeit modules.
In this query, you search for the following suspicious behaviors:
DB_servers = [“serverName1”, “serverName2”,….]
Web_servers = [“serverName1”, “serverName2”, ….]
Mail_servers = [“serverName1”, “serverName2”, ….]
Run this request for every type of server list.
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Machine",
"filters": [
{
"facetName": "elementDisplayName",
"values": [
"DB_servers"
],
"filterType":"ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType": "Machine",
"featureName": "processes"
}
},
{
"requestedType": "Process",
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
}
},
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"direction",
"serverAddress",
"serverPort",
"portType",
"aggregatedReceivedBytesCount",
"aggregatedTransmittedBytesCount",
"remoteAddressCountryName",
"accessedByMalwareEvidence",
"ownerMachine",
"ownerProcess",
"dnsQuery",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Machine",
"filters": [
{
"facetName": "elementDisplayName",
"values": [
"DB_servers"
],
"filterType": "ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType": "Machine",
"featureName": "processes"
}
},
{
"requestedType": "Process",
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
}
},
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"direction",
"serverAddress",
"serverPort",
"portType",
"aggregatedReceivedBytesCount",
"aggregatedTransmittedBytesCount",
"remoteAddressCountryName",
"accessedByMalwareEvidence",
"ownerMachine",
"ownerProcess",
"dnsQuery",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "nKnAJmBSF0i9"
server = "workshop.cybereason.net"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Machine"
query_element_1_filter = "elementDisplayName"
query_element_1_filter_value = "DB_servers"
linking_element = "Machine"
linking_feature = "Processes"
query_element_2 = "Process"
linking_element_2 = "Process"
linking_feature_2 = "connections"
query_element_3 = "Connection"
query_element_3_filter = "isExternalConnection"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"ContainsIgnoreCase"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"connectionFeature":{"elementInstanceType":linking_element_2,"featureName":linking_feature_2}},{"requestedType":query_element_3,"filters":[{"facetName":query_element_3_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["direction","serverAddress","serverPort","portType","aggregatedReceivedBytesCount","aggregatedTransmittedBytesCount","remoteAddressCountryName","accessedByMalwareEvidence","ownerMachine","ownerProcess","dnsQuery","calculatedCreationTime","endTime","elementDisplayName"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
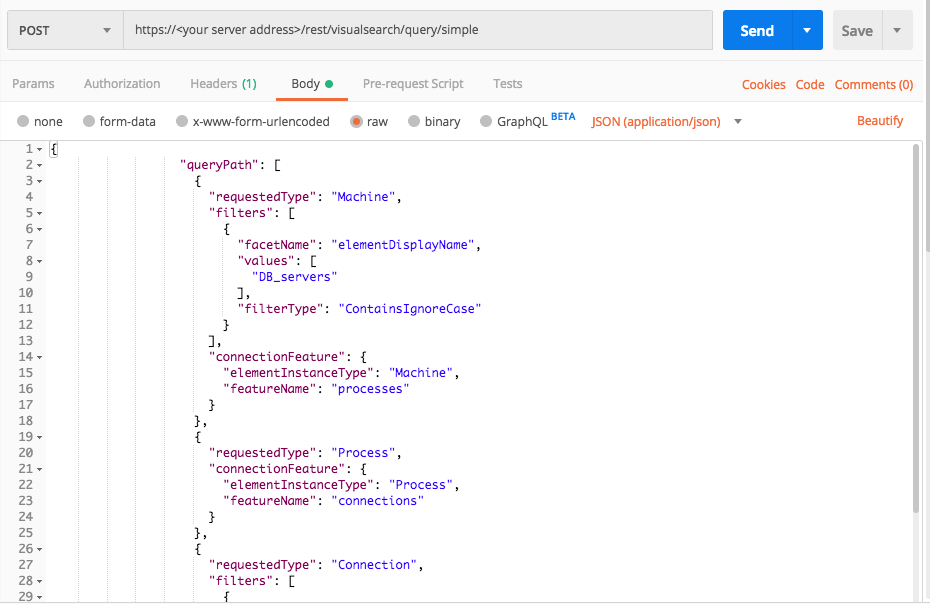
Database external connection
Use this request to investigate machines running processes with external connections.
In this query, you search for the following suspicious behaviors:
DB_servers = [“serverName1”, “serverName2”,….]
Web_servers = [“serverName1”, “serverName2”, ….]
Mail_servers = [“serverName1”, “serverName2”, ….]
Run this request for every type of server list.
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Machine",
"filters": [
{
"facetName": "elementDisplayName",
"values": [
"DB_servers"
],
"filterType":"ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType": "Machine",
"featureName": "processes"
}
},
{
"requestedType": "Process",
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
}
},
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"direction",
"serverAddress",
"serverPort",
"portType",
"aggregatedReceivedBytesCount",
"aggregatedTransmittedBytesCount",
"remoteAddressCountryName",
"accessedByMalwareEvidence",
"ownerMachine",
"ownerProcess",
"dnsQuery",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Machine",
"filters": [
{
"facetName": "elementDisplayName",
"values": [
"DB_servers"
],
"filterType": "ContainsIgnoreCase"
}
],
"connectionFeature": {
"elementInstanceType": "Machine",
"featureName": "processes"
}
},
{
"requestedType": "Process",
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
}
},
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"direction",
"serverAddress",
"serverPort",
"portType",
"aggregatedReceivedBytesCount",
"aggregatedTransmittedBytesCount",
"remoteAddressCountryName",
"accessedByMalwareEvidence",
"ownerMachine",
"ownerProcess",
"dnsQuery",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print session.cookies.items()
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Machine"
query_element_1_filter = "elementDisplayName"
query_element_1_filter_value = "DB_servers"
linking_element = "Machine"
linking_feature = "processes"
query_element_2 = "Process"
linking_element_2 = "Process"
linking_feature_2 = "connections"
query_element_3 = "Connection"
query_element_3_filter = "isExternalConnection"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"ContainsIgnoreCase"}],"connectionFeature": {"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"connectionFeature":{"elementInstanceType":linking_element_2,"featureName":linking_feature_2}},{"requestedType":query_element_3,"filters": [{"facetName":query_element_3_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["direction","serverAddress","serverPort","portType","aggregatedReceivedBytesCount","aggregatedTransmittedBytesCount","remoteAddressCountryName","accessedByMalwareEvidence","ownerMachine","ownerProcess","dnsQuery","calculatedCreationTime","endTime","elementDisplayName"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))