MITRE ATT&CK Techniques
Use the API to find examples of different MITRE ATT&CK techniques.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
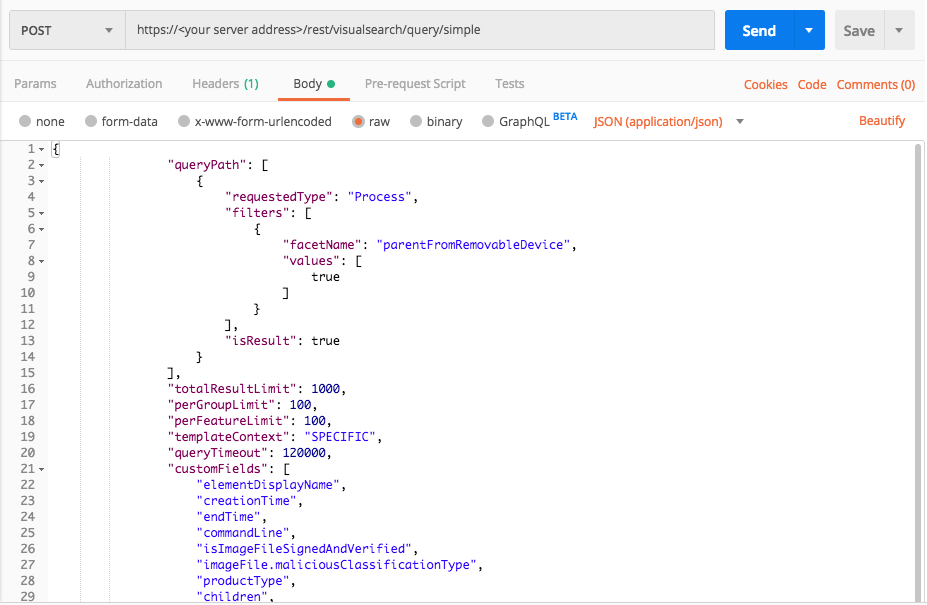
Initial Access: Replication Through Removable Media
Use this queries to find an example of the MITRE ATT&CK technique Initial Access: Replication Through Removable Media, where a process originates or is launched through removable media devices.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"parentFromRemovableDevice",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "parentFromRemovableDevice", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "parentFromRemovableDevice" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
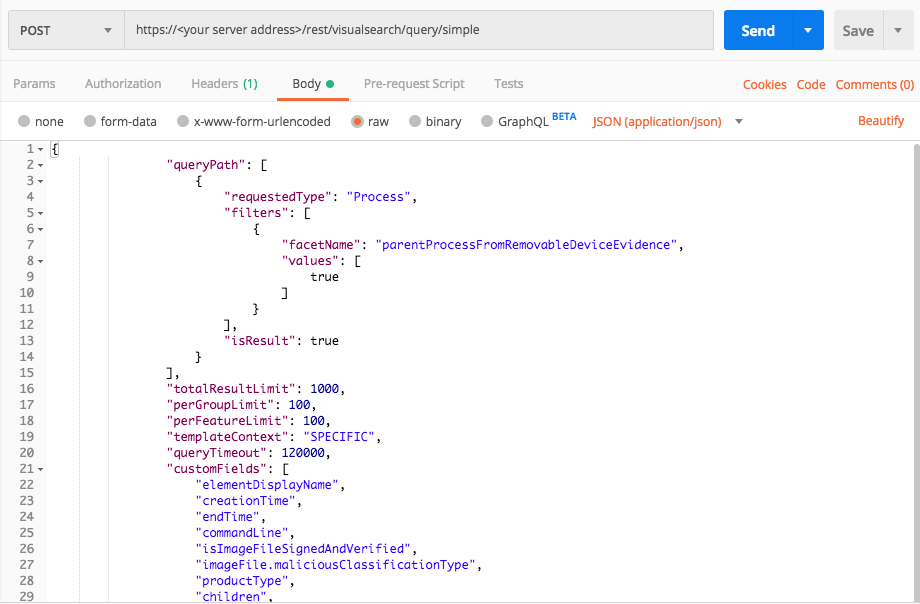
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"parentProcessFromRemovableDeviceEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "parentProcessFromRemovableDeviceEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "parentProcessFromRemovableDeviceEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
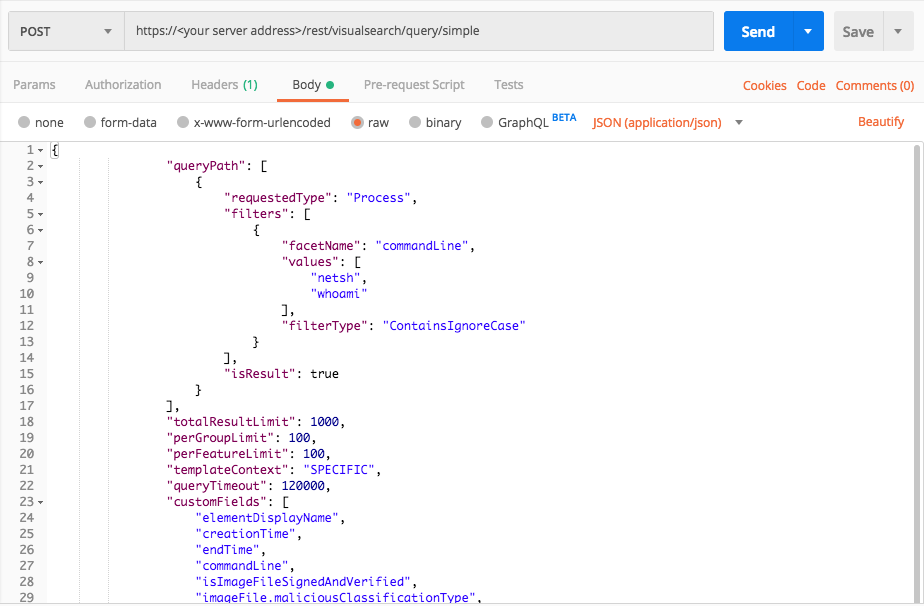
Execution: Command Line Interface
Use this query to find examples of the MITRE ATT&CK technique Execution: Command Line Interface, where you search for specific command lines run in your environment. This example uses a specific command but you can use any command line you want.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"commandLine",
"values": ["netsh","whoami"],
"filterType":"ContainsIgnoreCase"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "commandLine", "values": [ "netsh", "whoami" ], "filterType": "ContainsIgnoreCase" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "commandLine" query_element_1_filter_value_1 = "netsh" query_element_1_filter_value_2 = "whoami" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value_1,query_element_1_filter_value_2],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
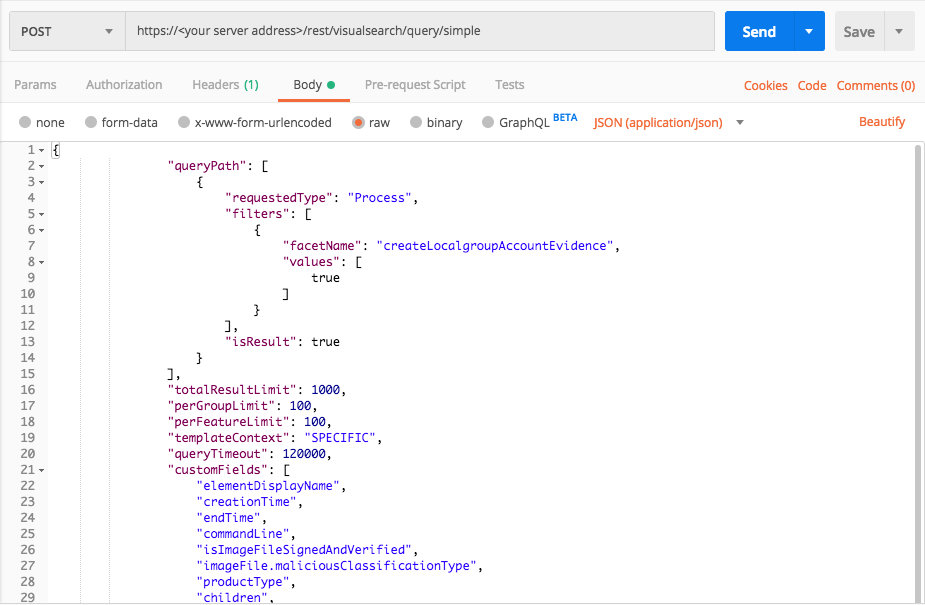
Persistence: Create Account
Use these queries to find examples of the MITRE ATT&CK technique Persistence: Create Account.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"createLocalgroupAccountEvidence",
"values":[true],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "createLocalgroupAccountEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "createLocalgroupAccountEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
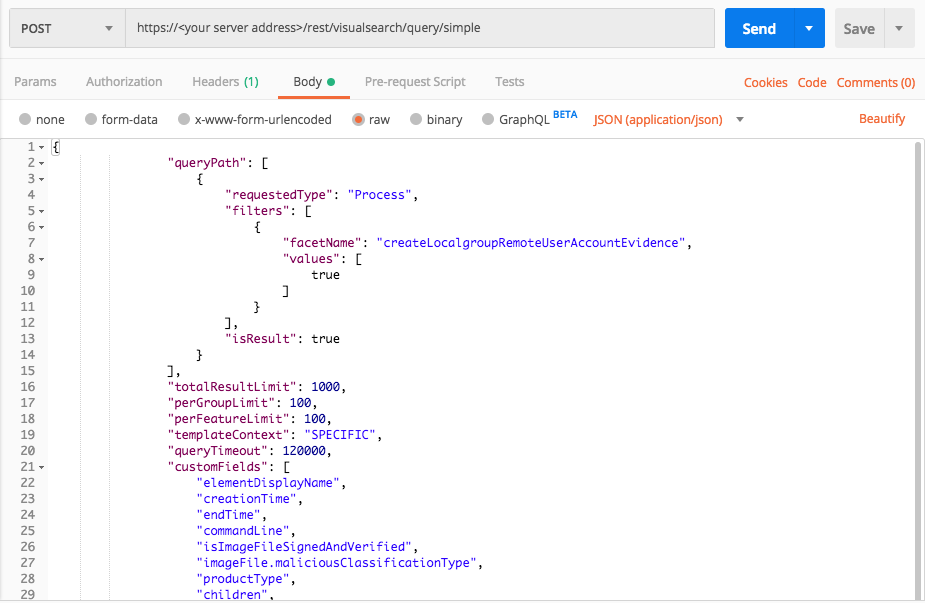
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"createLocalgroupRemoteUserAccountEvidence",
"values":[true],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime","commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType","children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "createLocalgroupRemoteUserAccountEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "createLocalgroupRemoteUserAccountEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 3:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"createLocalgroupAccountEvidence",
"values": [true],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
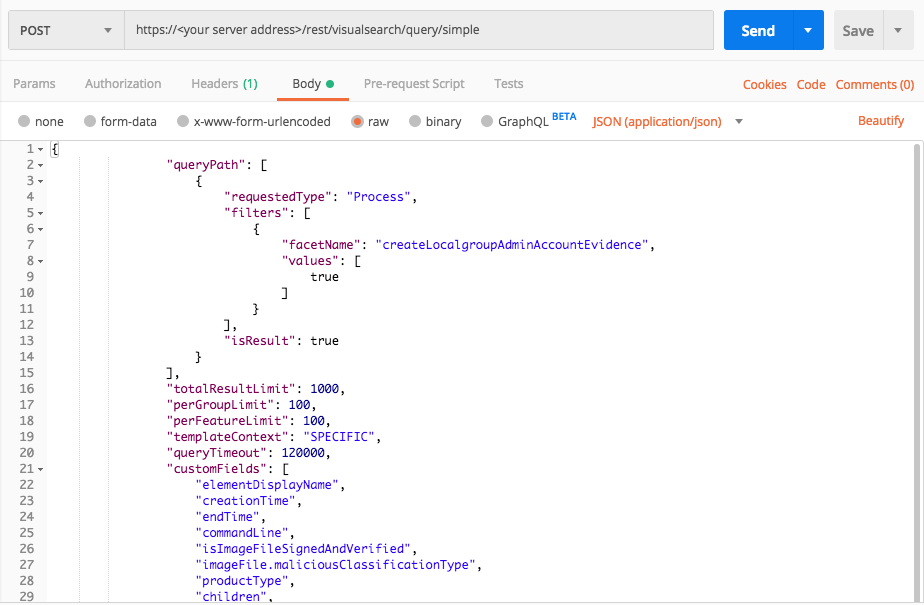
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "createLocalgroupAdminAccountEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "createLocalgroupAdminAccountEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Defense Evasion: Masquerading
Use these queries to find examples of the MITRE ATT&CK techniques Defense Evasion: Masquerading, where a process hides as a different type of process.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
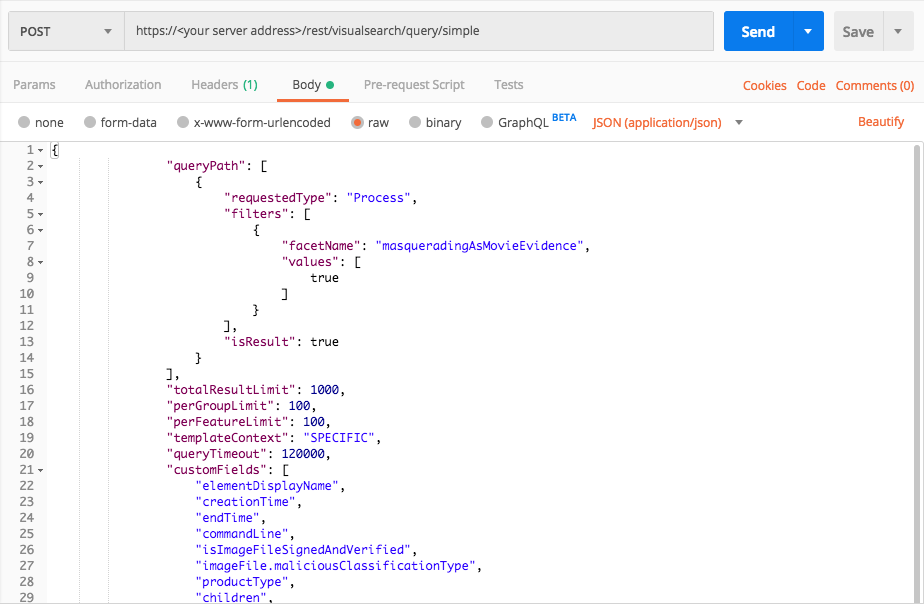
"facetName":"masqueradingAsMovieEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "masqueradingAsMovieEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "masqueradingAsMovieEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters":[
{
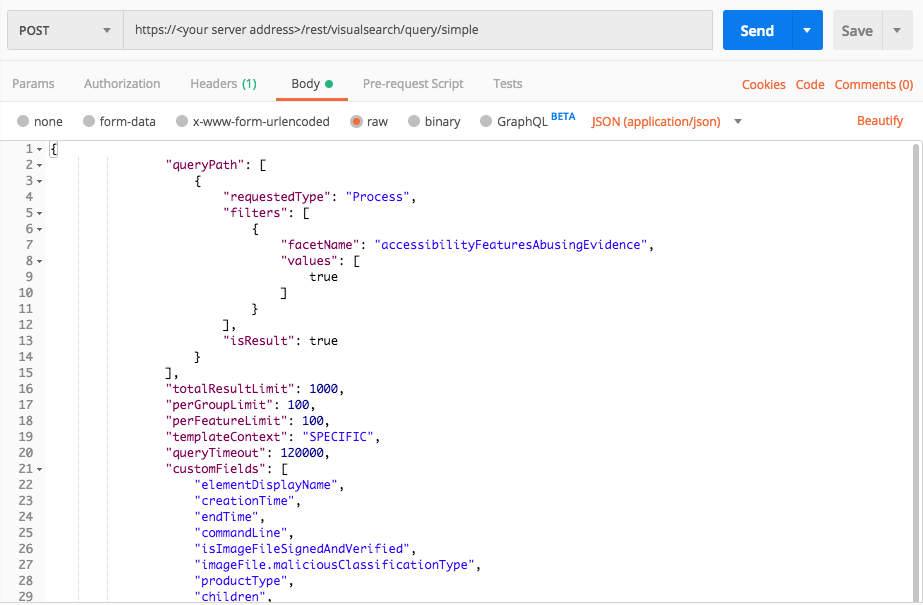
"facetName":"accessibilityFeaturesAbusingEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}
}
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "accessibilityFeaturesAbusingEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "accessibilityFeaturesAbusingEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 3:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
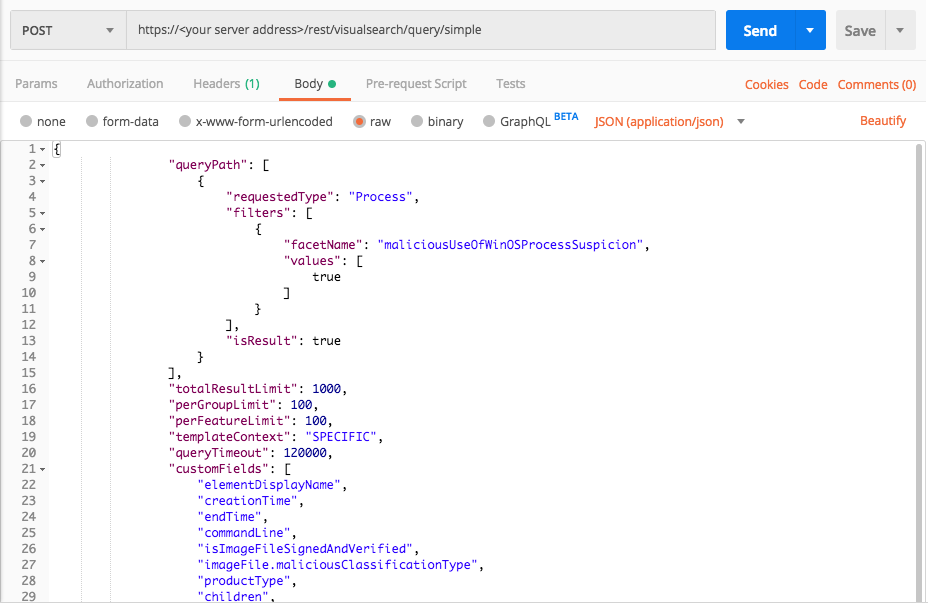
"facetName":"maliciousUseOfWinOSProcessSuspicion",
"values": [true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "maliciousUseOfWinOSProcessSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "maliciousUseOfWinOSProcessSuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Credential Access: Credential Dumping
Use these queries to find examples of the MITRE ATT&CK technique Credential Access: Credential Dumping, where processes perform a dump of credential information.
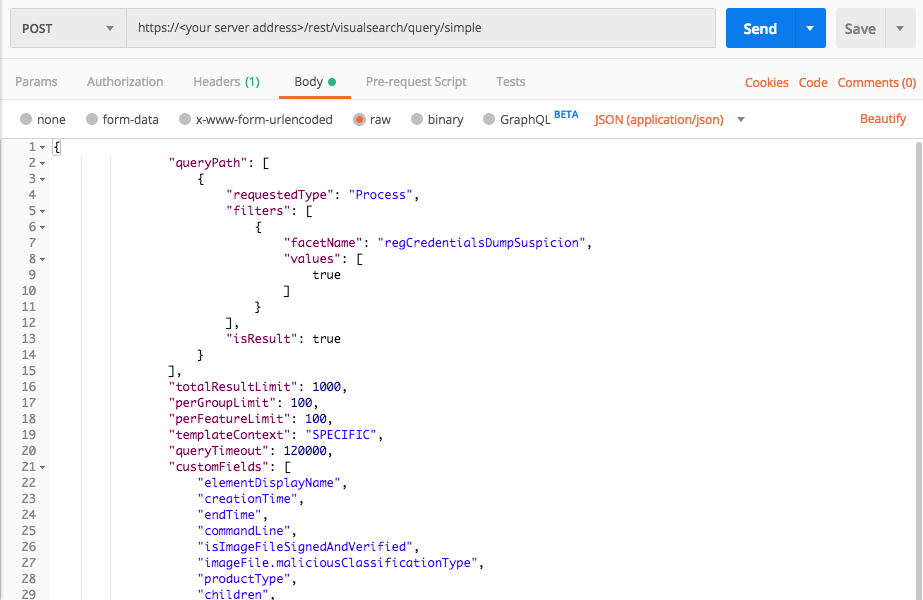
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"regCredentialsDumpSuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "regCredentialsDumpSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "regCredentialsDumpSuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
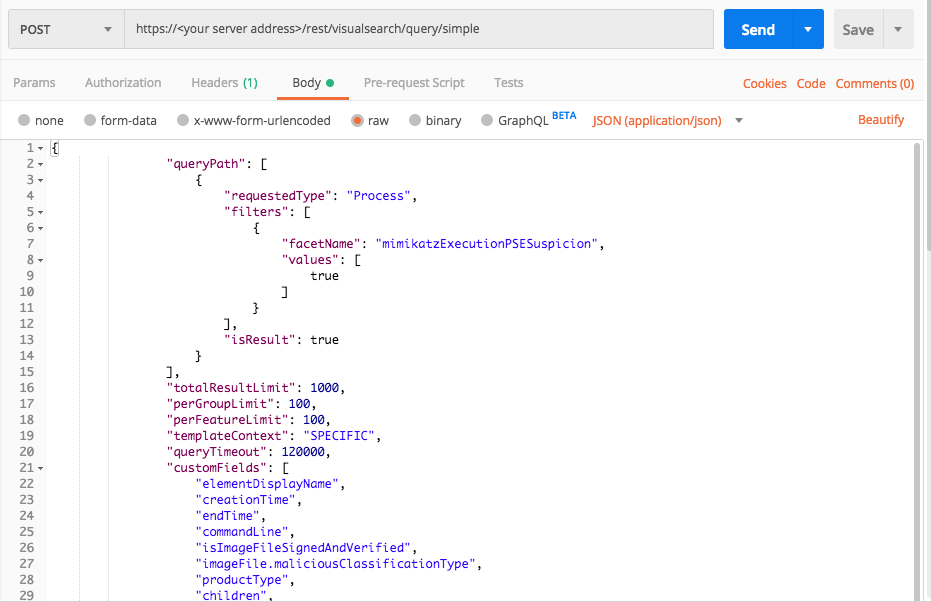
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"mimikatzExecutionPSESuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "mimikatzExecutionPSESuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "mimikatzExecutionPSESuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
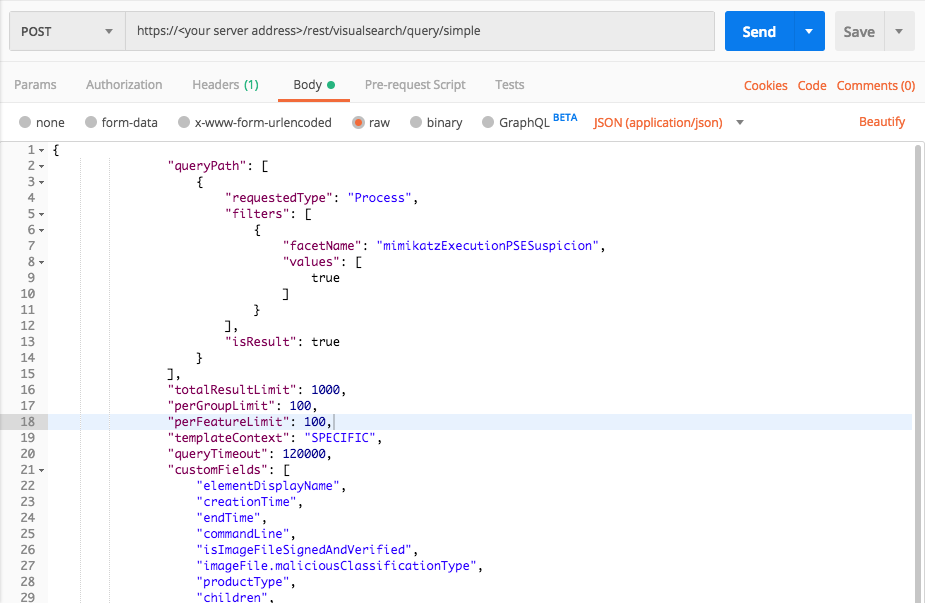
Query 3:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"mimikatzExecutionPSESuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "mimikatzExecutionPSESuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "mimikatzExecutionPSESuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
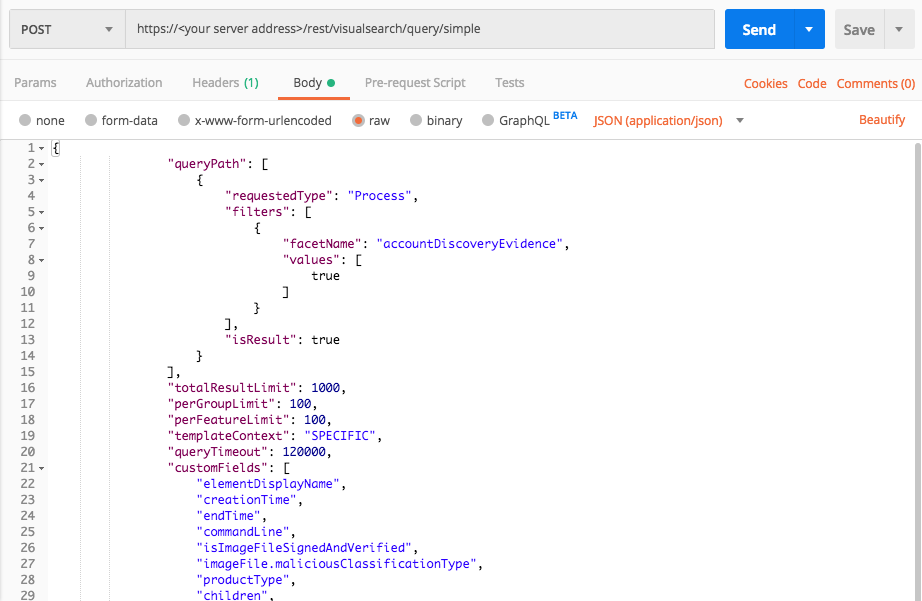
Discovery: Account Discovery
Use these queries to discover evidence of the MITRE ATT&CK technique Discovery: Account Discovery, where an attacker tries to discover information about accounts on a machine.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"accountDiscoveryEvidence",
"values": [true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "accountDiscoveryEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "nKnAJmBSF0i9" server = "workshop.cybereason.net" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "accountDiscoveryEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
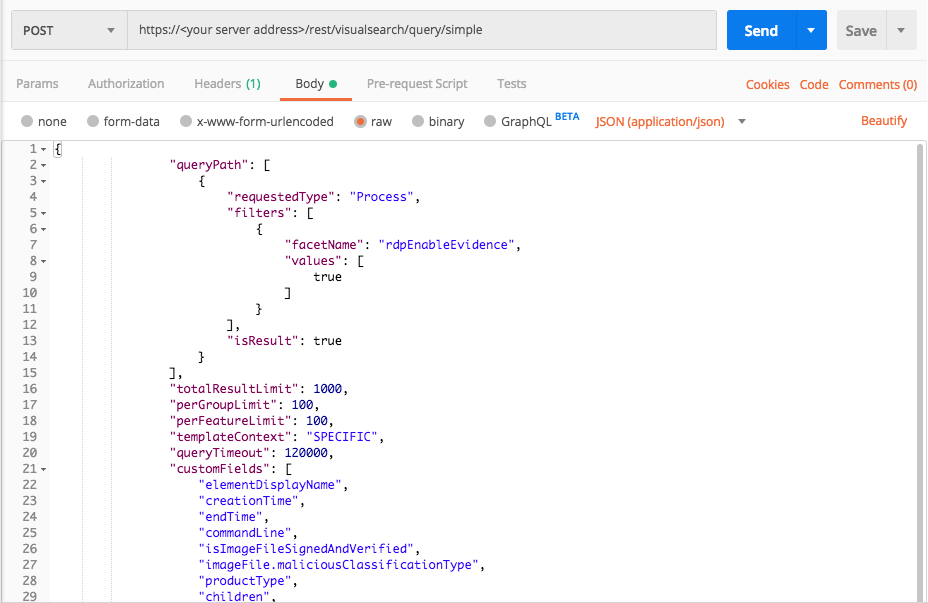
Lateral Movement: Remote Desktop Protocol
Use these queries to help you find evidence of the MITRE ATT&CK technique Lateral Movement: Remote Desktop Protocol where an attacker uses the Remote Desktop program to move throughout a network.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"rdpEnableEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "rdpEnableEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "myserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "rdpEnableEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
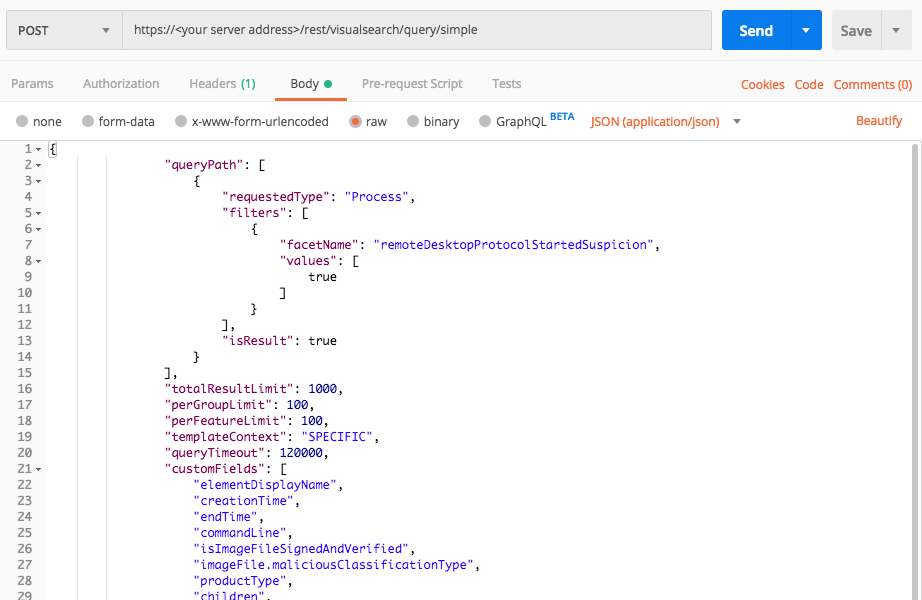
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"remoteDesktopProtocolStartedSuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "remoteDesktopProtocolStartedSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "remoteDesktopProtocolStartedSuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
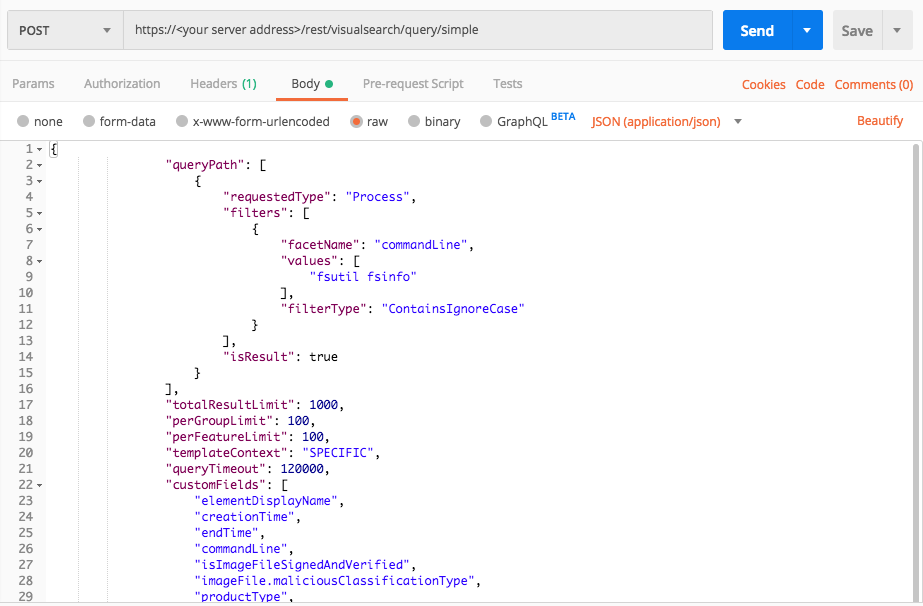
Collection: Local File System
Use this query to find evidence of the MITRE ATT&CK technique Collection: Local File System.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"commandLine",
"values":["fsutil fsinfo"],
"filterType":"ContainsIgnoreCase"
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "commandLine", "values": [ "fsutil fsinfo" ], "filterType": "ContainsIgnoreCase" } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "commandLine" query_element_1_filter_value_1 = "fsutil" query_element_1_filter_value_2 = "fsinfo" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value_1, query_element_1_filter_value_2],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
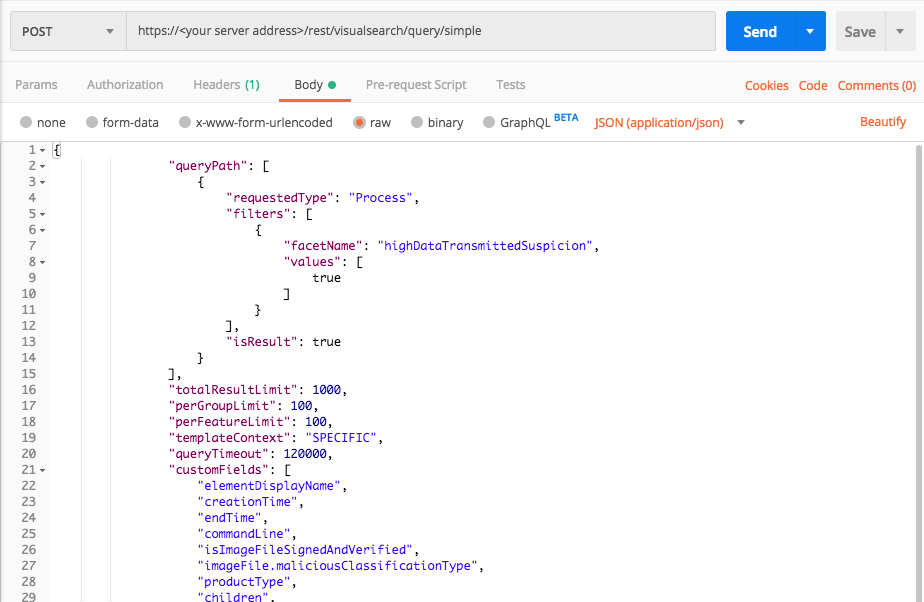
Exfiltration: Exfiltration over Command and Control Channel
Use these queries to find examples of the MITRE ATT&CK technique Exfiltration: Exfiltration over Command and Control Channel where an attacker uses a command and control channel to move data from a compromised environment.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"highDataTransmittedSuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64
ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "highDataTransmittedSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64\n\t\t \t\t\t\t\t\t\t\transomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request query_element_1 = "Process" query_element_1_filter = "highDataTransmittedSuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
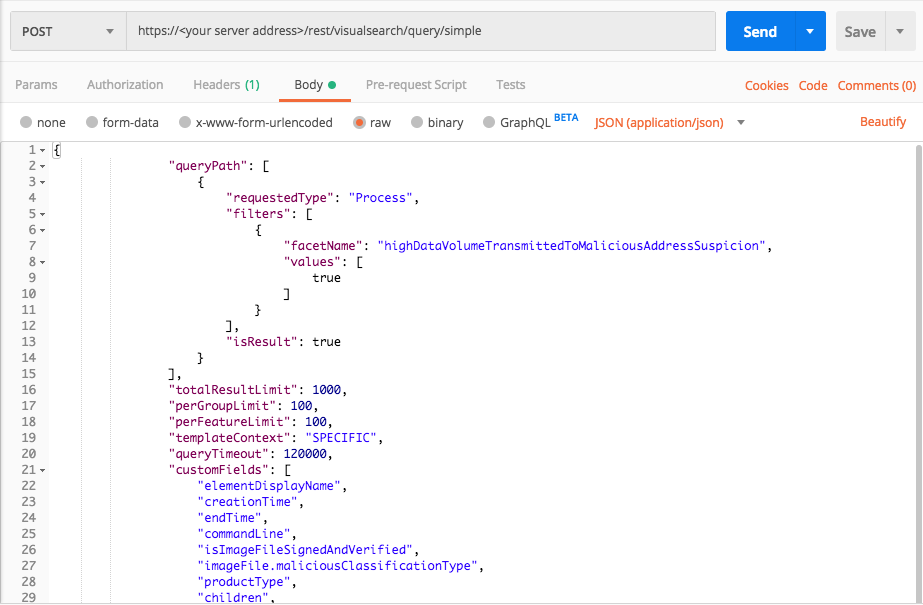
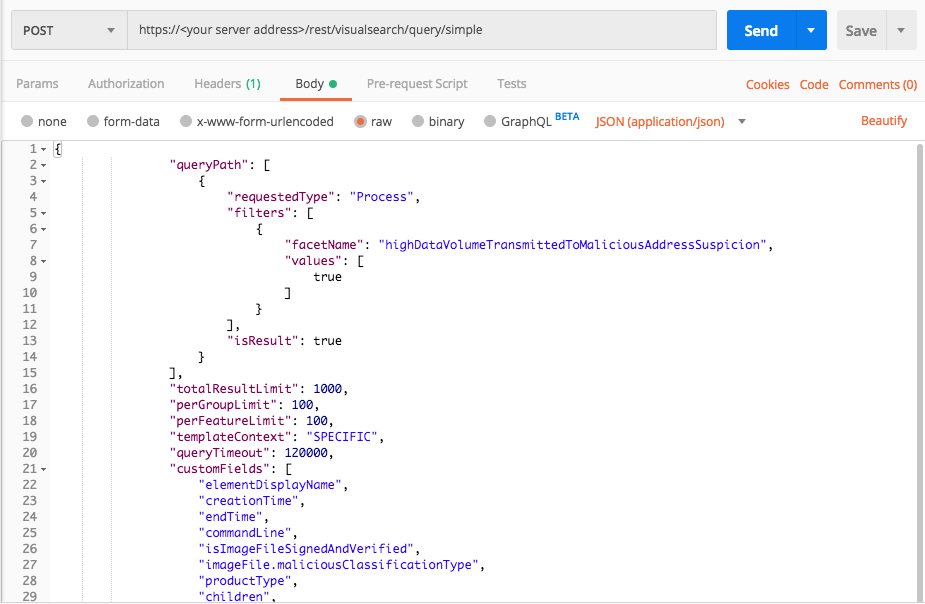
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType":"Process",
"filters": [
{
"facetName":"highDataVolumeTransmittedToMaliciousAddressSuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "highDataVolumeTransmittedToMaliciousAddressSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "highDataVolumeTransmittedToMaliciousAddressSuspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
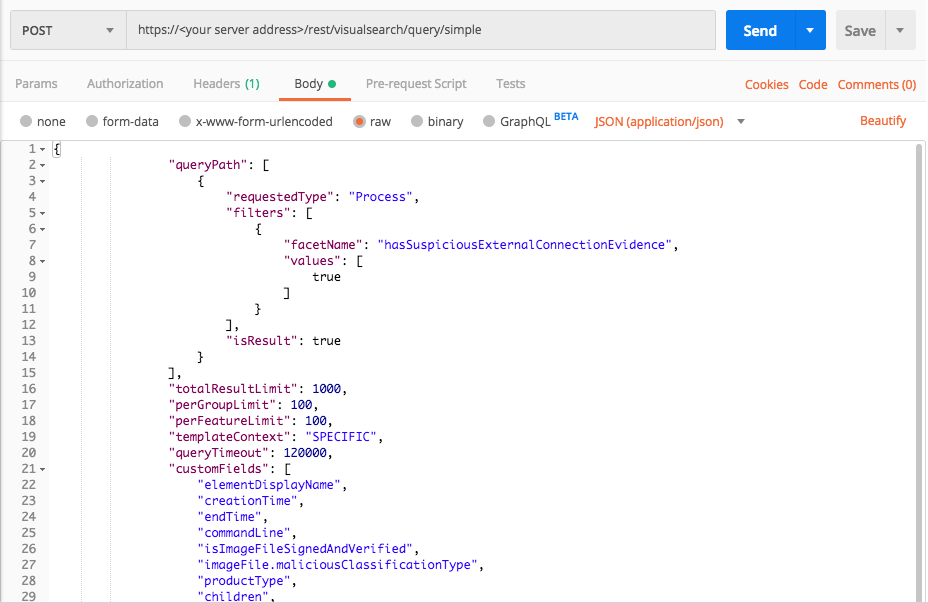
Query 3:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters": [
{
"facetName":"hasSuspiciousExternalConnectionEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "hasSuspiciousExternalConnectionEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "hasSuspiciousExternalConnectionEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Command and Control: Remote File Copy
Use these queries to find evidence of the MITRE ATT&CK technique Command and Control: Remote File Copy, where an attacker copies files to a remote location using command and control.
Query 1:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters": [
{
"facetName":"uncommonUseOfRundll32Suspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields": [
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "uncommonUseOfRundll32Suspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) endpoint_url = "/rest/visualsearch/query/simple" # Request URL api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "uncommonUseOfRundll32Suspicion" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 2:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters":[
{
"facetName":"ftpCommunicationEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields":[
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "ftpCommunicationEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "ftpCommunicationEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 3:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters":[
{
"facetName":"ftpDescendantofSuspiciousProcessEvidence",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields":[
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "ftpDescendantofSuspiciousProcessEvidence", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests import json # Login information username = "[email protected]" password = "mypassword" server = "yourserver.com" port = "443" data = { "username": username, "password": password } headers = {"Content-Type": "application/json"} base_url = "https://" + server + ":" + port login_url = base_url + "/login.html" session = requests.session() login_response = session.post(login_url, data=data, verify=True) print (login_response.status_code) print (session.cookies.items()) # Request URL endpoint_url = "/rest/visualsearch/query/simple" api_url = base_url + endpoint_url # These are the variables that represent different fields in the request. query_element_1 = "Process" query_element_1_filter = "ftpDescendantofSuspiciousProcessEvidence" query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]}) api_headers = {'Content-Type':'application/json'} api_response = session.request("POST", api_url, data=query, headers=api_headers) your_response = json.loads(api_response.content) print(json.dumps(your_response, indent=4, sort_keys=True))
Query 4:
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters":[
{
"facetName":"highDataVolumeTransmittedToMaliciousAddressSuspicion",
"values":[true]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields":[
"elementDisplayName",
"creationTime",
"endTime",
"commandLine",
"isImageFileSignedAndVerified",
"imageFile.maliciousClassificationType",
"productType",
"children",
"parentProcess",
"ownerMachine",
"calculatedUser",
"imageFile",
"imageFile.sha1String",
"imageFile.md5String",
"imageFile.companyName",
"imageFile.productName",
"iconBase64",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"isWhiteListClassification",
"matchedWhiteListRuleIds"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "queryPath": [ { "requestedType": "Process", "filters": [ { "facetName": "highDataVolumeTransmittedToMaliciousAddressSuspicion", "values": [ true ] } ], "isResult": true } ], "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "templateContext": "SPECIFIC", "queryTimeout": 120000, "customFields": [ "elementDisplayName", "creationTime", "endTime", "commandLine", "isImageFileSignedAndVerified", "imageFile.maliciousClassificationType", "productType", "children", "parentProcess", "ownerMachine", "calculatedUser", "imageFile", "imageFile.sha1String", "imageFile.md5String", "imageFile.companyName", "imageFile.productName", "iconBase64", "ransomwareAutoRemediationSuspended", "executionPrevented", "isWhiteListClassification", "matchedWhiteListRuleIds" ] }
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "highDataVolumeTransmittedToMaliciousAddressSuspicion"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","creationTime","endTime","commandLine","isImageFileSignedAndVerified","imageFile.maliciousClassificationType","productType","children","parentProcess","ownerMachine","calculatedUser","imageFile","imageFile.sha1String","imageFile.md5String","imageFile.companyName","imageFile.productName","iconBase64","ransomwareAutoRemediationSuspended","executionPrevented","isWhiteListClassification","matchedWhiteListRuleIds"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))