Find Malicious Use of Privilege Escalation
Use these queries to find examples of malicious behavior occurring in the privilege escalation stage of an attack.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
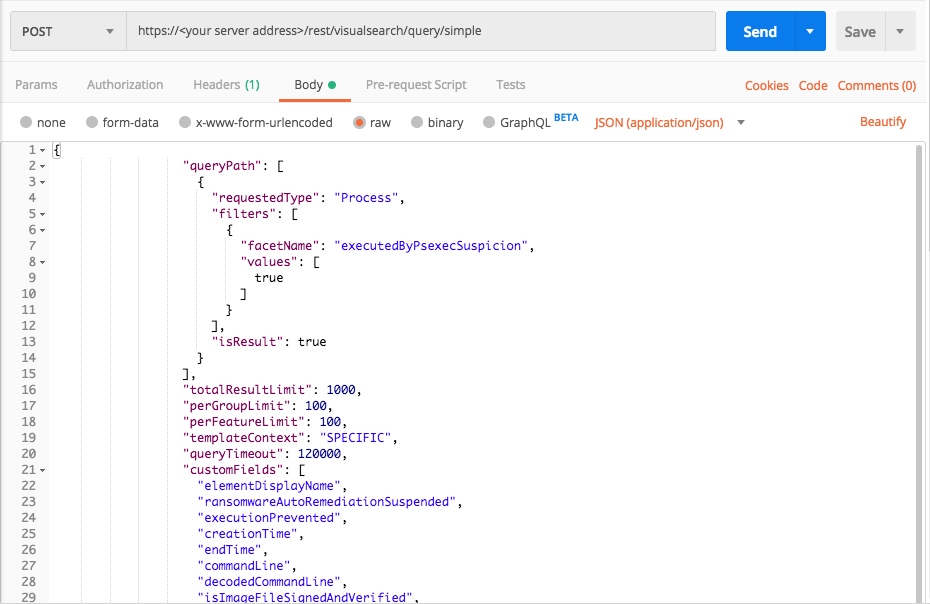
Malicious use of Psexec
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName":"executedByPsexecSuspicion",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-1208764281.8567501564444993905": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"cmd\" "
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1500641612039"
]
},
"pid": {
"totalValues": 1,
"values": [
"2140"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"cmd.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-5441679353483096598",
"name": "\\",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1208764281.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1208764281.-4813929778986701641",
"name": "psexesvc.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1208764281.-7927278256478080039",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"executedByPsexecSuspicion": 1500641710334
},
"filterData": {
"sortInGroupValue": "-1208764281.8567501564444993905",
"groupByValue": "cmd.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "-1208764281.8567501564444993905",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"executedByPsexecSuspicion": {
"potentialEvidence": [
"parentPsexecEvidence",
"unknownUnsignedEvidence"
],
"firstTimestamp": 1500641710334,
"totalSuspicions": 2
}
},
"evidenceMap": {},
"totalPossibleResults": 2,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 2
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "executedByPsexecSuspicion",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
"iconBase64"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-1208764281.8567501564444993905": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"cmd\" "
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1500641612039"
]
},
"pid": {
"totalValues": 1,
"values": [
"2140"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"cmd.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-5441679353483096598",
"name": "\\",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1208764281.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1208764281.-4813929778986701641",
"name": "psexesvc.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1208764281.-7927278256478080039",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"executedByPsexecSuspicion": 1500641710334
},
"filterData": {
"sortInGroupValue": "-1208764281.8567501564444993905",
"groupByValue": "cmd.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "-1208764281.8567501564444993905",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"executedByPsexecSuspicion": {
"potentialEvidence": [
"parentPsexecEvidence",
"unknownUnsignedEvidence"
],
"firstTimestamp": 1500641710334,
"totalSuspicions": 2
}
},
"evidenceMap": {},
"totalPossibleResults": 2,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 2
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "executedByPsexecSuspicion"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values": [True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext": "SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-1208764281.8567501564444993905": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "\"cmd\" " ] }, "creationTime": { "totalValues": 1, "values": [ "1500641612039" ] }, "pid": { "totalValues": 1, "values": [ "2140" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "cmd.exe" ] }, "productType": { "totalValues": 1, "values": [ "SHELL" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.-5441679353483096598", "name": "\\", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-1208764281.1198775089551518743", "name": null, "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-1208764281.-4813929778986701641", "name": "psexesvc.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-1208764281.-7927278256478080039", "name": "cmd.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": { "executedByPsexecSuspicion": 1500641710334 }, "filterData": { "sortInGroupValue": "-1208764281.8567501564444993905", "groupByValue": "cmd.exe" }, "isMalicious": false, "suspicionCount": 1, "guidString": "-1208764281.8567501564444993905", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "executedByPsexecSuspicion": { "potentialEvidence": [ "parentPsexecEvidence", "unknownUnsignedEvidence" ], "firstTimestamp": 1500641710334, "totalSuspicions": 2 } }, "evidenceMap": {}, "totalPossibleResults": 2, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 2 } ] }, "status": "SUCCESS", "message": "" }
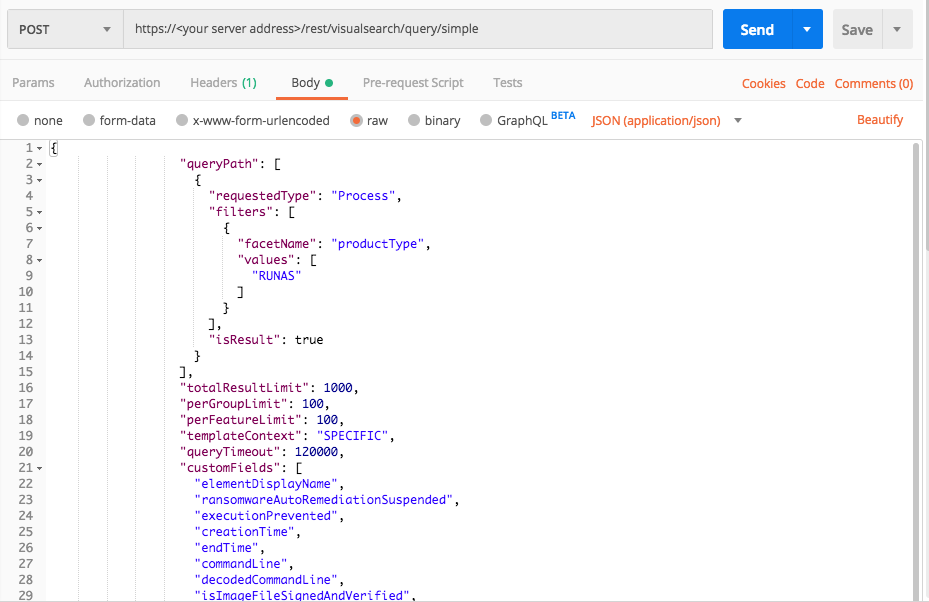
Attempt to run as processes
Use this request to find processes with a RunAs product type.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"RUNAS"
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
"iconBase64"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"RUNAS"
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
"iconBase64"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "productType"
query_element_1_filter_value = "RUNAS"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))