Generic Queries
Generic queries may return a high rate of false positives, but can be useful in noisy environments. Use the Query API to perform these generic queries and further your investigation.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
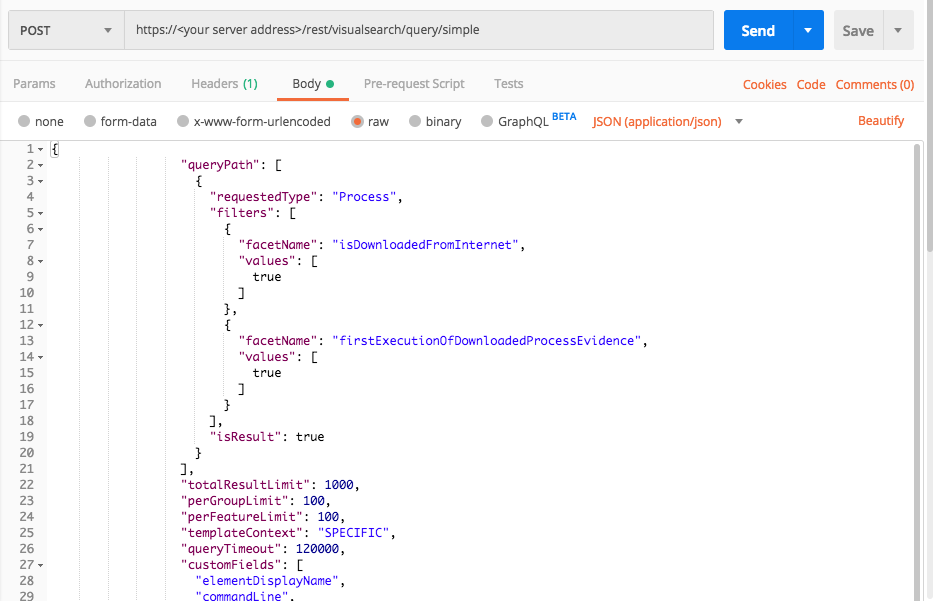
Find binaries users downloaded from the Internet
Use this request to locate drive-by attacks and trojaned binaries.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data ' {
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName": "isDownloadedFromInternet",
"values": [
true
]
},
{
"facetName": "firstExecutionOfDownloadedProcessEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-2046359355.-446319856563366924": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1512300801309"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512300801311"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"ransomfreetest.exe"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-6313743191401684913",
"name": "mydomain\\mark",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2046359355.-7870067516287985870",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"blackListFileSuspicion": 1512300804528
},
"filterData": {
"sortInGroupValue": "-2046359355.-446319856563366924",
"groupByValue": "ransomfreetest.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-2046359355.-446319856563366924",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512314218832,
"totalSuspicions": 1
},
"ransomwareByCanaryFilesSuspicion": {
"potentialEvidence": [
"ransomwareByCanaryFilesEvidence"
],
"firstTimestamp": 1512313571594,
"totalSuspicions": 1
},
"connectingToBadReputationAddressSuspicion": {
"potentialEvidence": [
"hasMaliciousConnectionEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
}
},
"evidenceMap": {},
"totalPossibleResults": 13,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 13
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "isDownloadedFromInternet",
"values": [
true
]
},
{
"facetName": "firstExecutionOfDownloadedProcessEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-2046359355.-446319856563366924": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1512300801309"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512300801311"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"ransomfreetest.exe"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-6313743191401684913",
"name": "mydomain\\mark",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2046359355.-7870067516287985870",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"blackListFileSuspicion": 1512300804528
},
"filterData": {
"sortInGroupValue": "-2046359355.-446319856563366924",
"groupByValue": "ransomfreetest.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-2046359355.-446319856563366924",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512314218832,
"totalSuspicions": 1
},
"ransomwareByCanaryFilesSuspicion": {
"potentialEvidence": [
"ransomwareByCanaryFilesEvidence"
],
"firstTimestamp": 1512313571594,
"totalSuspicions": 1
},
"connectingToBadReputationAddressSuspicion": {
"potentialEvidence": [
"hasMaliciousConnectionEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
}
},
"evidenceMap": {},
"totalPossibleResults": 13,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 13
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "myserver.com"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "isDownloadedFromInternet"
query_element_1_filter_2 = "firstExecutionOfDownloadedProcessEvidence"
query = json.dumps({"queryPath":[{"requestedType":"Process","filters":[{"facetName":query_element_1_filter,"values":[True]},{"facetName":query_element_1_filter_2,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout": 120000,"customFields":["elementDisplayName","commandLine","parentProcess","calculatedUser","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{
"data": {
"resultIdToElementDataMap": {
"-2046359355.-446319856563366924": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1512300801309"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512300801311"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"ransomfreetest.exe"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-6313743191401684913",
"name": "mydomain\\mark",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2046359355.-7870067516287985870",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"blackListFileSuspicion": 1512300804528
},
"filterData": {
"sortInGroupValue": "-2046359355.-446319856563366924",
"groupByValue": "ransomfreetest.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-2046359355.-446319856563366924",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512314218832,
"totalSuspicions": 1
},
"ransomwareByCanaryFilesSuspicion": {
"potentialEvidence": [
"ransomwareByCanaryFilesEvidence"
],
"firstTimestamp": 1512313571594,
"totalSuspicions": 1
},
"connectingToBadReputationAddressSuspicion": {
"potentialEvidence": [
"hasMaliciousConnectionEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
}
},
"evidenceMap": {},
"totalPossibleResults": 13,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 13
}
]
},
"status": "SUCCESS",
"message": ""
}
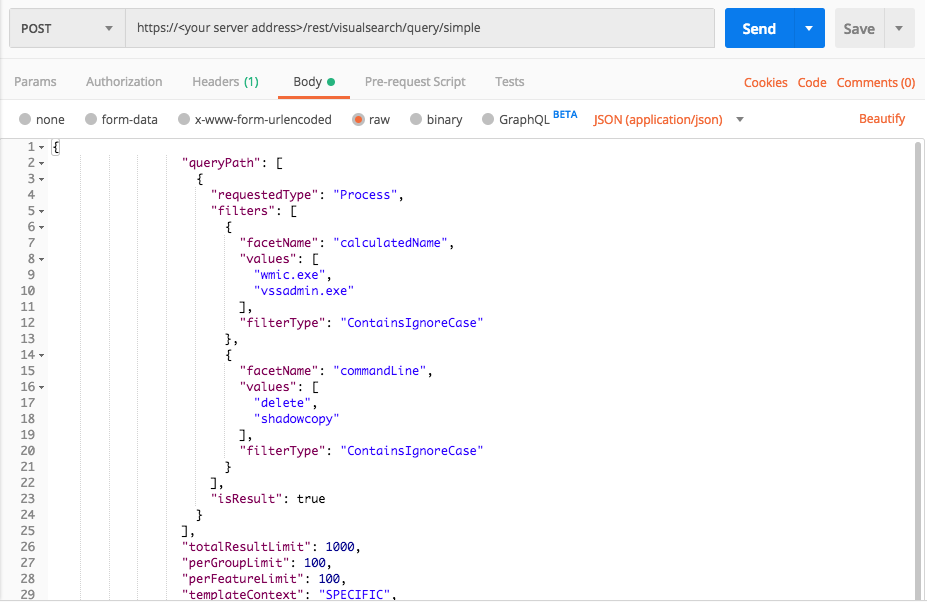
Find attempts to delete Windows shadowfiles
Use this request to find strange administrator behavior and potentially some ransomware.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"wmic.exe",
"vssadmin.exe"
],
"filterType":"ContainsIgnoreCase"
},
{
"facetName": "commandLine",
"values": [
"delete",
"shadowcopy"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser"
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"wmic.exe",
"vssadmin.exe"
],
"filterType": "ContainsIgnoreCase"
},
{
"facetName": "commandLine",
"values": [
"delete",
"shadowcopy"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "calculatedName"
query_element_1_filter_value_1 = "wmic.exe"
query_element_1_filter_value_2 = "vssadmin.exe"
query_element_1_filter_2 = "commandLine"
query_element_1_filter_2_value_1 = "delete"
query_element_1_filter_2_value_2 = "shadowcopy"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value_1,query_element_1_filter_value_2],"filterType":"ContainsIgnoreCase"},{"facetName":query_element_1_filter_2,"values":[query_element_1_filter_2_value_1,query_element_1_filter_2_value_2],"filterType":"ContainsIgnoreCase"}],"isResult": True}],"totalResultLimit": 1000,"perGroupLimit": 100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","commandLine","parentProcess","calculatedUser","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
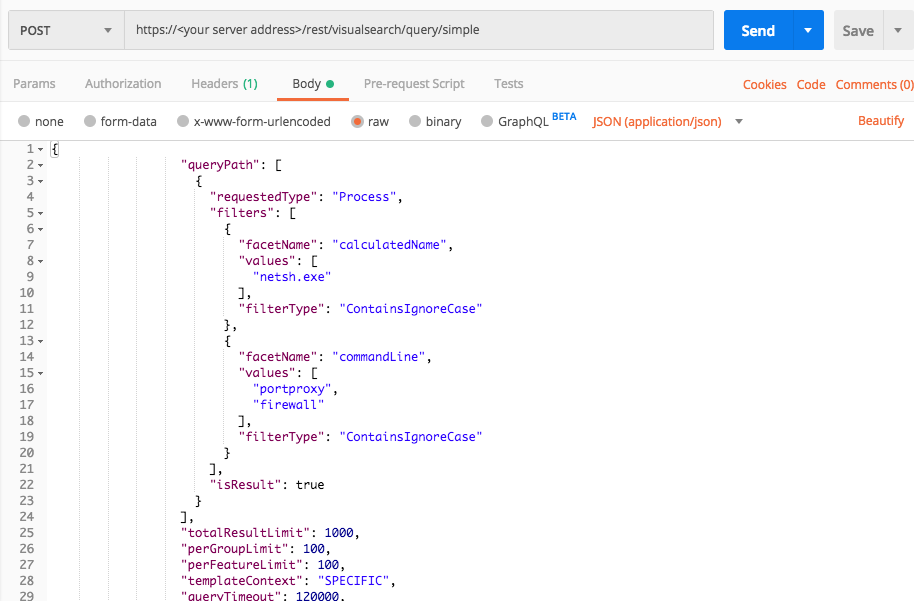
Find attempts to modify the firewall
Use this request to find active attackers who are pivoting through your network.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"netsh.exe"
],
"filterType":"ContainsIgnoreCase"
},
{
"facetName": "commandLine",
"values": [
"portproxy",
"firewall"
],
"filterType":"ContainsIgnoreCase"
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser"
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"668418323.553860106027913251": {
"simpleValues": {
"commandLine": {
"totalValues": 1,
"values": [
"C:\\WINDOWS\\system32\\netsh.exe advfirewall firewall add rule name=Dropbox dir=in action=allow \"program=C:\\Program Files (x86)\\Dropbox\\Client\\Dropbox.exe\" enable=yes profile=Any"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1497769904294"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1497769904502"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"netsh.exe"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-7984771045127340640",
"name": "user\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "668418323.-6176625369285990984",
"name": "dropbox.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"firewallHolePunchingSuspicion": 1497771345695
},
"filterData": {
"sortInGroupValue": "668418323.553860106027913251",
"groupByValue": "netsh.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "668418323.553860106027913251",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"firewallHolePunchingSuspicion": {
"potentialEvidence": [
"addFirewallRuleEvidence"
],
"firstTimestamp": 1495441086946,
"totalSuspicions": 14
}
},
"evidenceMap": {},
"totalPossibleResults": 14,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 14
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "calculatedName",
"values": [
"netsh.exe"
],
"filterType": "ContainsIgnoreCase"
},
{
"facetName": "commandLine",
"values": [
"portproxy",
"firewall"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"commandLine",
"parentProcess",
"calculatedUser",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"668418323.553860106027913251": {
"simpleValues": {
"commandLine": {
"totalValues": 1,
"values": [
"C:\\WINDOWS\\system32\\netsh.exe advfirewall firewall add rule name=Dropbox dir=in action=allow \"program=C:\\Program Files (x86)\\Dropbox\\Client\\Dropbox.exe\" enable=yes profile=Any"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1497769904294"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1497769904502"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"netsh.exe"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-7984771045127340640",
"name": "user\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "668418323.-6176625369285990984",
"name": "dropbox.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"firewallHolePunchingSuspicion": 1497771345695
},
"filterData": {
"sortInGroupValue": "668418323.553860106027913251",
"groupByValue": "netsh.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "668418323.553860106027913251",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"firewallHolePunchingSuspicion": {
"potentialEvidence": [
"addFirewallRuleEvidence"
],
"firstTimestamp": 1495441086946,
"totalSuspicions": 14
}
},
"evidenceMap": {},
"totalPossibleResults": 14,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 14
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "calculatedName"
query_element_1_filter_value = "netsh.exe"
query_element_1_filter_2 = "commandLine"
query_element_1_filter_2_value_1 = "portproxy"
query_element_1_filter_2_value_2 = "firewall"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"ContainsIgnoreCase"},{"facetName":query_element_1_filter_2,"values":[query_element_1_filter_2_value_1,query_element_1_filter_2_value_2],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit": 1000,"perGroupLimit":100,"perFeatureLimit": 100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","commandLine","parentProcess","calculatedUser","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "batchId": -1312043715, "actionType": "FileSearchStart", "actionArguments": { "@class": "com.cybereason.configuration.models.FileSearchParameters", "filters": [ { "fieldName": "fileName", "values": [ "ShadowAttack.exe" ], "operator": "Equals" } ], "maxAnswers": 20 }, "globalStats": { "stats": { "Pending": 0, "partialResponse": 0, "AbortTimeout": 0, "EndedWithSensorTimeout": 0, "UnauthorizedUser": 0, "FailedSendingToServer": 0, "GettingChunks": 0, "NewerInstalled": 0, "SendingMsi": 0, "None": 52, "MsiSendFail": 0, "EndedWithInvalidParam": 0, "Failed": 0, "InProgress": 0, "Disconnected": 0, "Aborted": 0, "FailedSending": 0, "MsiFileCorrupted": 0, "UnknownProbe": 0, "NotSupported": 0, "Primed": 0, "ChunksRequired": 0, "ProbeRemoved": 0, "Started": 0, "EndedWithTooManySearches": 0, "TimeoutSending": 0, "InvalidState": 0, "Timeout": 0, "EndedWithUnknownError": 0, "AlreadyUpdated": 0, "EndedWithTooManyResults": 0, "Succeeded": 0 } }, "finalState": false, "totalNumberOfProbes": 52, "initiatorUser": "[email protected]", "startTime": 1524400763922, "aborterUser": null, "abortTime": 0, "abortTimeout": false, "abortHttpStatusCode": null }