Find Instances of Malicious Communication
Use the API to find examples of malicious communication.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
DNS requests and connections to unknown domains
Use this request to find examples of DNS requests or connections to unknown domains.
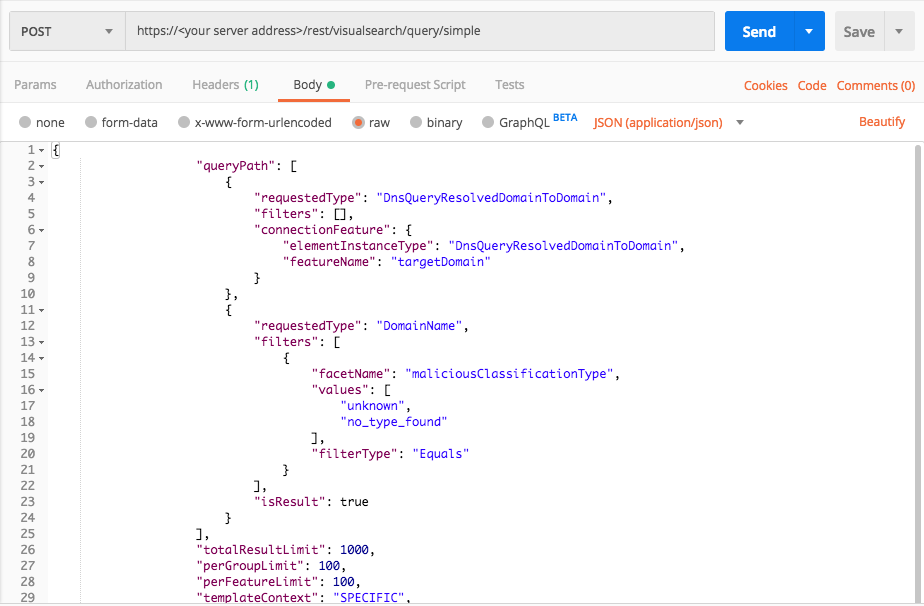
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":
[
{
"requestedType":"DnsQueryResolvedDomainToDomain",
"filters":[],
"connectionFeature": {
"elementInstanceType":"DnsQueryResolvedDomainToDomain",
"featureName":"targetDomain"
}
},
{
"requestedType":"DomainName",
"filters": [
{
"facetName":"maliciousClassificationType",
"values": ["unknown","no_type_found"],
"filterType":"Equals"
}
],
"isResult": true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"maliciousClassificationType",
"isInternalDomain",
"everResolvedDomain",
"everResolvedSecondLevelDomain",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "DnsQueryResolvedDomainToDomain", "filters": [], "connectionFeature": { "elementInstanceType": "DnsQueryResolvedDomainToDomain", "featureName": "targetDomain" } }, { "requestedType": "DomainName", "filters": [ { "facetName": "maliciousClassificationType", "values": [ "unknown", "no_type_found" ], "filterType": "Equals" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "maliciousClassificationType", "isInternalDomain", "everResolvedDomain", "everResolvedSecondLevelDomain", "elementDisplayName" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "myserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "DnsQueryResolvedDomainToDomain" linking_element = "DnsQueryResolvedDomainToDomain" linking_feature = "targetDomain" query_element_2 = "DomainName" query_element_2_filter = "maliciousClassificationType" query_element_2_filter_1 = "unknown" query_element_2_filter_2 = "no_type_found" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[query_element_2_filter_1,query_element_2_filter_2],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["maliciousClassificationType","isInternalDomain","everResolvedDomain","everResolvedSecondLevelDomain","elementDisplayName"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content)print(json.dumps(your_response, indent=4, sort_keys=True))
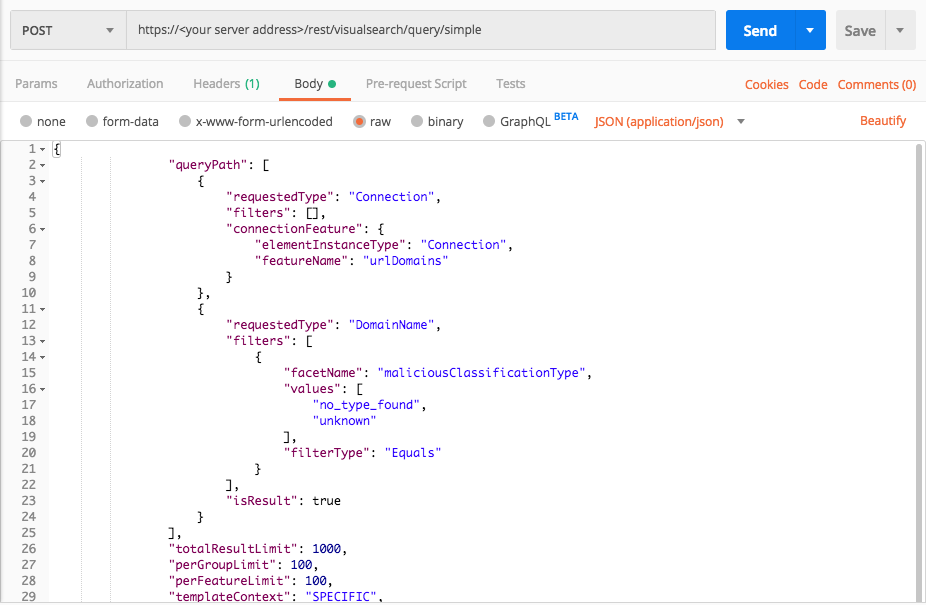
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{ "requestedType":"Connection",
"filters":[],
"connectionFeature": {
"elementInstanceType":"Connection",
"featureName":"urlDomains"
}
},
{
"requestedType":"DomainName",
"filters": [
{
"facetName":"maliciousClassificationType",
"values": ["no_type_found","unknown"],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"maliciousClassificationType",
"isInternalDomain",
"everResolvedDomain",
"everResolvedSecondLevelDomain",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Connection", "filters": [], "connectionFeature": { "elementInstanceType": "Connection", "featureName": "urlDomains" } }, { "requestedType": "DomainName", "filters": [ { "facetName": "maliciousClassificationType", "values": [ "no_type_found", "unknown" ], "filterType": "Equals" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "maliciousClassificationType", "isInternalDomain", "everResolvedDomain", "everResolvedSecondLevelDomain", "elementDisplayName" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "myserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Connection" linking_element = "Connection" linking_feature = "urlDomains" query_element_2 = "DomainName" query_element_2_filter = "maliciousClassificationType" query_element_2_filter_value_1 = "unknown" query_element_2_filter_value_2 = "no_type_found" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[query_element_2_filter_value_1,query_element_2_filter_value_2],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["maliciousClassificationType","isInternalDomain","everResolvedDomain","everResolvedSecondLevelDomain","elementDisplayName"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
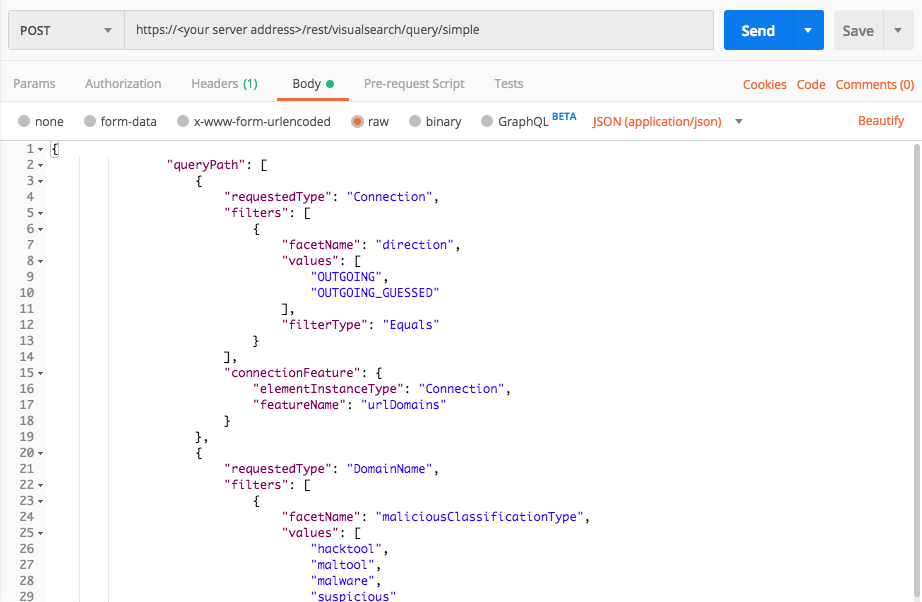
Outbound communication to a hostile domain
Use this request to find communications to domains classified as hostile.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Connection",
"filters": [
{
"facetName":"direction",
"values":["OUTGOING","OUTGOING_GUESSED"],
"filterType":"Equals"
}
],
"connectionFeature": {
"elementInstanceType":"Connection",
"featureName":"urlDomains"
}
},
{
"requestedType": "DomainName",
"filters": [
{
"facetName":"maliciousClassificationType",
"values": ["hacktool","maltool","malware","suspicious"],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"maliciousClassificationType",
"isInternalDomain",
"everResolvedDomain",
"everResolvedSecondLevelDomain",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Connection", "filters": [ { "facetName": "direction", "values": [ "OUTGOING", "OUTGOING_GUESSED" ], "filterType": "Equals" } ], "connectionFeature": { "elementInstanceType": "Connection", "featureName": "urlDomains" } }, { "requestedType": "DomainName", "filters": [ { "facetName": "maliciousClassificationType", "values": [ "hacktool", "maltool", "malware", "suspicious" ], "filterType": "Equals" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "maliciousClassificationType", "isInternalDomain", "everResolvedDomain", "everResolvedSecondLevelDomain", "elementDisplayName" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Connection" query_element_1_filter = "direction" query_element_1_filter_value_1 = "OUTGOING" query_element_1_filter_value_2 = "OUTGOING_GUESSED" linking_element = "Connection" linking_feature = "urlDomains" query_element_2 = "DomainName" query_element_2_filter = "maliciousClassificationType" query_element_2_filter_value_1 = "hacktool" query_element_2_filter_value_2 = "maltool" query_element_2_filter_value_3 = "malware" query_element_2_filter_value_4 = "suspicious" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value_1,query_element_1_filter_value_2],"filterType":"Equals"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[query_element_2_filter_value_1,query_element_2_filter_value_2,query_element_2_filter_value_3,query_element_2_filter_value_4],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["maliciousClassificationType","isInternalDomain","everResolvedDomain","everResolvedSecondLevelDomain","elementDisplayName"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
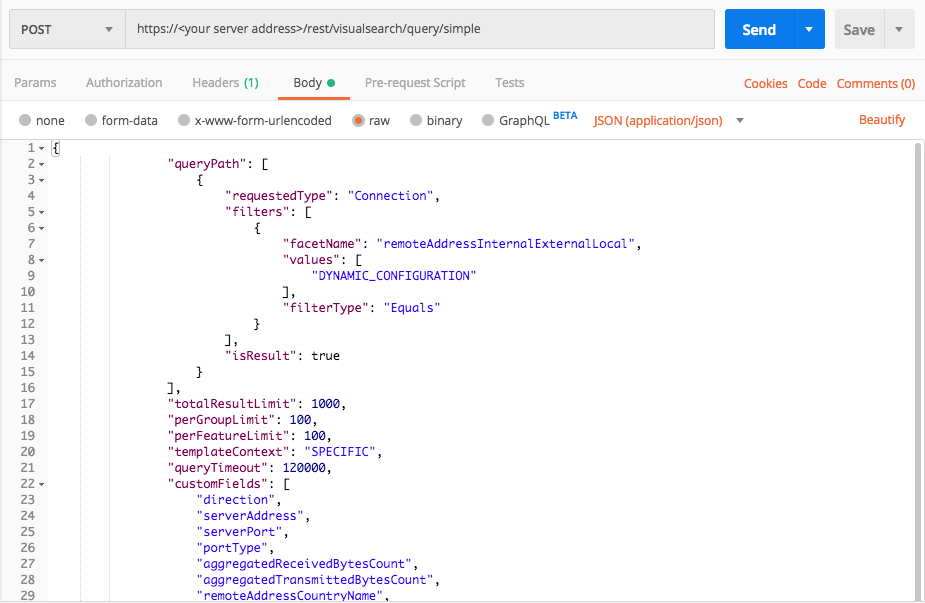
Communication with dynamic DNS servers
Use this request to find instances of communication with servers that use a dynamic DNS configuration.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Connection",
"filters": [
{
"facetName":
"remoteAddressInternalExternalLocal",
"values": ["DYNAMIC_CONFIGURATION"],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"direction",
"serverAddress",
"serverPort",
"portType",
"aggregatedReceivedBytesCount",
"aggregatedTransmittedBytesCount",
"remoteAddressCountryName",
"accessedByMalwareEvidence",
"ownerMachine",
"ownerProcess",
"dnsQuery",
"calculatedCreationTime",
"endTime",
"elementDisplayName"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Connection", "filters": [ { "facetName": "remoteAddressInternalExternalLocal", "values": [ "DYNAMIC_CONFIGURATION" ], "filterType": "Equals" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "direction", "serverAddress", "serverPort", "portType", "aggregatedReceivedBytesCount", "aggregatedTransmittedBytesCount", "remoteAddressCountryName", "accessedByMalwareEvidence", "ownerMachine", "ownerProcess", "dnsQuery", "calculatedCreationTime", "endTime", "elementDisplayName" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Connection" query_element_1_filter = "remoteAddressInternalExternalLocal" query_element_1_filter_value = "DYNAMIC_CONFIGURATION" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["direction","serverAddress","serverPort","portType","aggregatedReceivedBytesCount","aggregatedTransmittedBytesCount","remoteAddressCountryName","accessedByMalwareEvidence","ownerMachine","ownerProcess","dnsQuery","calculatedCreationTime","endTime","elementDisplayName"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))