Find Actions on a Target
Use the API to find execution of specific attacks on a given target.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
In this topic:
Kovter and Poweliks Detection
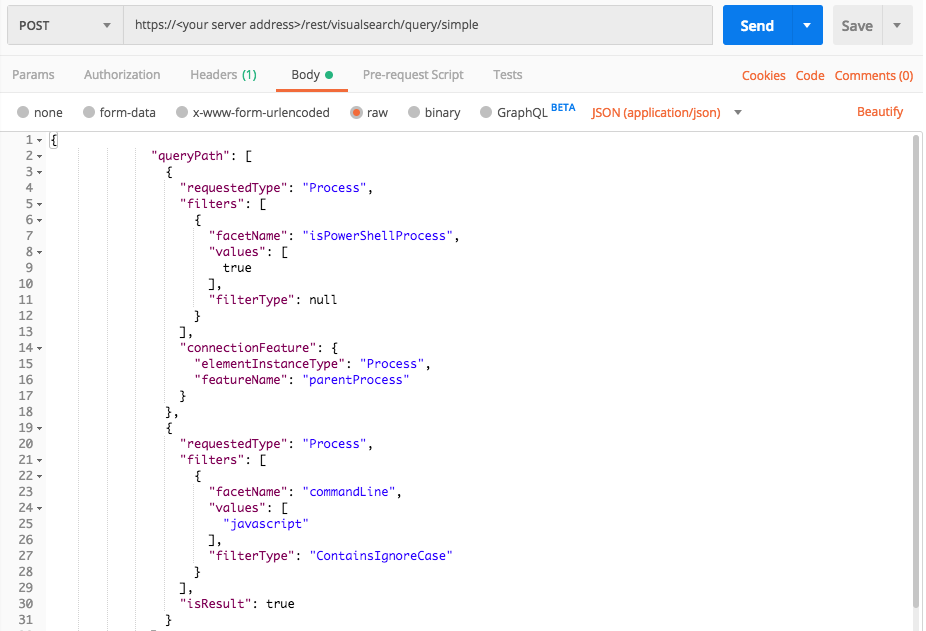
Use this request to search for processes with JavaScript in the command line, running Powershell and Windows processes with injected code
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "isPowerShellProcess",
"values": [
true
],
"filterType": null
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "parentProcess"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLine",
"values": [
"javascript"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"parentProcess",
"hasSuspicions",
"creationTime",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"endTime"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"923810613.-3599489590504944098": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1506331710323"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1506331798071"
]
},
"hasSuspicions": {
"totalValues": 1,
"values": [
"false"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
}
},
"elementValues": {
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "923810613.-3086126652240771255",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "923810613.-3599489590504944098",
"groupByValue": "powershell.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "923810613.-3599489590504944098",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {},
"evidenceMap": {},
"totalPossibleResults": 3,
"queryLimits": {
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "parentProcess"
},
"count": 3
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "isPowerShellProcess",
"values": [
true
],
"filterType": null
}
],
"connectionFeature": {
"elementInstanceType": "Process",
"featureName": "parentProcess"
}
},
{
"requestedType": "Process",
"filters": [
{
"facetName": "commandLine",
"values": [
"javascript"
],
"filterType": "ContainsIgnoreCase"
}
],
"isResult": true
}
],
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"parentProcess",
"hasSuspicions",
"creationTime",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"endTime"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"923810613.-3599489590504944098": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1506331710323"
]
},
"endTime": {
"totalValues": 1,
"values": [
"1506331798071"
]
},
"hasSuspicions": {
"totalValues": 1,
"values": [
"false"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"powershell.exe"
]
}
},
"elementValues": {
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "923810613.-3086126652240771255",
"name": "cmd.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "923810613.-3599489590504944098",
"groupByValue": "powershell.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "923810613.-3599489590504944098",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {},
"evidenceMap": {},
"totalPossibleResults": 3,
"queryLimits": {
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 3
},
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": "parentProcess"
},
"count": 3
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter = "isPowerShellProcess"
linking_element = "Process"
linking_feature = "parentProcess"
query_element_2 = "Process"
query_element_2_filter = "commandLine"
query_element_2_filter_value = "javascript"
query = json.dumps({"queryPath":[{"requestedType":query_element_1,"filters":[{"facetName":query_element_1_filter,"values":[True],"filterType":"Equals"}],"connectionFeature":{"elementInstanceType":linking_element,"featureName":linking_feature}},{"requestedType":query_element_2,"filters":[{"facetName":query_element_2_filter,"values":[query_element_2_filter_value],"filterType":"ContainsIgnoreCase"}],"isResult":True}],"totalResultLimit":100,"perGroupLimit":10,"perFeatureLimit":10,"templateContext":"SPECIFIC","queryTimeout":120000,"customFields":["elementDisplayName","parentProcess","hasSuspicions","creationTime","ransomwareAutoRemediationSuspended","executionPrevented","endTime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "923810613.-3599489590504944098": { "simpleValues": { "creationTime": { "totalValues": 1, "values": [ "1506331710323" ] }, "endTime": { "totalValues": 1, "values": [ "1506331798071" ] }, "hasSuspicions": { "totalValues": 1, "values": [ "false" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "powershell.exe" ] } }, "elementValues": { "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "923810613.-3086126652240771255", "name": "cmd.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": {}, "filterData": { "sortInGroupValue": "923810613.-3599489590504944098", "groupByValue": "powershell.exe" }, "isMalicious": false, "suspicionCount": 0, "guidString": "923810613.-3599489590504944098", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": {}, "evidenceMap": {}, "totalPossibleResults": 3, "queryLimits": { "totalResultLimit": 100, "perGroupLimit": 10, "perFeatureLimit": 10, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 3 }, { "featureDescriptor": { "elementInstanceType": "Process", "featureName": "parentProcess" }, "count": 3 } ] }, "status": "SUCCESS", "message": "" }
Injected by a browser
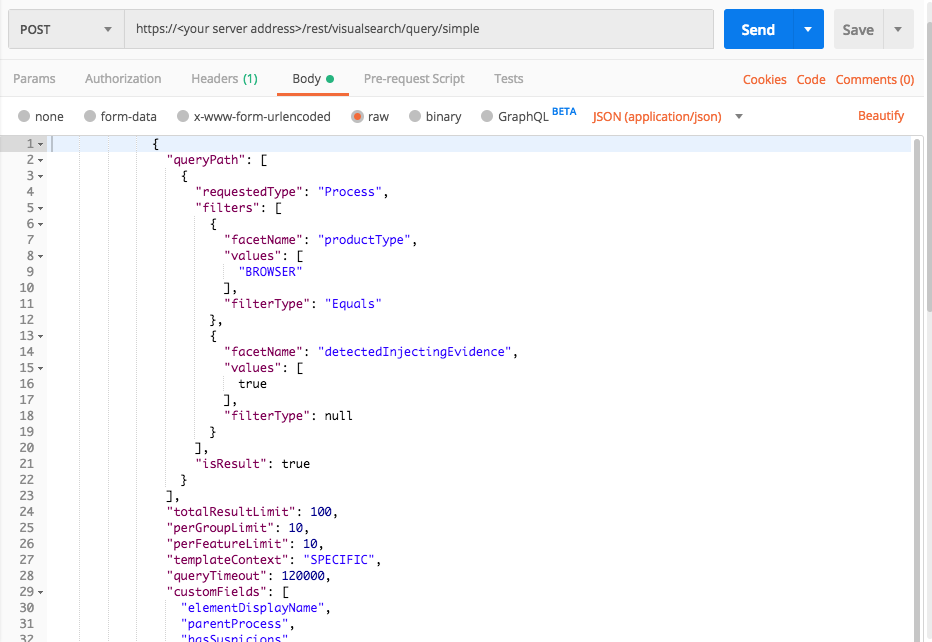
Use this request to find processes injected by a browser. Since browsers often inject into legitimate computer processes, you should review the result set for this query and filter out legitimate items.
Request
curl --request POST \
--url https://12.34.56.78/rest/visualsearch/query/simple \
--header 'Content-Type: application/json' \
--data '{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"BROWSER"
],
"filterType": "Equals"
},
{
"facetName": "detectedInjectingEvidence",
"values": [
true
],
"filterType": null
}
],
"isResult": true
}
],
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"parentProcess",
"hasSuspicions",
"creationTime",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"endTime"
]
}'
Response
{
"data": {
"resultIdToElementDataMap": {
"1464859087.-8196079988746161145": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1522651245051"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"hasSuspicions": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"chrome.exe"
]
}
},
"elementValues": {
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "1464859087.6965238414721080829",
"name": "explorer.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "1464859087.-8196079988746161145",
"groupByValue": "chrome.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "1464859087.-8196079988746161145",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {},
"evidenceMap": {},
"totalPossibleResults": 2,
"queryLimits": {
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 2
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{
"queryPath": [
{
"requestedType": "Process",
"filters": [
{
"facetName": "productType",
"values": [
"BROWSER"
],
"filterType": "Equals"
},
{
"facetName": "detectedInjectingEvidence",
"values": [
true
],
"filterType": "Equals"
}
],
"isResult": true
}
],
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"templateContext": "SPECIFIC",
"queryTimeout": 120000,
"customFields": [
"elementDisplayName",
"parentProcess",
"hasSuspicions",
"creationTime",
"ransomwareAutoRemediationSuspended",
"executionPrevented",
"endTime"
]
}
Response
{
"data": {
"resultIdToElementDataMap": {
"1464859087.-8196079988746161145": {
"simpleValues": {
"creationTime": {
"totalValues": 1,
"values": [
"1522651245051"
]
},
"executionPrevented": {
"totalValues": 1,
"values": [
"false"
]
},
"hasSuspicions": {
"totalValues": 1,
"values": [
"false"
]
},
"elementDisplayName": {
"totalValues": 1,
"values": [
"chrome.exe"
]
}
},
"elementValues": {
"parentProcess": {
"totalValues": 1,
"elementValues": [
{
"elementType": "Process",
"guid": "1464859087.6965238414721080829",
"name": "explorer.exe",
"hasSuspicions": false,
"hasMalops": false
}
],
"totalSuspicious": 0,
"totalMalicious": 0
}
},
"suspicions": {},
"filterData": {
"sortInGroupValue": "1464859087.-8196079988746161145",
"groupByValue": "chrome.exe"
},
"isMalicious": false,
"suspicionCount": 0,
"guidString": "1464859087.-8196079988746161145",
"labelsIds": null,
"malopPriority": null
}
},
"suspicionsMap": {},
"evidenceMap": {},
"totalPossibleResults": 2,
"queryLimits": {
"totalResultLimit": 100,
"perGroupLimit": 10,
"perFeatureLimit": 10,
"groupingFeature": {
"elementInstanceType": "Process",
"featureName": "imageFileHash"
},
"sortInGroupFeature": null
},
"queryTerminated": false,
"pathResultCounts": [
{
"featureDescriptor": {
"elementInstanceType": "Process",
"featureName": null
},
"count": 2
}
]
},
"status": "SUCCESS",
"message": ""
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username = "[email protected]"
password = "nKnAJmBSF0i9"
server = "workshop.cybereason.net"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
login_response = session.post(login_url, data=data, verify=True)
print (login_response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/visualsearch/query/simple"
api_url = base_url + endpoint_url
# These are the variables that represent different fields in the request.
query_element_1 = "Process"
query_element_1_filter_1 = "productType"
query_element_1_filter_1_value = "BROWSER"
query_element_1_filter_2 = "detectedInjectingEvidence"
query = json.dumps({"queryPath":[{"requestedType":"Process","filters":[{"facetName":query_element_1_filter_1,"values":[query_element_1_filter_1_value],"filterType":"Equals"},{"facetName":query_element_1_filter_2,"values":[True],"filterType":"Equals"}],"isResult":True}],"totalResultLimit":100,"perGroupLimit":10,"perFeatureLimit":10,"templateContext":"SPECIFIC","queryTimeout": 120000,"customFields":["elementDisplayName","parentProcess","hasSuspicions","creationTime","ransomwareAutoRemediationSuspended","executionPrevented","endTime"]})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{ "data": { "resultIdToElementDataMap": { "1464859087.-8196079988746161145": { "simpleValues": { "creationTime": { "totalValues": 1, "values": [ "1522651245051" ] }, "executionPrevented": { "totalValues": 1, "values": [ "false" ] }, "hasSuspicions": { "totalValues": 1, "values": [ "false" ] }, "elementDisplayName": { "totalValues": 1, "values": [ "chrome.exe" ] } }, "elementValues": { "parentProcess": { "totalValues": 1, "elementValues": [ { "elementType": "Process", "guid": "1464859087.6965238414721080829", "name": "explorer.exe", "hasSuspicions": false, "hasMalops": false } ], "totalSuspicious": 0, "totalMalicious": 0 } }, "suspicions": {}, "filterData": { "sortInGroupValue": "1464859087.-8196079988746161145", "groupByValue": "chrome.exe" }, "isMalicious": false, "suspicionCount": 0, "guidString": "1464859087.-8196079988746161145", "labelsIds": null, "malopPriority": null } }, "suspicionsMap": {}, "evidenceMap": {}, "totalPossibleResults": 2, "queryLimits": { "totalResultLimit": 100, "perGroupLimit": 10, "perFeatureLimit": 10, "groupingFeature": { "elementInstanceType": "Process", "featureName": "imageFileHash" }, "sortInGroupFeature": null }, "queryTerminated": false, "pathResultCounts": [ { "featureDescriptor": { "elementInstanceType": "Process", "featureName": null }, "count": 2 } ] }, "status": "SUCCESS", "message": "" }